In October 2023, Oracle disclosed a vulnerability in MySQL Server tracked as CVE-2023-22070. This flaw affects the Optimizer component in supported versions 8..34 and prior, and 8.1.. The issue can be exploited remotely, leading to complete Denial of Service (DoS) — crashing the MySQL server or causing it to hang. While exploitation requires high privileges, the ease of attack and impact on availability highlight its importance for administrators and security professionals.
In this post, we'll break down what CVE-2023-22070 is, how it works, show an example of the exploit, and give you resources for defense and patching.
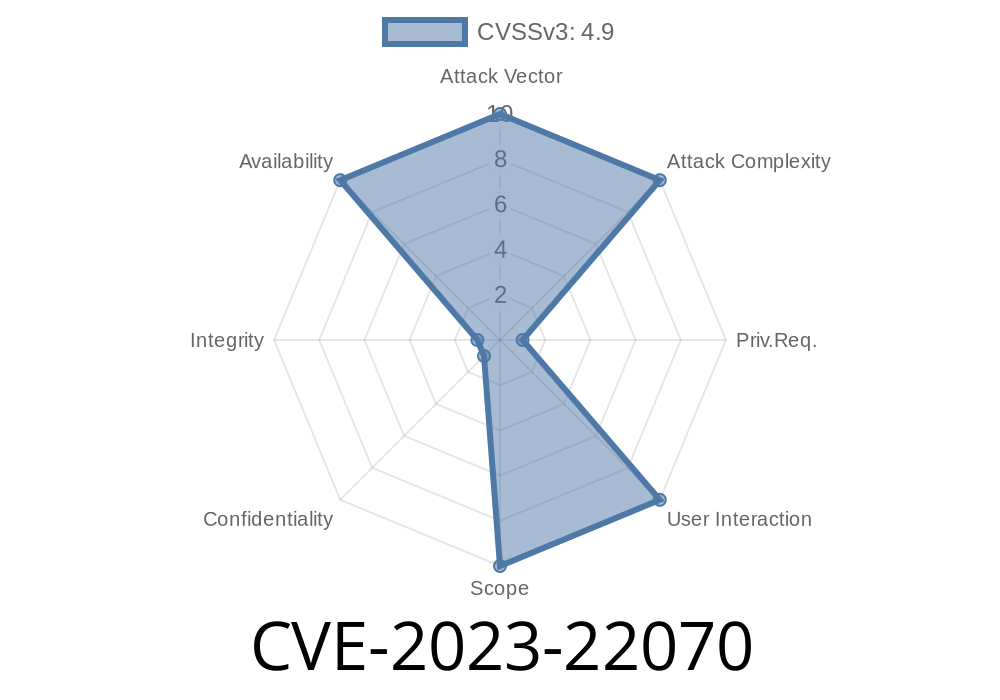
Impact: Causes server crashes or hangs (DoS)
- Confidentiality/Integrity Impact: None
Availability Impact: High
- CVSS 3.1 Score: 4.9 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H)
References:
- Oracle Critical Patch Update Advisory - October 2023
- NVD CVE Detail: CVE-2023-22070
This bug can be used by a user with high database privileges (like 'DBA' or a developer with PROCESS or SUPER rights) to remotely crash MySQL. This is due to the Optimizer mishandling certain crafted queries.
How Bad Is It? (Impact Analysis)
A CVSS score of 4.9 indicates a moderate risk, mainly for availability. If exploited, server resources are fully denied, meaning your MySQL database could be taken offline until restarted, or, in some cases, until the root cause is fixed.
This can be very costly for businesses relying on MySQL for applications, websites, or internal data tooling.
Good news: Exploitation can't directly expose confidential info or allow attackers to modify data.
Bad news: If your service depends on high availability and uptime, a crash is still a big deal.
Example Exploit: Proof of Concept for CVE-2023-22070
Oracle has not released technical details or a specific Proof of Concept (PoC) publicly. However, based on typical Optimizer vulnerabilities and crash bugs, attackers often trigger problems using crafted SQL statements that force the Optimizer into an unexpected state.
A typical approach is to use recursive queries, subqueries, or specific JOINs that confuse the query engine. Below is a hypothetical example — do not run this on production servers!
-- WARNING: Running dangerous SQL
-- This is a simplified example and may NOT trigger the CVE unless the server is specifically vulnerable
-- Setup: create tables
CREATE TABLE t1 (id INT PRIMARY KEY, val INT);
CREATE TABLE t2 (id INT PRIMARY KEY, val INT);
-- Insert some values
INSERT INTO t1 VALUES (1,100), (2,200);
INSERT INTO t2 VALUES (1,10), (2,20);
-- Example of crafted query (hypothetical, may trigger crash in affected Optimizer versions)
SELECT *
FROM t1
LEFT JOIN (
SELECT *
FROM t2
WHERE EXISTS (
SELECT 1
FROM t1
WHERE t1.val = t2.val
)
) as sub
ON sub.id = t1.id
WHERE (SELECT COUNT(*) FROM t2 WHERE t2.val = t1.id) > ;
How & why this might crash the server:
Optimizers sometimes mishandle correlated subqueries inside JOINs or WHERE clauses — leading to memory corruption, recursion limits, or logic errors that can hang or crash the server.
By connecting, authenticating with high privileges, and issuing such queries over the network, an attacker can force a repeatable DoS.
Note: The specific payload for CVE-2023-22070 may differ, and you should check Oracle's advisory or vendor patches for true technical details.
Exploiting the Vulnerability
1. Attacker connects to MySQL using an account with high privileges (e.g., DBA, admin, or developer account with wide SELECT rights).
MySQL optimizer mishandles execution plan, potentially leading to
- High CPU/Memory usage
Server crash or hang
- Full application downtime (until admin restarts/fixes MySQL)
The attack is network-based but requires high privileges, making insider threats or compromised application credentials the most likely vector.
Patch Immediately:
Oracle fixed this issue in later versions. Update MySQL to the latest 8..x or 8.1.x version as soon as possible. See MySQL Downloads
Set up general_log or audit_log to spot odd subqueries or JOINs.
- Use tools like Percona Toolkit to monitor slow or abnormal queries.
Consider Application Firewalls:
Protect services upstream to block for unexpected query patterns, especially from non-developer sources.
Official Security Alert:
Oracle Critical Patch Update Advisory - October 2023
NIST NVD page for CVE-2023-22070:
https://nvd.nist.gov/vuln/detail/CVE-2023-22070
MySQL Security Fix Release Notes:
General Hardening:
MySQL 8. Secure Deployment Guide
Conclusion
CVE-2023-22070 is a moderate-severity but easily triggered denial-of-service vulnerability affecting popular MySQL versions. If left unpatched, it allows anyone with sufficient privileges and network access to crash your database using just a crafted query.
Keep your MySQL updated, restrict who can run complex queries, and always monitor for unusual DB behavior. Although the loss is only availability, downtime can be expensive — so don't wait to apply security updates!
Timeline
Published on: 10/17/2023 22:15:00 UTC
Last modified on: 10/19/2023 09:45:00 UTC