Modern computing relies on countless drivers and device utilities to function. Unfortunately, these complex pieces of software often harbor hidden security risks. One such risk emerged in 2023, as Microsoft acknowledged a critical flaw in their ubiquitous PostScript and PCL6 Class Printer Drivers for Windows. Designated CVE-2023-23413, this vulnerability opens the door for remote code execution attacks—a nightmare scenario for IT professionals, businesses, and everyday users. Let’s break down what makes CVE-2023-23413 so dangerous, how attackers might exploit it, and what you can do to stay safe.
What Is CVE-2023-23413?
On February 14, 2023, Microsoft released a security update addressing a security bug in the Microsoft Windows PostScript and PCL6 Class Printer Drivers. These are default drivers found in many Windows installations, used to print with a wide variety of laser, inkjet, and business printers.
The flaw, CVE-2023-23413, is categorized as a Remote Code Execution (RCE) vulnerability. RCEs are particularly hazardous because they can allow an attacker to run malicious code on your computer from anywhere—sometimes with elevated privileges.
Official Microsoft Advisory:
- Microsoft CVE-2023-23413 Security Update Guide
Other Key References:
- NVD - CVE-2023-23413
- ZDI-23-220 (Zero Day Initiative advisory)
How Does the Vulnerability Work?
CVE-2023-23413 is a vulnerability in the way Windows’ printer drivers handle certain specially crafted files (such as PostScript or PCL6 print jobs). If an attacker can trick a user into printing a malicious file—whether by email attachment, website, or network share—the driver may process the file incorrectly, allowing code to be executed on the target system.
No user interaction is required beyond attempting to print a malicious document.
- Attackers could potentially trigger this by getting you to open and print a file or by exploiting network printers.
Victim prints the file using a vulnerable printer driver.
3. The malicious code in the print job triggers a buffer overflow or similar bug in the driver, allowing arbitrary code execution.
4. The payload runs with the privileges of the user (sometimes higher, depending on the configuration).
Example Exploit Concept
While a public working exploit is not available for ethical and legal reasons, here's a pseudo-code example that demonstrates a basic logic of the attack:
# This pseudo-code does not exploit the bug directly,
# but shows the general logic that a real exploit might use.
malicious_postscript = b"%!PS\n" # PostScript file header
malicious_postscript += b"%" + b"A" * 4096 + b"\n" # Overflow buffer
# Insert shellcode or malicious commands here
with open("exploit.ps", "wb") as f:
f.write(malicious_postscript)
# When printed with the vulnerable driver, this could trigger the bug
Note:
The real exploit would require detailed understanding of driver internals, memory layout, and possibly bypassing modern Windows security mitigations like DEP and ASLR.
How Bad Is It?
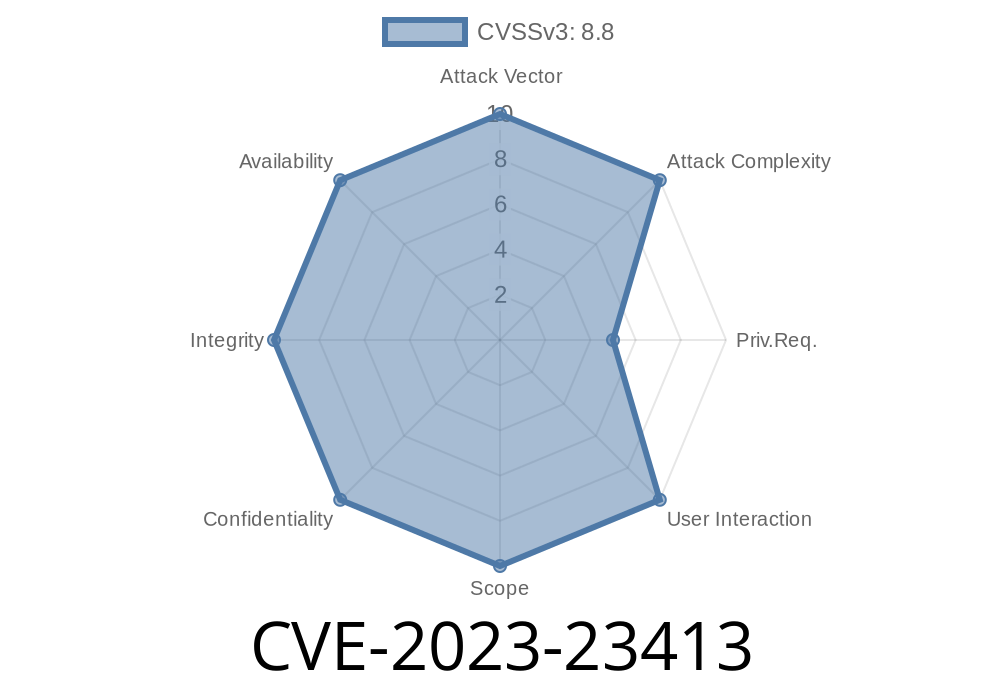
Severity score:
CVSS 3.1 Base Score: 7.8 (High)
Affected Systems:
- Windows systems (including Windows 10, and Windows Server versions) using the default PostScript and PCL6 Class Printer Drivers pre-patch.
Attack complexity:
LOW: A typical user action, such as printing a document, may trigger the bug.
Impact:
Real-World Attack Scenarios
1. Phishing Email: User receives an email with a seemingly regular document (e.g., invoice.ps). The user prints it, activating the exploit.
2. Malicious Website: User browses to a compromised website that instructs the browser to print a remote file via a vulnerable driver.
Apply Updates:
Microsoft’s February 2023 Patch Tuesday includes the fix. Install all security updates using Windows Update.
- Microsoft Update Catalog
Final Words
CVE-2023-23413 is a stark reminder of how even basic system functions like printing can pose severe cybersecurity threats. By leveraging a bug in common printer drivers, attackers get a promising entry point into organizations and home networks alike. Thankfully, Microsoft’s swift response and the wide availability of the patch mean you can secure your systems effectively—just be sure to update as soon as possible.
Further Reading and References
- Microsoft CVE-2023-23413 Advisory
- NIST National Vulnerability Database
- Zero Day Initiative ZDI-23-220
- Microsoft Update Catalog
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:55:00 UTC