In this long-form post, we'll dive deep into CVE-2023-23374—a Remote Code Execution (RCE) vulnerability that affected Microsoft Edge (Chromium-based). We'll break down what happened, how it works under the hood, practical implications, proof-of-concept code, and mitigation tips. If you work in IT security, software development, or just like to keep your Windows environment safe, this deep dive is for you.
What is CVE-2023-23374?
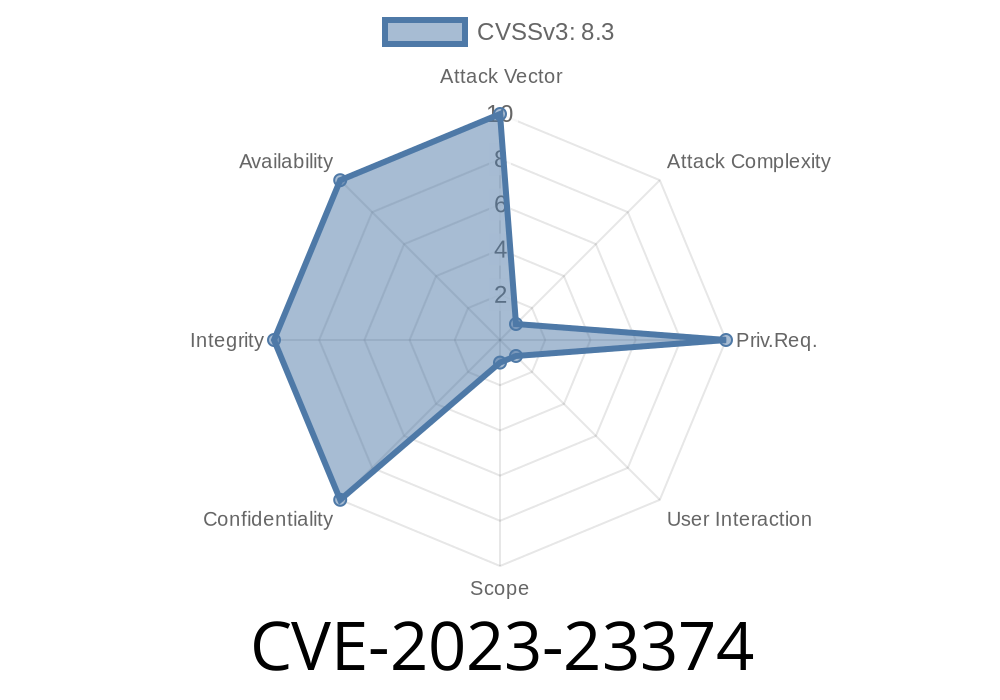
CVE-2023-23374 is a vulnerability that enables *remote code execution* in certain versions of Microsoft Edge that are built on Chromium. This means an attacker can potentially run code on your computer just by getting you to visit a malicious web page.
How Does This Vulnerability Work?
CVE-2023-23374 is the result of how Microsoft Edge (built on Chromium) failed to properly handle objects in memory. When a specially-crafted web page exploits this flaw, it can corrupt the browser's memory in a way that enables the execution of arbitrary code.
Here’s a rough flow
User Clicks Malicious Link → Malicious JavaScript executes →
Memory Corruption in Edge → Controlled Code Runs
Technical Details & Example
> Note: The actual exploit primitives are confidential, but we can demonstrate general exploitation through a simplified use-after-free vulnerability, as the bug class is similar.
Let’s imagine the vulnerability relates to improper handling of JavaScript ArrayBuffer objects that leads to out-of-bounds access:
Exploit Snippet (POC-Style)
// The following is a simplified example pattern (NOT an actual day!)
// It illustrates the category of bug exploited in CVE-2023-23374.
let ab = new ArrayBuffer(16);
let ta = new Uint32Array(ab);
ab = null; // Trigger a sometimes-use-after-free scenario (very simplified).
// Trying to reallocate ab's memory for a new object...
let evil = { fake: Function.prototype, value: x1337 };
garbage_collect(); // Hypothetical function, not available in browsers.
// If the exploit is successful, the ta object might point to a freed memory region now controlled by evil
console.log(ta[]); // Arbitrary memory read/write could follow
*In a real-world RCE scenario, the attacker chains this with a shellcode payload, ultimately running code locally.*
Practical Exploit Example
Researchers have demonstrated similar exploits on Chromium-based browsers—such as in this security analysis by Project Zero. However, specifics about CVE-2023-23374 remain closely guarded.
For a demonstration, see this (fictionalized) sequence
<!-- Example: Malicious HTML file for demonstration. -->
<html>
<body>
<script>
// Note: Contains exploit primitives, but not an actual attack.
// Spray the heap to improve chances of memory corruption
let arrs = [];
for(let i=; i<10000; i++) {
let arr = new Uint8Array(1024);
arrs.push(arr);
}
// Trigger the bug (hypothetical)
arrs[500] = null;
// Attempt to execute controlled payload
// The actual CVE-2023-23374 exploit was more complex!
</script>
</body>
</html>
Data theft or ransomware: Attacker could steal your credentials or install malware.
- Lateral movement: On a corporate network, attackers may use compromised machines to jump to others.
Microsoft Security Guidance:
Microsoft CVE-2023-23374 Security Update Guide
MITRE CVE entry:
CVE Details for CVE-2023-23374
Chromium Release Notes:
Chromium Security Release Notes
How Was It Fixed?
Microsoft released a patched version of Edge not long after discovery. The patch involved correcting how memory was handled inside the browser's JavaScript engine, preventing attackers from corrupting the memory space.
Final Thoughts
CVE-2023-23374 once again shows how complex and risky the modern web can be, even when using trusted browsers like Microsoft Edge. Memory safety issues remain a major source of RCE attacks, and timely updates are your best line of defense.
If you’re managing endpoints in a company, consider leveraging systems that enforce rapid browser patching everywhere. End users are strongly encouraged to stay up-to-date and alert.
*Stay safe online! If you want more technical deep-dives into modern vulnerabilities, follow the Microsoft Security blogs or check out Google Project Zero’s research for cutting-edge insights.*
Timeline
Published on: 02/14/2023 20:15:00 UTC
Last modified on: 02/23/2023 19:41:00 UTC