---
In early 2023, Microsoft disclosed a major security vulnerability tagged CVE-2023-23407, involving the Windows implementation of Point-to-Point Protocol over Ethernet (PPPoE). This vulnerability allows an attacker to remotely execute code on vulnerable systems, potentially taking full control. Here, we break down what CVE-2023-23407 means, how it can be exploited, and what you should do to stay safe.
What is PPPoE, and Why Does it Matter?
Point-to-Point Protocol over Ethernet (PPPoE) is a network protocol that encapsulates PPP frames inside Ethernet frames. It’s commonly used by Internet Service Providers (ISPs) to manage client connections, especially for DSL broadband, letting your computer establish a connection to the internet.
Because PPPoE must parse complex data packets received over untrusted networks, bugs in its implementation can expose a computer to remote attacks.
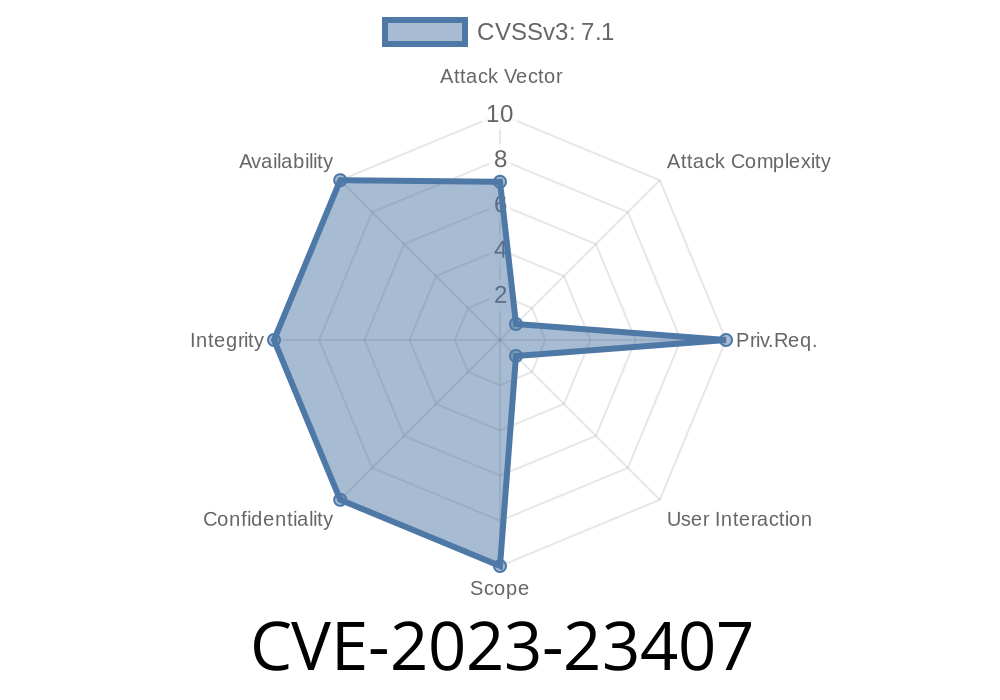
Attack Vector: Network (specifically, PPPoE connectivity)
Microsoft’s official advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23407
NVD entry:
https://nvd.nist.gov/vuln/detail/CVE-2023-23407
How Does the Exploit Work?
This vulnerability comes from improper validation of packets in the Windows PPPoE implementation. Simply put, when Windows connects to the internet using PPPoE, a remote attacker on the same network or ISP can send specially-designed PPPoE packets that trigger a buffer overflow or memory corruption vulnerability inside the operating system.
A successful exploit typically allows an attacker to execute arbitrary code with SYSTEM privileges — the highest level possible.
What Needs to Be in Place for Exploitation?
- The Windows device must have PPPoE configured (not all computers do — this is typical for DSL and some broadband users).
- The attacker must be able to send PPPoE traffic to the victim, usually by being on the same network segment (such as an ISP or malicious Wi-Fi).
Target Discovery: Attacker sniffs the network for devices that initiate PPPoE sessions.
2. Craft Malicious Packet: Attacker sends a PPPoE Active Discovery Initiation (PADI) or Session packet with a specially malformed PPP payload, often with a buffer-overflow condition.
3. Trigger Vulnerability: The Windows PPPoE service processes the packet and, due to improper boundary checks, overwrites memory–potentially leading to execution of remote shellcode.
Remote Control: Attacker gains remote code execution as SYSTEM.
## Code Snippet: Malicious PPPoE Packet Example (for Research/Education Only)
To understand how these kinds of exploits work, here’s Python code (with Scapy) to create a PPPoE discovery packet with an overlong payload that could trigger the bug in vulnerable systems:
from scapy.all import *
# Malform the payload — classic buffer overflow approach
malicious_payload = b"A" * 4096 # Over-sized payload
# Construct PPPoE Active Discovery Session packet
pppoe_packet = Ether(dst="ff:ff:ff:ff:ff:ff")/ \
PPPoED(code=x09, # Code: Session
sessionid=x001,
length=len(malicious_payload))/ \
Raw(load=malicious_payload)
# Send the crafted packet on the network (replace "eth" with your interface)
sendp(pppoe_packet, iface="eth")
> Warning: Do not launch malicious code against networks you do not own or have explicit permission to test. This code is for educational demonstration only.
Real-World Impact
Because PPPoE is still used by millions for home and business internet, especially outside major fiber or cable regions, the reach of this bug is broad. On affected computers, a malicious actor could:
How To Protect Yourself
- Update Windows as soon as updates are available. Microsoft has patched this vulnerability in their monthly Patch Tuesday releases:
- See Microsoft’s Guidance
If you don’t use PPPoE, disable or uninstall PPPoE adapters on your system for extra safety.
- For network administrators: segment and monitor networks, especially those with PPPoE connections.
Further Reading and References
- Microsoft Security Response Center: CVE-2023-23407
- NVD Detail Entry
- What is PPPoE? - Cloudflare Learning
- Scapy PPPoE Documentation
Conclusion
CVE-2023-23407 highlights how old protocols can introduce new risks in modern systems. Anyone relying on PPPoE for connectivity, especially on Windows desktops or servers, should upgrade immediately. Even if you don’t use PPPoE, keeping your system patched is always your best defense.
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:54:00 UTC