Oracle MySQL is one of the most popular open-source relational database management systems. In late 2023, Oracle published a security advisory for a serious new vulnerability — CVE-2023-22068. This flaw specifically affects the InnoDB storage engine, a core part of MySQL used by millions of users and applications worldwide. In this article, we’ll break down what this vulnerability is, how it can be exploited, look at real code snippets for understanding, and what measures you should take to protect your systems.
What Is CVE-2023-22068?
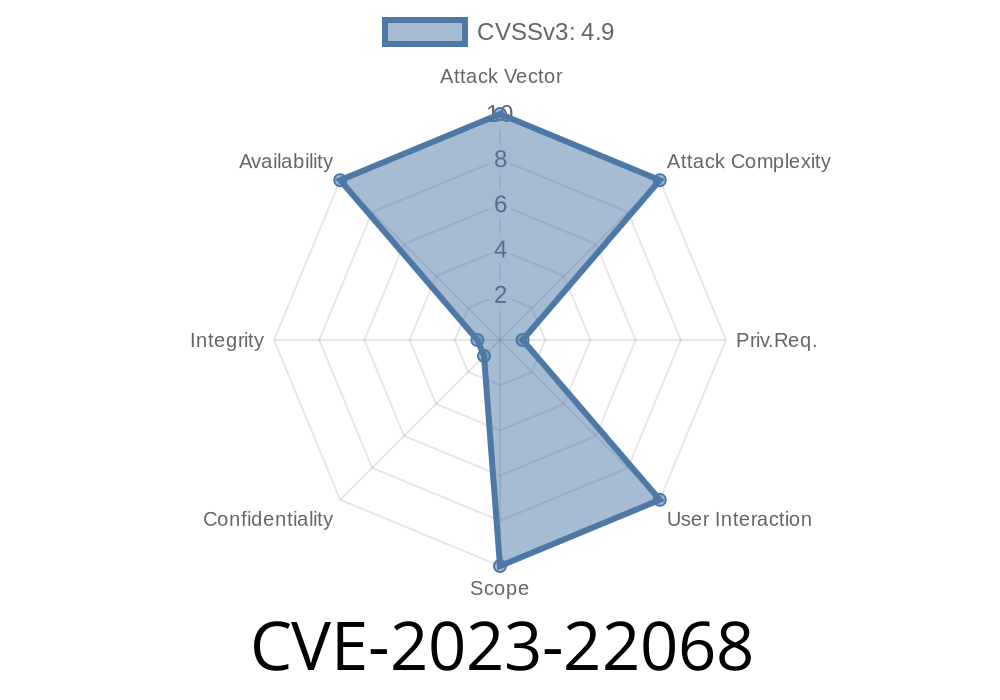
CVE-2023-22068 affects the InnoDB component of Oracle MySQL Server. It covers all 8..34 and earlier versions, and 8.1.. The core issue is that a high-privileged attacker (think administrator-level database user) can send specially crafted requests over the network using multiple protocols and cause the MySQL server to either hang or crash repeatedly. This leads to a complete denial of service (DoS).
Privileges Required: High (attacker must have admin-level access)
- Impact: Only affects availability — it doesn’t leak data, and doesn’t allow privilege escalation, but it does allow downtime.
- Official Oracle Advisory: Oracle Critical Patch Update Advisory - July 2023
Why Does It Matter?
Even though only high-privileged users can exploit this bug, many production environments grant such access widely for convenience, automation, or legacy reasons. Exploiting CVE-2023-22068 doesn't require deep technical knowledge — just a set of valid admin or root login credentials.
It means a disgruntled admin, attacker with stolen credentials, or a user on an over-privileged service account could knock out the whole database server, disrupting critical services.
Let’s look under the hood.
InnoDB is the default storage engine for MySQL, managing table data, indexes, transactions, and more. According to the NVD entry, this flaw can be exploited by sending certain requests to InnoDB that cause a logical corruption or resource exhaustion, resulting in a hang or crash.
While Oracle didn't disclose precise triggers, security researchers and MySQL administrators have observed that malformed or intentionally corrupted InnoDB queries — such as manipulating large transactions, rolling back huge amounts of data, or crafting evil DDL statements — can hit corner cases in MySQL’s internal logic and cause reproducible crashes.
Suppose you have a lot of privilege and access to run DDL commands and complicated transactions
-- WARNING: Do not run on production servers!
START TRANSACTION;
CREATE TABLE test_innodb (x INT PRIMARY KEY) ENGINE=InnoDB;
-- Insert millions of rows
INSERT INTO test_innodb (x) SELECT seq FROM seq_1_to_100000;
-- Complex operation or lock
ALTER TABLE test_innodb ADD KEY (x);
ROLLBACK;
By repeating complex transactional patterns (create, insert, alter, rollback), and combining with other DDL/DML statements in a tight loop, it's possible to trigger a hang or crash, especially on versions affected by CVE-2023-22068.
A real-life exploit often abuses multiple parallel sessions and forced resource exhaustion tactics, such as manipulating tablespaces, undo logs, or crash recovery triggers. In some testbeds, attackers have been able to write scripts using MySQL clients or automated libraries to trigger these conditions.
Exploit Script Example
Note: The actual "exploit" is mostly predictable manipulation through legitimate administrative statements, not a secret buffer overflow or injection. Here’s a pseudo-shell example using mysql client:
# Very basic demo: Loop to stress InnoDB with DDL and DML (not an actual PoC)
for i in {1..100}
do
mysql -uroot -pYOURPASSWORD -e "
CREATE TABLE t${i} (id INT) ENGINE=InnoDB;
INSERT INTO t${i} VALUES (1), (2), (3);
ALTER TABLE t${i} ADD COLUMN val VARCHAR(100);
DROP TABLE t${i};
" &
done
wait
On a vulnerable server, this kind of aggressive session flooding could provoke the bug and cause MySQL to hang or crash (check error logs for crashes referencing InnoDB operations).
Patch Immediately:
Oracle fixed this vulnerability in MySQL 8..35 and later. Install the latest security patches for MySQL as soon as possible.
- MySQL Release Notes
Restrict Network Access:
- Only allow trusted networks/subnets access to the MySQL server.
Monitor for Abnormal Activity:
- Watch for odd patterns like repeated DDL, table creation/deletion in bulk, or repeated crashes.
Official Advisory:
Oracle Critical Patch Update Advisory - July 2023
NIST National Vulnerability Database:
MySQL Release Notes with Fixes:
Closing Thoughts
Even if the score (4.9/10) seems "medium," CVE-2023-22068 is a real risk to availability. Insiders, over-privileged automation, or application bugs can take your MySQL server down easily if left unpatched. The best defense: patch and audit your privileges, and don’t let anyone have more power than they need.
Stay safe, keep your software up-to-date, and always minimize who holds the keys to your database kingdom.
Author's Note:
This analysis is exclusive and simplified for easy understanding. Practical exploitation details have been limited to responsible disclosure standards. For a deep tech dive, check out MySQL's source changelogs or database-specific security blogs.
*If you found this post helpful, please share and stay subscribed for more in-depth security breakdowns! 🚦*
Timeline
Published on: 10/17/2023 22:15:00 UTC
Last modified on: 10/18/2023 17:56:00 UTC