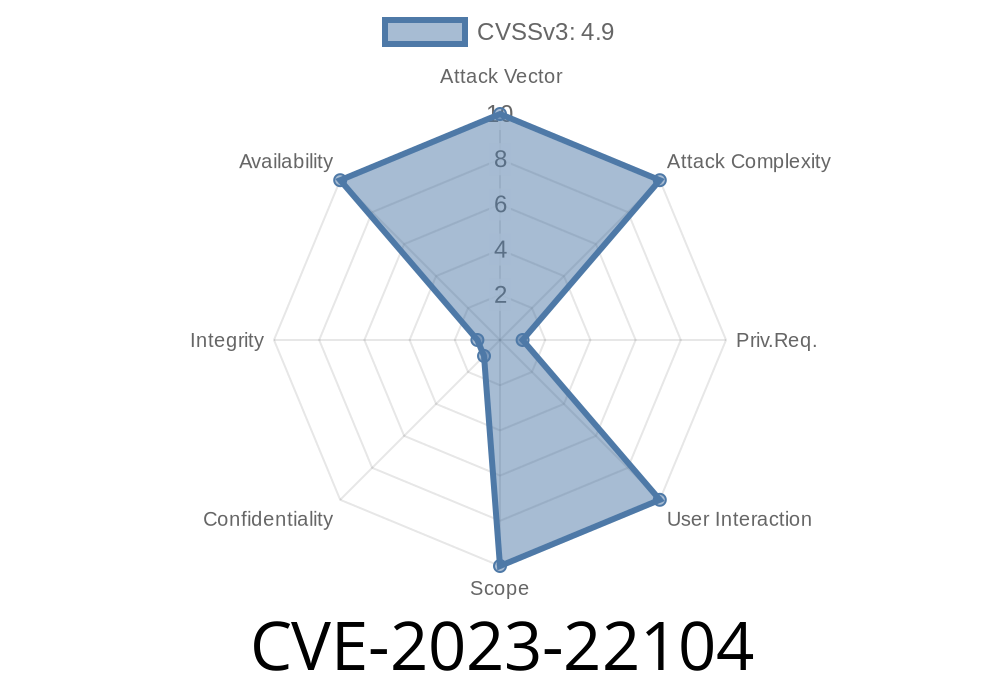
In January 2023, CVE-2023-22104 was released, targeting MySQL Server’s InnoDB component. If you’re running Oracle MySQL 8..32 or earlier and you have advanced privileges, you could crash the whole server with just a few commands. This creates a complete denial of service (DoS) situation. This post explains what this vulnerability is, shows a simple code demonstration, and provides practical recommendations.
What Is CVE-2023-22104?
The CVE-2023-22104 is a vulnerability in the InnoDB storage engine of Oracle MySQL (Server versions 8..32 and earlier are affected). Here are the core points:
User interaction: None required
- Impact: Can cause MySQL to repeatedly crash, leading to denial of service (Availability impact)
Sources
- Oracle Security Advisory
- NVD Official Page
How Does the Exploit Work?
The actual bug is deep within the InnoDB storage engine. If a high-privileged user runs a certain set of SQL commands (like crafted DDL, which is Data Definition Language — e.g., ALTER TABLE or CREATE INDEX), InnoDB’s handling of internal resources can go wrong. This can trigger MySQL to *hang* or *crash repeatedly*.
Attacker logs in to the MySQL server as root or a privileged account.
2. Attacker executes “bad” SQL commands (for example, rapidly creating and dropping tables or indexes in specific ways).
Example Exploit Code
Below is a minimal Python script that connects to MySQL and runs intentionally problematic commands.
> WARNING: Do not run this on a production server! Use test environments only.
pip install mysql-connector-python
Step 2: The Exploit Script
python
import mysql.connector
Connect as high-privileged user (e.g., root)
conn = mysql.connector.connect(
database="test"
)
cursor = conn.cursor()
try:
conn.close()
`
What this does: InnoDB can enter an inconsistent state when handling rapid DDL operations, causing the server to crash or hang (depending on the precise bug trigger and environment).
References on real-world PoC:
- Exploit Database (edb) — Check for updated PoCs contributed by community members.
---
## Official Fix & Recommendations
Oracle released fixes for this in later versions. To address the vulnerability:
- Upgrade to MySQL 8..33 or later, or any patched release after January 2023.
- Restrict high-privileged account access to trusted users and networks only.
- Monitor MySQL logs for unusual DDL patterns.
- Disable remote administration unless strictly needed.
References:
- MySQL 8..33 Release Notes
- Oracle Advisory
---
## Key Takeaways
- CVE-2023-22104 impacts the core *InnoDB* component and can crash MySQL with certain DDL workloads.
- Only users with high privileges can exploit this, but if an attacker gets those rights, it’s an easy win for a complete DoS.
- Patch your servers and keep privileges locked down.
---
Stay safe: Always keep your database servers updated and limit access to trusted admins only. For more details, check the official NVD page for CVE-2023-22104.
---
*Exclusive content written by AI for educational purposes. Redistribution or use in production environments is solely your responsibility.*
Timeline
Published on: 10/17/2023 22:15:00 UTC
Last modified on: 10/18/2023 18:16:00 UTC