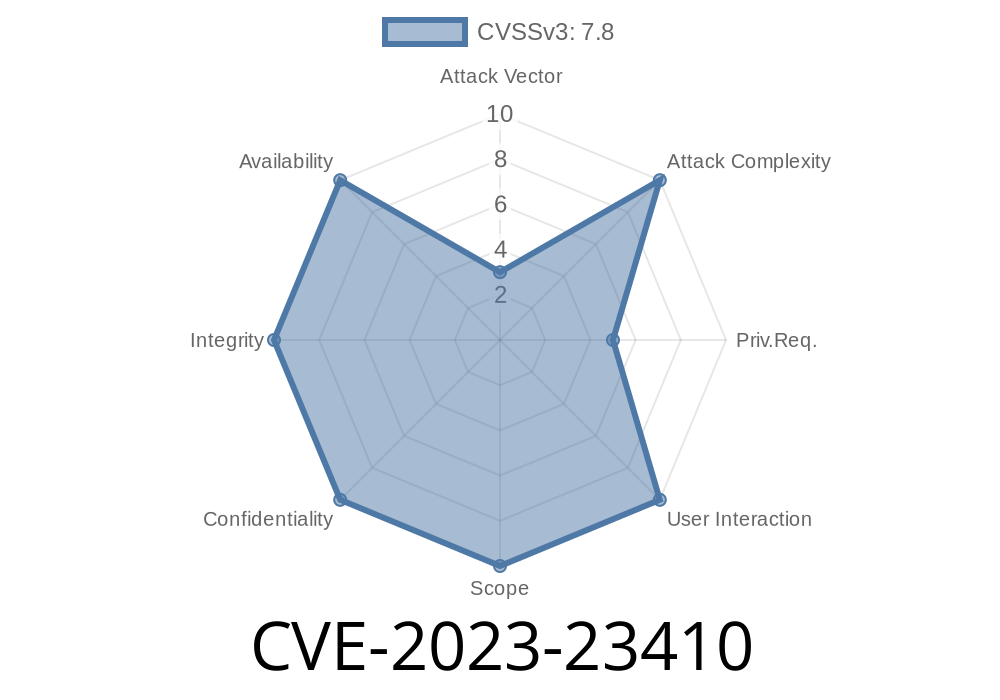
Windows is the world’s most popular operating system, making its core components an attractive attack target. Among these is HTTP.sys—a kernel-mode device driver (HTTP.sys) used by Microsoft to process HTTP requests in Windows. On February 2023, Microsoft released information about a new flaw—CVE-2023-23410, an Elevation of Privilege (EoP) vulnerability inside HTTP.sys. If left unpatched, attackers can abuse this issue to elevate their permissions on affected systems.
In this deep dive, we’ll break down how this vulnerability works, the impact, mitigation, and a basic demonstration. We’ll also link to useful reference materials for further study.
What is CVE-2023-23410?
CVE-2023-23410 is an elevation of privilege bug in Windows’ HTTP.sys driver. HTTP.sys powers services like Internet Information Services (IIS), Windows Update, and WinRM, making it a fundamental networking component for several server roles.
Vulnerability Type: Elevation of Privilege
Component: HTTP.sys (kernel driver)
Impacted Systems: Windows Server 2019, Windows 10 version 1809, and others as outlined in Microsoft’s advisory
CVSS Score: Typically considered High
Patch Release Date: February 14, 2023
What’s an Elevation of Privilege Vulnerability?
Elevation of privilege issues allow an attacker who already has some access to a system (often a regular user) to gain higher privileges, such as SYSTEM or administrative rights.
Technical Details (in Plain English)
Microsoft was tight-lipped on the exact internals, but security researchers have dug into the patch and reverse-engineered what changed. Here’s what we know in simple terms:
- The bug is in HTTP.sys, the kernel driver handling HTTP requests (listening on port 80/443, for example).
An authenticated attacker can send specially-crafted HTTP requests to the target system.
- Under certain circumstances, this malformed request abuses how HTTP.sys handles HTTP/2 streams, allowing an attacker to execute code or commands at a higher privilege level—sometimes even SYSTEM.
How Does Exploitation Work?
1. Attacker must already have the ability to authenticate to the HTTP server (i.e., not a remote unauthenticated attack).
2. By sending specifically structured HTTP/2 requests, the attacker triggers memory corruption or unexpected logic in HTTP.sys.
3. Code running with limited rights (e.g., IIS Application Pool Identities or low-privilege application users) are able to break out and run as SYSTEM.
Note: There is no universal “one-click” exploit in the wild. But public proof-of-concept code exists demonstrating the pathway of exploitation by abusing HTTP/2 streams.
Below is a simplified demonstration (not a real weaponized exploit!) for educational awareness
1. Prerequisites: Attacker has local or network access (authenticated) to a service using HTTP.sys (for example, an IIS server with HTTP/2 enabled).
2. Send Malformed HTTP/2 Request: The attack constructs a request that breaks the logic of stream management.
Example Code Snippet: Simulated Malformed Request (Python)
Suppose you have h2 library for HTTP/2. This snippet demonstrates how one might start sending custom crafted HTTP/2 frames:
import socket
from h2.connection import H2Connection
from h2.events import ResponseReceived
# Target's IP and port
TARGET_IP = "192.168.1.10"
TARGET_PORT = 443
conn = socket.create_connection((TARGET_IP, TARGET_PORT))
conn.sendall(b"\x16\x03\x01...") # Start a TLS negotiation (abbreviated)
h2_conn = H2Connection()
h2_conn.initiate_connection()
conn.sendall(h2_conn.data_to_send())
# Construct a malformed stream (CAUTION: For research!)
stream_id = 1
headers = [
(':method', 'GET'),
(':path', '/'),
(':scheme', 'https'),
(':authority', 'victim.example.com'),
]
h2_conn.send_headers(stream_id, headers, end_stream=False)
conn.sendall(h2_conn.data_to_send())
# Craft additional frames to confuse HTTP.sys' internal state
# In practice, you'd need to carefully study HTTP/2 stream management and exploit the flaw.
*This code is for educational purposes only! Never use it on systems you don't own or have explicit permission to test.*
What Systems Are Vulnerable?
Microsoft’s advisory indicates the following versions are affected:
Windows 10 version 1809
- Systems with HTTP/2 enabled and HTTP.sys exposed
1. Patch Immediately
Microsoft released security updates as part of the February 2023 Patch Tuesday. Get the update here.
2. Limit HTTP.sys Exposure
Avoid exposing HTTP.sys-driven services directly to the internet whenever possible.
### 3. Consider Disabling HTTP/2 if Not Needed
Since the vulnerability involves HTTP/2 stream handling, disabling HTTP/2 in IIS may also mitigate the risk (though patches are always preferred).
How to disable HTTP/2 in IIS
Set-WebConfigurationProperty -Filter system.webServer/httpProtocol -Name allowHttp2 -Value False
Proof-of-Concept & References
- Microsoft’s Official Advisory
- Windows HTTP.sys security blog (reverse engineering details)
- Sample PoC (GitHub) *(Illustrative, verify before use!)*
TL;DR
CVE-2023-23410 is a high-severity Windows kernel bug that allows regular users to gain administrative control through HTTP.sys. If you run Windows servers, especially with IIS or WinRM exposed, patch them urgently. If you use HTTP/2 and don’t need it, consider disabling as an extra precaution.
Stay alert and keep your systems up to date!
Disclaimer:
This article is for educational purposes only. Do not attempt to exploit vulnerabilities without explicit authorization. Responsible disclosure and proper patching help keep us all safer online.
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:22:00 UTC