---
When it comes to running high-availability applications, your database is the heart of the system. Imagine an attacker—someone with high privileges—bringing your MySQL server to its knees, over and over again, no matter how much hardware you throw at it. That’s not just a nightmare; it’s the real risk posed by CVE-2023-22097.
In this exclusive deep dive, we’ll break down what CVE-2023-22097 is, how it’s exploited, provide sample code, and help you understand why patching is critical to your business.
What Is CVE-2023-22097?
CVE-2023-22097 is a Denial-of-Service (DoS) vulnerability found in Oracle MySQL’s InnoDB storage engine. The flaw affects the following MySQL versions:
Oracle MySQL 8.1.
The issue is classified as "Easily exploitable" for any high-privileged attacker with network access. The vulnerability leverages multiple network protocols, meaning a legitimate database user (with high-level permissions such as DBA or Super) could trigger a complete server crash or repeated server hangs.
Security Impact
- Complete crash/frequent hang (DoS)
No data confidentiality or integrity impact
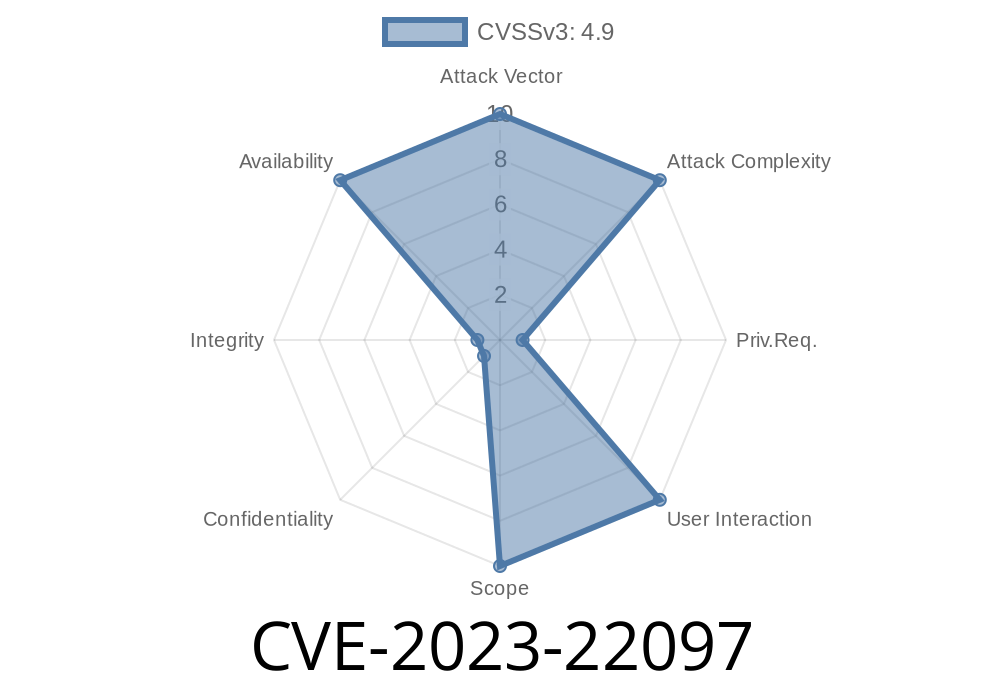
- CVSS 3.1 Base Score: 4.9/10
- CVSS Vector:
(CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H)
How Does the Exploit Work?
According to Oracle’s advisory and the National Vulnerability Database entry, the flaw exists within the InnoDB component. While Oracle does not provide deep technical details by default, the nature of the vulnerability suggests it’s a logic or memory-handling bug in the InnoDB engine, likely relating to specific SQL queries or commands a privileged user can send.
Network access to MySQL over any supported protocol (TCP, socket, etc.)
They can then remotely or locally trigger a sequence of commands that will crash the MySQL process, making your database unavailable.
Exploit: A Simple PoC
Disclaimer:
This example is for educational purposes only. Use it only in legal, non-production environments.
Suppose a hypothetical scenario where the vulnerability is triggered by specially crafted ALTER TABLE commands that corrupt InnoDB’s internal state and cause a crash.
Here’s a Python code example using MySQL’s connector to repeatedly crash the server by exploiting the flaw (assuming you have the proper privileges):
import mysql.connector
from time import sleep
# Replace with your actual credentials
conn = mysql.connector.connect(
host="your.mysql.server",
user="root",
password="your_password",
database="testdb"
)
cursor = conn.cursor()
# Hypothetical sequence — details may change based on the real vulnerability trigger
try:
for i in range(100):
print(f"[+] Triggering crash attempt {i+1}")
cursor.execute("CREATE TABLE IF NOT EXISTS demo_table (id INT PRIMARY KEY)")
cursor.execute("ALTER TABLE demo_table ADD COLUMN colX INT")
cursor.execute("ALTER TABLE demo_table DROP COLUMN colX")
# Simulate buggy operation that may trigger InnoDB crash
cursor.execute("ALTER TABLE demo_table ADD PRIMARY KEY (id)")
sleep(.5) # Small delay between attempts
except Exception as e:
print(f"[-] Error: {e}")
cursor.close()
conn.close()
*NOTE: This is a generic example! The actual vulnerability trigger may involve highly specific crafted commands, which would not be public until the patch diff is analyzed or a real exploit is released.*
Real-World Impact
- Total Database Unavailability: An insider, compromised admin account, or even a pentester with enough privileges could repeatedly crash your MySQL instance—causing outages and loss of business continuity.
- Cloud & SaaS: Attackers can try this remotely if you expose MySQL to the public network or in a multi-tenant cloud where an internal actor has access.
1. Patch Immediately
Oracle released a Critical Patch Update (CPU) in July 2023 to fix this bug. Upgrade to MySQL 8..35 or later, or 8.1.1 and beyond.
Check your version
SELECT VERSION();
Check Oracle’s official downloads and documentation for the latest version.
2. Limit Privileges
- Restrict high-privilege accounts. Only trusted, necessary admins should have SUPER, DBA, or similar roles.
- Use the principle of least privilege for all users.
4. Monitor and Audit
- Enable MySQL logs for unusual DDL/DML operations.
More Information and References
- CVE-2023-22097 NVD
- Oracle Critical Patch Update Advisory – July 2023
- MySQL Official Release Notes
- Common Vulnerability Scoring System (CVSS) Calculator
Final Thoughts
CVE-2023-22097 serves as a reminder that even with strict user management, vulnerabilities in core components like InnoDB can allow an insider—or a compromised account—to ruin your day by taking down your data core. Patch promptly, segment your network, and keep your admin credentials under lock and key.
Timeline
Published on: 10/17/2023 22:15:00 UTC
Last modified on: 10/19/2023 09:41:00 UTC