Oracle Database is one of the most widely used relational database systems in enterprise environments. In July 2023, Oracle published a security advisory related to a vulnerability tracked as CVE-2023-22075, affecting the Oracle Database Sharding component. This post breaks down what it is, who’s affected, how it's exploited, and how to protect your systems.
What is CVE-2023-22075?
CVE-2023-22075 is a security flaw in the Oracle Database Sharding component of the Oracle Database Server. The sharding feature allows enterprises to horizontally partition databases—improving scalability and availability. However, a flaw in its implementation means that, under certain conditions, an attacker with high privileges can cause a partial denial of service (DoS) on the sharding service.
Select Any Table
Also, exploitation requires network access via Oracle Net, and (importantly) human interaction from someone other than the attacker. This typically means the victim performs an action (possibly clicking, running a query, or another interaction), leading to the trigger of the flaw.
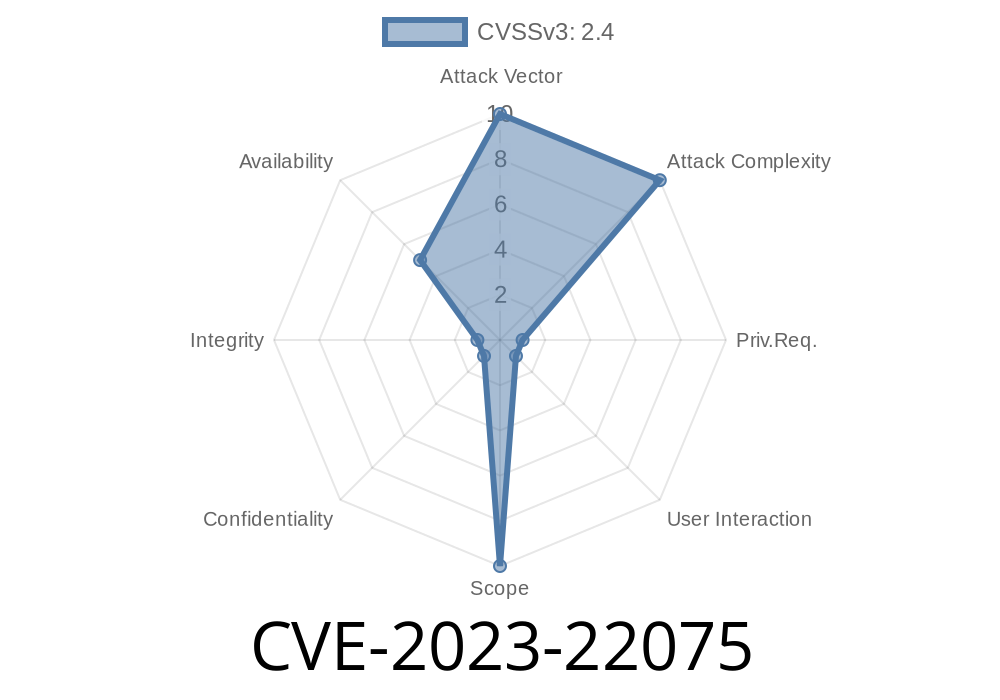
CVSS Base Score: 2.4 (Low)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:U/C:N/I:N/A:L
Exploit Details (with Code Snippet)
Here’s a conceptual demo of what exploiting this bug might look like, based on sharding system internals and Oracle's own advisory. The real exploit details are restricted, but the following snippet shows typical misuse patterns in such privileged Oracle environments.
-- Attacker creates a specially crafted VIEW in sharded DB
CREATE OR REPLACE VIEW SYSTEM.V_SHARD_ATTACK AS
SELECT * FROM SYS.DBA_SHARDING_KEY_MAP
WHERE 1=
UNION ALL
SELECT * FROM dual;
-- Victim (DBA or user) later queries the view via a legitimate administration tool or script
SELECT * FROM SYSTEM.V_SHARD_ATTACK;
-- This causes the sharding process to hang or malfunction
Explanation:
The attacker, using their privileges, creates an abnormal database VIEW that references a sensitive part of the sharding subsystem. When another DBA or user (the human victim) interacts with this view (e.g., through routine inspection or third-party app), the database gets partially denied—leading to a performance drop or unavailability in the sharding system.
> NOTE: The actual root cause may involve more complex misuse of sharding APIs, but the core exploit vector remains—a privileged user sets up a malicious database object that, when executed by someone else, disrupts the sharded architecture.
Impact of an Exploit
- Partial Denial of Service: The core outcome is limited availability for the sharding subsystem. Sharding operations (like metadata refresh, chunk migration, or health checks) may slow down, hang, or even fail transiently.
Detection
- Check for suspicious VIEWS: Audit for new or suspiciously named views, especially those owned by non-standard users or referencing system sharding tables.
- Monitor for DoS signs: Slow responses, failed sharding jobs, or unexplained spikes in resource usage on sharded nodes.
Database Auditing: Enable auditing of CREATE VIEW and SELECT ANY TABLE grants.
-- Find users with excessive privileges
SELECT grantee, privilege
FROM dba_sys_privs
WHERE privilege IN ('CREATE ANY VIEW', 'SELECT ANY TABLE');
### Mitigation/Remediation
Apply Oracle Patch:
Oracle has released patches. See the Oracle Critical Patch Update Advisory.
Educate DBAs:
Train admins and privileged users to check that objects they're accessing are what they expect, especially when suggested by or linked from other users.
References and Further Reading
- Oracle July 2023 CPU Advisory
- National Vulnerability Database CVE-2023-22075
- Oracle Database Sharding Documentation
Conclusion
Oracle Database Sharding is a powerful feature, but carries a risk if not carefully secured, especially when users have high database privileges. CVE-2023-22075 shows how an attacker can leverage privileges and trick another user into making the system less available, even with no data theft or corruption risk. Always keep your systems patched, minimize privileges, and audit your internal database activities to prevent and detect these subtle attacks.
Stay safe and always patch promptly!
*For questions or contributions, feel free to comment below or contact your Oracle Security representative.*
Timeline
Published on: 10/17/2023 22:15:13 UTC
Last modified on: 10/23/2023 18:23:12 UTC