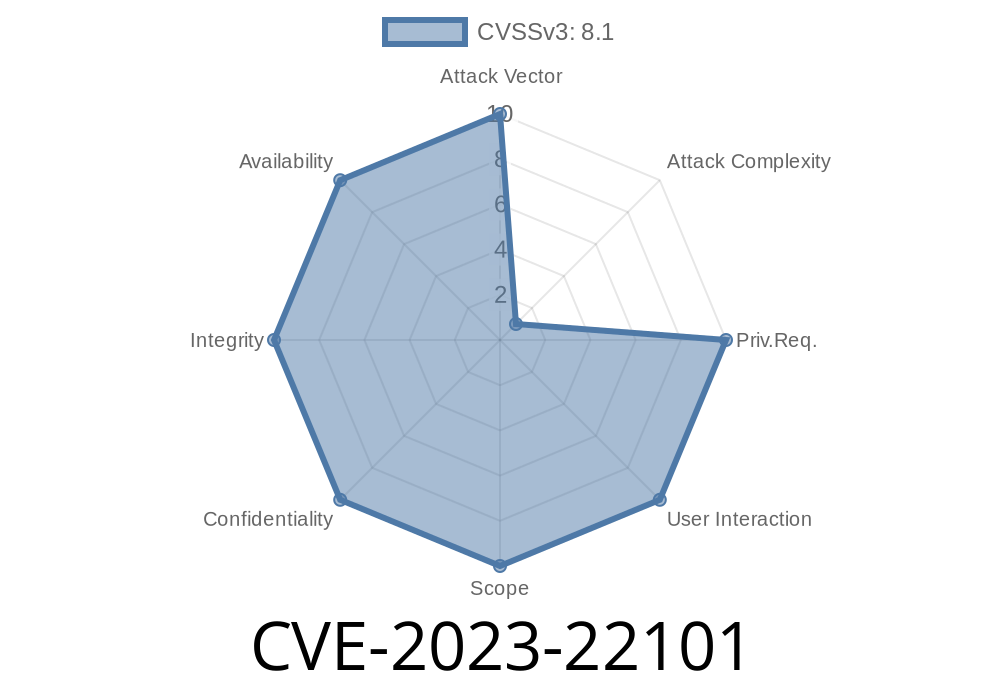
Summary:
In October 2023, Oracle published an advisory about CVE-2023-22101, a serious vulnerability in Oracle WebLogic Server, a cornerstone product for many enterprise Java applications. The flaw, which affects versions 12.2.1.4. and 14.1.1.., offers unauthenticated attackers the chance to compromise targeted servers over the network—without needing a username or password. This article explains how the vulnerability works, why it matters, and what you can do to protect your environment.
What is CVE-2023-22101?
CVE-2023-22101 is a vulnerability in the *Core* component of Oracle WebLogic Server as a part of the Fusion Middleware suite. Specifically, it allows attackers using T3 or IIOP protocols to exploit and potentially take control of an affected server.
Availability: HIGH
Use your servers to attack others.
The bug is rated highly critical because of its broad impacts on confidentiality, integrity, and availability. No authentication means even outsider attackers can succeed.
Read the official Oracle advisory here.
What's the Core Issue?
WebLogic supports several network protocols, including T3 (proprietary) and IIOP (CORBA). WebLogic servers use these for application communication. In this case, attackers can send specially crafted network traffic using T3 or IIOP—triggering software flaws in the backend and enabling remote code execution.
How Could an Attack Look in Code?
Here’s an illustrative Python snippet showing how an attacker might check if a server is vulnerable, using T3 protocol. (Note: This snippet does NOT exploit, but shows connection):
import socket
# Replace 'your.target.server' and 7001 with your target host and port
host = 'your.target.server'
port = 7001
# Basic handshake for WebLogic T3 protocol (hex representation)
t3_handshake = b't3 12.2.1\nAS:255\nHL:19\n\n'
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.settimeout(5)
s.connect((host, port))
s.sendall(t3_handshake)
response = s.recv(1024)
print('Response:', response)
If the server responds, it’s running T3 and could be vulnerable to a real exploit for CVE-2023-22101.
A real exploit would go much deeper, sending crafted serialized Java payloads that abuse deserialization or logic bugs in the Core component. These payloads could force WebLogic to execute attacker-chosen code.
Exploit Details
While no full public exploit is available (due to Oracle's coordinated disclosure process and the high risk), threat actors are known to monitor patch releases and reverse-engineer them. Exploits usually follow this path:
Craft Malicious Payload
- Use a Java tool like ysoserial to generate a serialized Java object that, when deserialized, executes code (like running a shell or dropping additional malware).
Send to Server
- Encode the payload to fit T3/IIOP format.
Payload Execution
- Server, tricked into deserializing the payload, executes arbitrary code under the WebLogic server’s privileges.
Example Reference Code (for Education):
- T3 Exploit Walkthrough (GitHub)
Download the latest CPU (Critical Patch Update) for your WebLogic version.
Restrict Network Access
- Only allow trusted IPs or networks to access T3/IIOP ports.
If you don’t need T3 or IIOP, disable these protocols in your WebLogic configuration.
Save and review server logs.
- Watch for unexpected T3/IIOP connections, especially from untrusted networks.
Keep Your Software Updated
- Regularly check Oracle’s advisory page for new vulnerabilities.
Conclusion
CVE-2023-22101 could let an outsider take over your Oracle WebLogic Server—all they need is network access, and you don’t have to do a thing wrong. The only true fix is to patch ASAP and limit who can connect to those sensitive ports.
Stay vigilant! Attackers race to exploit critical vulnerabilities as soon as patches drop.
More Reading & References
- Oracle WebLogic Security Advisories
- National Vulnerability Database Entry for CVE-2023-22101
- Oracle CPU October 2023 (Original)
- Exploit Research Example
- How to Secure T3 access (Oracle)
*If you run WebLogic, acting now is critical. Patch, restrict access, monitor, and stay informed!*
Timeline
Published on: 10/17/2023 22:15:15 UTC
Last modified on: 10/23/2023 18:19:52 UTC