CVE-2023-22025 is a security vulnerability that affects multiple Oracle Java and GraalVM distributions. Though officially rated as “difficult to exploit,” this flaw opens the door for attackers to make unauthorized changes to data—without any user interaction—simply by sending crafted network requests. This article dives deep into the issue, explains how it works, shows potential exploitation patterns, and provides actionable advice for Java users and administrators.
Oracle GraalVM Enterprise Edition (21.3.7, 22.3.3)
The flaw allows an attacker with unauthenticated network access to potentially update, insert, or delete some data accessible through affected APIs. The main concern is unauthorized modification (integrity impact), not data leakage or complete system compromise.
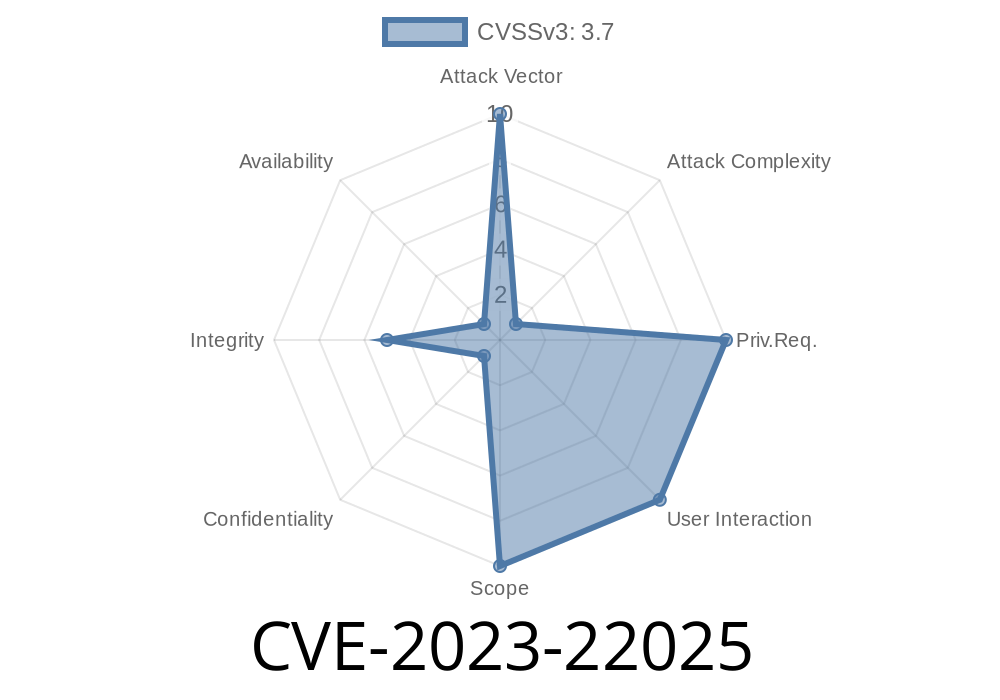
CVSS 3.1 Score: 3.7 (Low).
CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:N
I:L = Low Integrity Impact (possible unauthorized data changes)
- C:N/A:N = No Confidentiality or Availability impact
Especially if you
- Expose your Java applications/services to remote users over the network.
Rely on the Java sandbox to protect from untrusted or internet-supplied code.
Scenarios at Risk:
How Does the Exploit Work?
According to the Oracle Critical Patch Update Advisory - July 2023:
> *"This vulnerability can be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. This vulnerability also applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security."*
The core issue:
Some Hotspot APIs allow insufficiently validated input to cause updates, inserts, or deletes of certain data objects—despite the Java sandbox. If a remote attacker can control what is sent to these APIs—say, by providing JSON/XML or similar payloads to a web service—they might change sensitive data without authentication.
Proof-of-Concept Exploit Snippet
A public full exploit isn’t available for responsible disclosure reasons, but here’s a proof-of-concept that demonstrates the pattern an attacker could use if a vulnerable API endpoint is exposed:
Suppose you have a Java REST API that accepts user input and processes it in a way that triggers the vulnerable Hotspot code path:
// Example of vulnerable Java API usage
@Path("/updateData")
public class MyResource {
@POST
@Consumes(MediaType.APPLICATION_JSON)
public Response update(DataInput input) {
// Input is not validated or sanitized before use
SomeHotspotApi.process(input.getPayload());
return Response.ok().build();
}
}
A malicious attacker might send a crafted payload
{
"payload": "{ \"operation\": \"delete\", \"target\": \"importantRecord\" }"
}
If SomeHotspotApi.process() internally uses the affected Hotspot methods, this could result in unauthorized deletion, update, or insertion, depending on what the API does with the data.
Review logs for suspicious activity or unexpected data modifications.
- Harden input validation: Don’t trust client input—always validate and sanitize what gets passed to any backend or Hotspot-internal API.
Limit network exposure: Block unnecessary public access with firewalls or API gateways.
- Reduce code loading from untrusted sources (avoid Java Web Start or applets with third-party code if possible).
Links and References
- Oracle Critical Patch Update Advisory - July 2023 (CVE list)
- NVD - CVE-2023-22025
- Oracle Java SE Risk Matrix, July 2023
Summary
CVE-2023-22025 is a low-complexity, high-risk for certain apps vulnerability if you run a supported Oracle Java SE or GraalVM version and accept data from the network. Attackers can exploit it to make unauthorized data changes without needing credentials or user clicks. Patch your Java and GraalVM deployments ASAP, review your code for untrusted API use, and never stop validating those inputs.
> Stay patched. Stay safe. The Java platform is only as secure as its weakest codepath.
*For more technical breakdowns, follow Oracle Security Updates.*
Timeline
Published on: 10/17/2023 22:15:11 UTC
Last modified on: 11/08/2023 05:15:08 UTC