Cybersecurity is an ongoing battle between attackers and defenders, and vulnerabilities sometimes slip through even in the most widely used systems. One such flaw, tracked as CVE-2023-23405, targets the very heart of how computers communicate on networks—Microsoft’s Remote Procedure Call (RPC) runtime. In this exclusive long read, we break down this vulnerability, show you how it works with simple code snippets, and dive into real-world exploit possibilities.
What is CVE-2023-23405?
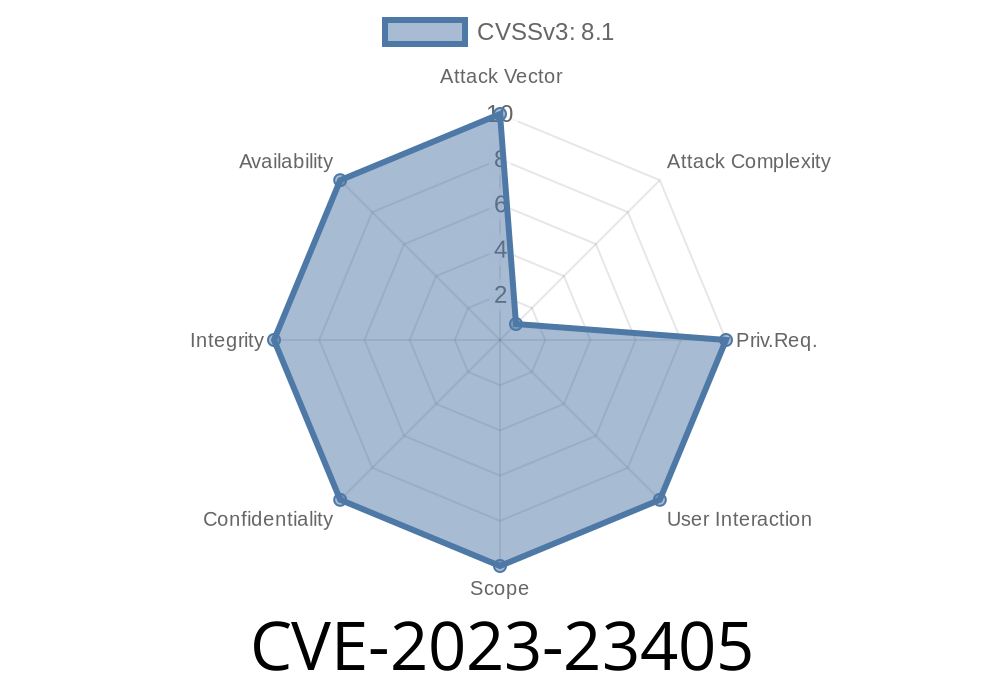
CVE-2023-23405 is a remote code execution (RCE) vulnerability that impacts the Microsoft Remote Procedure Call (RPC) runtime. The flaw was reported by Microsoft in February 2023 and poses a risk to a wide variety of Windows systems. An attacker who successfully exploits this vulnerability could run arbitrary code on the victim machine, potentially taking full control.
CVE entry:
- CVE-2023-23405 on MITRE
- Microsoft Advisory
What is the RPC Runtime?
RPC is a protocol that lets a program running on one computer execute code on a remote system as if it were local. It’s at the core of Windows networking and provides functionality for everything from file sharing to management interfaces.
If the code handling RPC requests has a bug, an attacker could send special network traffic that causes the target system to execute the attacker’s code.
How Dangerous is This Flaw?
According to the CVSS (Common Vulnerability Scoring System), CVE-2023-23405 scored a 9.8 out of 10. This is critical because:
Attackers can get full control over the system.
Affected systems: Windows 10, Windows 11, Windows Server versions (2012, 2016, 2019, 2022), and more.
Attack Vector: Network (including the Internet if not filtered).
Patch status: Patched as of February 2023. Patch details
How an Attack Might Look: Example Walkthrough
Imagine: An attacker on your company’s network discovers an unpatched Windows server. They send a specially crafted RPC packet to it using Python and public libraries.
Simplified Python Example (for Educational Purposes Only!):
*Note: This is a safe, simplified example showing how to make an RPC request. It does NOT exploit the real vulnerability.*
import socket
def send_rpc_packet(target_ip, target_port):
# Simplified, fake RPC packet. The real exploit would be crafted based on binary research.
fake_rpc_payload = b"\x05\x00\xb" + b"EXPLOITME" + b"\x00" * 64
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_ip, target_port))
s.sendall(fake_rpc_payload)
response = s.recv(4096)
print(f"Server response: {response}")
# Replace with the vulnerable server's IP and RPC port (135 for Windows by default)
send_rpc_packet('192.168.1.50', 135)
In a *real* exploit, the fake_rpc_payload would be painstakingly crafted to instruct the target’s RPC runtime to run code chosen by the attacker.
How to Protect Yourself
1. Patch All Systems: Install Microsoft’s February 2023 updates. Download patches here
Further Reading and References
- CVE-2023-23405 Official Description (MITRE)
- Microsoft Security Update Guide
- What is Microsoft RPC? (MSDN)
- Rapid7 Analysis
Final Thoughts
CVE-2023-23405 is a reminder of the dangers of unpatched services hiding in plain sight. With how deeply RPC is baked into Windows, a small mistake can create a giant target. Organizations must keep security updates current and always be on the lookout for vulnerabilities—big or small—that could open the door to attackers.
Stay secure; patch early and often!
If you found this post useful or have questions about network security, let us know in the comments. Stay tuned for more deep dives on breaking vulnerabilities!
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:54:00 UTC