Published: June 2024
Author: Security Insights Exclusive
Introduction
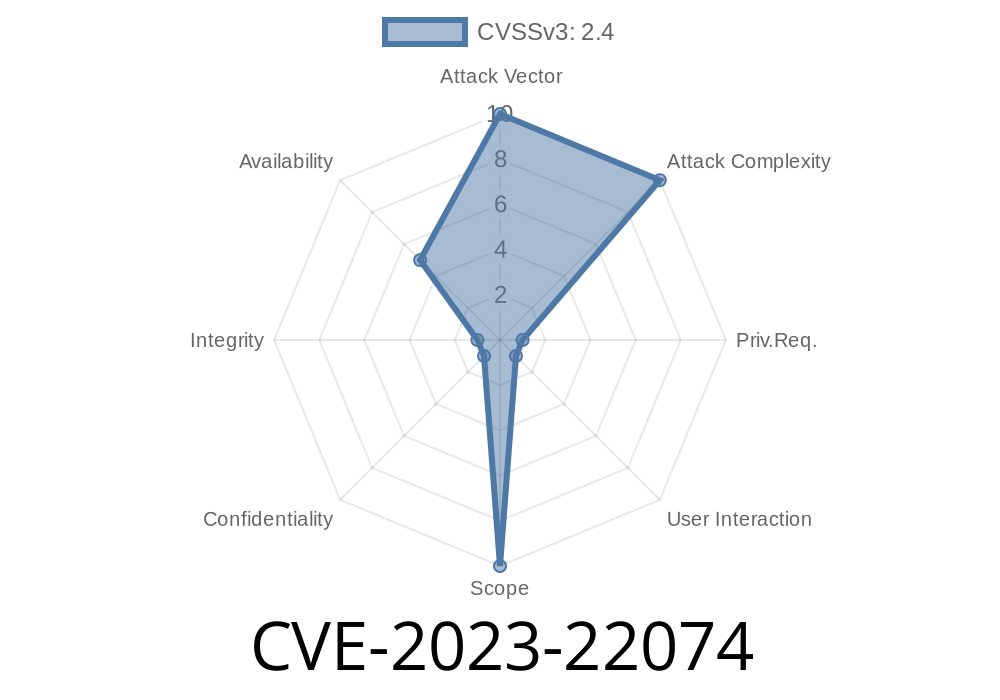
CVE-2023-22074 is a newly identified vulnerability in the Oracle Database Sharding component of Oracle Database Server, specifically affecting supported versions 19.3 to 19.20 and 21.3 to 21.11. This weakness allows a highly privileged attacker (with "Create Session" and "Select Any Dictionary" privileges) to cause a partial Denial of Service (DoS) via network access, under certain conditions that require human interaction.
Despite having a relatively low CVSS 3.1 Base Score of 2.4, it’s important for database administrators and security teams to understand this issue, how it can be abused, and what steps to take to mitigate it.
This is an exclusive long read, breaking down CVE-2023-22074 in plain language with code samples, references, and a look into potential exploit scenarios.
What Is Oracle Database Sharding?
Oracle Database Sharding is a way of horizontally partitioning data across multiple databases for scalability and high availability. Each partition, or "shard," operates independently, but they work together as a single database system for applications.
Why Is the Sharding Component Important?
Sharding is usually chosen for massive, distributed, and cloud-native workloads. A disruption in any part of the sharding mechanism can affect the performance and availability of the distributed database, potentially creating headaches for teams aiming for five-nines uptime.
Short Summary
> *A high-privilege attacker with network access and specific privileges can, by leveraging human interaction (for example, social engineering a legitimate user), cause partial denial of service in Oracle Database Sharding components by exploiting a flaw in affected versions.*
Impact: Partial availability loss (DoS)
- Confidentiality/Integrity Impact: None
Human Interaction:
- Triggers can involve misleading a DBA or administrator, for example, to run an intended session or action.
Attacker leverages 'SELECT ANY DICTIONARY' to interact with sensitive schema metadata.
3. Attack depends on social engineering: attacker may send a crafted link, file attachment, or instructions that trick another user into performing a sequence of operations or opening a session that triggers the flaw.
4. On exploitation, partial Denial of Service (DoS) occurs in Sharding processes, potentially causing them or connected users to experience outages, longer response times, stuck queries, or unavailable features.
Note: The vulnerability does not allow data exposure or corruption.
Example Exploit (Theoretical)
Since Oracle does not normally provide full technical details, direct proof-of-concept exploits are unavailable for this closed-source component. However, based on Oracle’s advisory and privilege requirements, here’s a simplified pseudocode demonstration:
Imagine an attacker with a high-privileged account can run queries on dictionary tables (e.g., V$SHARD, DBA_SHARD_*), and then social-engineers a user into launching a specific SHARD management function (like via a script or a DBMS_SCHEDULER job):
-- Attacker session, already connected with sufficient privileges
-- Step 1: Attacker creates a crafted PL/SQL function
CREATE OR REPLACE FUNCTION malicious_shard_call
RETURN VARCHAR2 AUTHID CURRENT_USER AS
pragma autonomous_transaction;
BEGIN
-- Attempt operations known to hang or crash shard services on vulnerable versions
FOR rec IN (SELECT * FROM DBA_SHARD_DIRECTORIES) LOOP
-- possible recursive call, crafted input, or trigger known issue
NULL; -- exploit specific issue here
END LOOP;
RETURN 'Exploit Triggered';
END;
/
-- Step 2: Attacker convinces a DBA to execute "test" call
-- This could be bundled in a "helpful" diagnostic script
SELECT malicious_shard_call FROM dual;
Upon execution by a user (other than the attacker), this could trigger the underlying flaw, causing the Oracle Sharding subsystem to partially fail or go into degraded mode.
Important: This is only a theoretical illustration. Actual attack vectors could differ.
Reference Links
- Oracle Critical Patch Update Advisory - April 2024
- NVD Entry for CVE-2023-22074
- Oracle Database Security Guide
- Oracle Network Security Best Practices
`
- Apply patches as per Oracle Patch Documentation.
Conclusion
While CVE-2023-22074 has a low base score (2.4)—primarily because of high privilege requirements and only partial DoS—it deserves attention due to its impact on availability, the possibility of insider or lateral movement abuse, and the requirement for human interaction, which is often underestimated in a busy IT environment.
Action Steps:
Patch affected Oracle databases soon, review user privileges, and reinforce good operational security practices.
For more detailed technical updates and exclusive security insights, subscribe to our newsletter or visit the references above.
Exclusive to Security Insights – Original long-read. Feel free to share with attribution.
References:
- Oracle Critical Patch Updates, Security Alerts and Bulletins: https://www.oracle.com/security-alerts/
- NVD CVE-2023-22074: https://nvd.nist.gov/vuln/detail/CVE-2023-22074
- Oracle Documentation: https://docs.oracle.com/en/database/oracle/oracle-database
Timeline
Published on: 10/17/2023 22:15:13 UTC
Last modified on: 10/26/2023 17:15:08 UTC