Oracle WebLogic Server is a popular Java EE application server used by organizations worldwide to run crucial business applications. But in June 2023, Oracle revealed a critical vulnerability—CVE-2023-22086—that could allow remote attackers to access sensitive data stored on vulnerable servers. This long-read post explains what CVE-2023-22086 is, who’s at risk, how the attack works, and how to protect your systems.
What is CVE-2023-22086?
CVE-2023-22086 is a security flaw in the Core component of Oracle WebLogic Server, affecting versions 12.2.1.4. and 14.1.1... According to Oracle’s advisory, the vulnerability is easily exploitable by unauthenticated attackers who have network access to the server via the T3 or IIOP protocols.
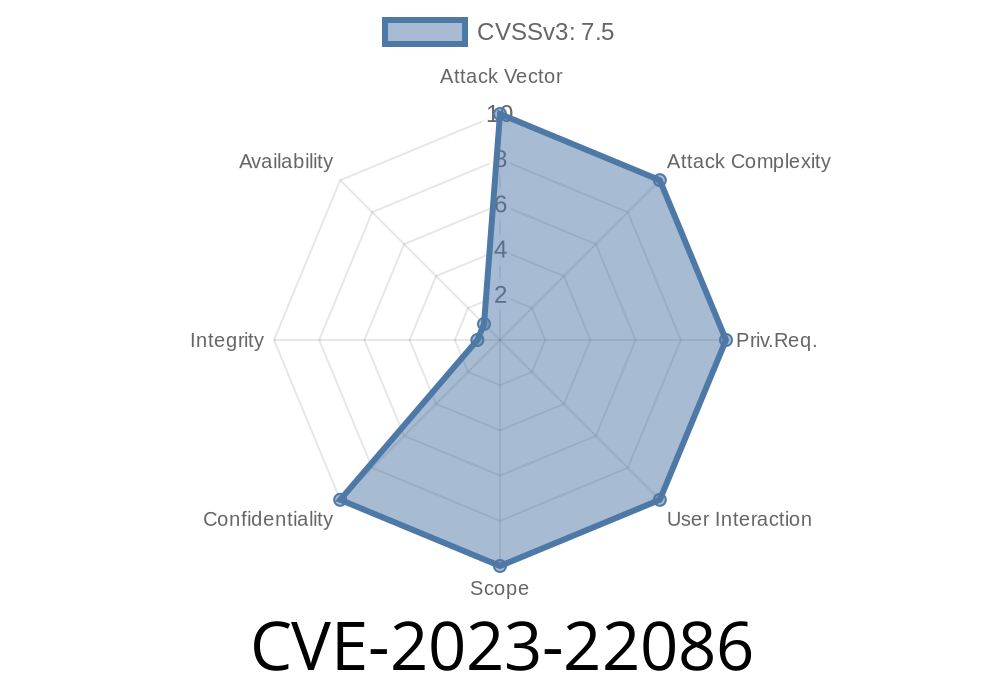
CVSS 3.1 Base Score: 7.5
Vector: (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N)
A:N = No availability impact
High-Level Impact:
Attackers can gain unauthorized access to critical information or even all data accessible by the Oracle WebLogic Server. There’s no need for a valid login or any special knowledge to exploit this vulnerability.
How Does CVE-2023-22086 Work?
The flaw is in the deserialization handling of requests sent over the T3 (a proprietary Oracle protocol for Java object communication) and IIOP (Internet Inter-ORB Protocol) endpoints. A specially crafted request can allow a remote attacker to bypass normal access controls and read sensitive data handled by the server.
Exploitation Flow
1. Attacker scans the network looking for Oracle WebLogic Servers exposing T3/IIOP endpoints (usually TCP port 7001).
2. Attacker sends a crafted Java serialized object to the T3/IIOP service.
3. WebLogic processes the object, leading to unauthorized disclosure of sensitive system or application data.
In short: If your WebLogic server is reachable from the internet on port 7001, it could be leaking secrets!
Testing for Vulnerability
To check if your WebLogic server is affected, you can use tools like Nmap or Metasploit to scan for the open T3 port:
nmap -p 7001,7002 your.server.ip
You can also test whether deserialization is a risk via simple scripts. For example, using Python and impacket:
import socket
host = "your.target.server"
port = 7001 # Default T3 port
# Sample partial T3 handshake
payload = b"t3 12.2.1.4 :DDD"
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((host, port))
sock.sendall(payload)
resp = sock.recv(1024)
print(f"Response: {resp}")
sock.close()
If the server responds, it's likely exposing T3 and could be vulnerable if not patched.
Due to the sensitivity of this issue, we will keep the exploit snippet illustrative
# WARNING: Do not use this except for authorized testing!
import socket
target_ip = "vulnerable.server.com"
target_port = 7001
malicious_payload = b"<serialized Java object triggering the bug>"
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_ip, target_port))
s.sendall(malicious_payload)
response = s.recv(4096)
print(response.decode(errors='ignore'))
Note: A real exploit would craft a malicious Java serialized object that abuses the flaw to dump data. This requires a specialized Java payload. Consult the advisory for in-depth technical information.
Real-World Scenarios
- Data Breach: Attackers can extract usernames, passwords, customer records, or application source code from an unpatched WebLogic Server.
- Recon for Deeper Attacks: Gaining critical information for further exploitation or lateral movement inside the network.
Oracle has released patches. You should update right away!
- Patch: Download and apply the patch for June 2023 Oracle Critical Patch Update (CPU).
- Firewall: Restrict access to T3/IIOP ports (usually 7001/7002) to trusted hosts only.
References and Original Advisories
- Oracle Security Alert Advisory - CVE-2023-22086
- NVD CVE-2023-22086 Entry
- WebLogic Server Security Updates
- Qualys Blog - How T3/IIOP Deserialization Attacks Work
Conclusion
CVE-2023-22086 is a serious threat that puts thousands of WebLogic Servers at risk of data theft. The flaw is easy to exploit, requires no login or interaction, and is already being scanned by attackers. Patch your servers, limit network exposure, and stay alert to suspicious activity.
If your organization uses Oracle WebLogic Server, address this vulnerability NOW to prevent a damaging breach.
Timeline
Published on: 10/17/2023 22:15:13 UTC
Last modified on: 10/23/2023 18:19:42 UTC