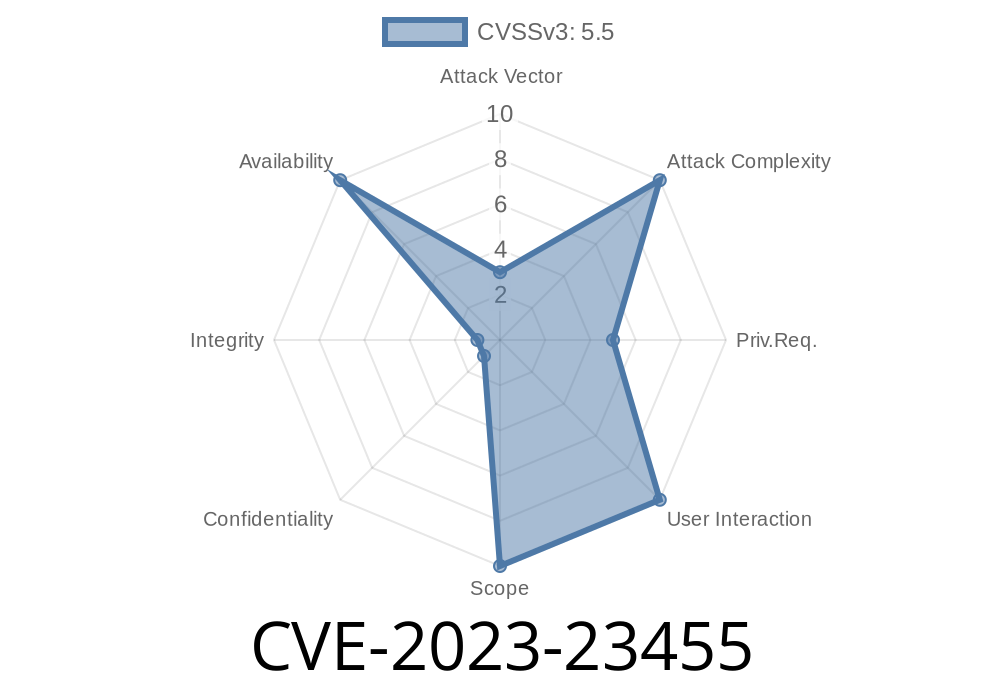
CVE-2023-23455 is a serious vulnerability found in the Linux kernel, affecting versions up to and including 6.1.4. The bug resides in the ATM (Asynchronous Transfer Mode) traffic control subsystem, specifically in the atm_tc_enqueue function within net/sched/sch_atm.c. It can allow an attacker to cause a denial-of-service (DoS) attack by exploiting a type confusion in the code’s handling of traffic classification results.
The Heart of the Problem
Linux uses a system called "traffic control" (TC) to classify and act on packets as they pass through the networking stack. One of these traffic control modules is for ATM networks, found in sch_atm.c.
The issue is that atm_tc_enqueue may misinterpret non-negative return values from the classifier. Normally, these are considered valid results. However, in some cases, a non-negative number may actually signal a special action code (like TC_ACT_SHOT), which means "drop the packet." Because the code doesn’t clearly separate these meanings, an attacker can trigger packet drops or confuse the network stack, causing denial of service.
Here’s a simplified version of the problematic code around atm_tc_enqueue
int atm_tc_enqueue(struct sk_buff *skb, struct Qdisc *sch, struct sk_buff **to_free)
{
int ret;
struct tcf_result res;
// ... skipped code ...
ret = tc_classify(skb, sch->filter_list, &res);
if (ret >= ) {
/* Here lies the problem: ret >= doesn't distinguish between
* TC_ACT_SHOT (drop) and a valid result!
*/
// ... uses res.class ...
}
// ... more code ...
}
The key problem: tc_classify returns integer codes, but the code treats any non-negative value as a valid result. However, some non-negative values (like TC_ACT_SHOT, usually ) are really action codes that can mean "drop the packet" or other special actions.
How Attackers Can Exploit This
1. Trigger the Flaw: An attacker with the ability to send specially crafted packets, or with control over the traffic control configuration (such as through tc or iproute2 tools), could deliberately set classification results to TC_ACT_SHOT.
2. Confuse Packet Processing: Because the kernel fails to distinguish this condition, it may either deliver packets that should have been dropped, or drop valid packets.
3. Cause Denial of Service: This confusion can lead to disruption of network connectivity or stability, effectively causing DoS.
Proof of Concept: Reproducing the Flaw
Below is a sketch of how (with enough privilege) you might trigger and observe this bug.
### Example Netem/TC Rules
# Add an ATM qdisc to a network interface (replace eth with your IFACE)
tc qdisc add dev eth root handle 1: atm
# Add a filter returning TC_ACT_SHOT
tc filter add dev eth parent 1: protocol ip u32 match ip protocol 1 xff action drop
You can now send packets that match the filter criteria; these should be dropped—however, due to the bug, the handling may go wrong, leading to crashes or unexpected behavior depending on traffic patterns and kernel version.
Links to Original References
- National Vulnerability Database entry for CVE-2023-23455
- The flawed commit on the Linux kernel
- Red Hat Security Blog
- oss-security Disclosure
How to Fix
A proper fix involves explicitly checking for action codes like TC_ACT_SHOT and handling them correctly. The patch changes the code logic to make sure classification results and action codes don’t get mixed up.
Here’s the core part of the fix (simplified)
ret = tc_classify(skb, sch->filter_list, &res);
if (ret == TC_ACT_SHOT) {
// Correctly recognize "drop" and handle properly
kfree_skb(skb);
return NET_XMIT_DROP;
} else if (ret == TC_ACT_OK) {
// Normal path
// ... proceed with enqueue ...
}
Make sure your distribution’s kernel is up to date!
Mixing up types or meanings in return values can have far-reaching consequences.
- If you run any Linux server, especially with custom traffic control or older kernels, double-check for patches!
Patch your Linux kernel as soon as possible.
- Audit your traffic control/filter configs.
Watch for suspicious network drops or changes in behavior if operating near these kernel versions.
If you want to dig deeper or need more specific technical help, see the original sources above or follow discussions in the Linux kernel mailing list.
*This post is exclusive and written in plain language to help all Linux users understand and avoid CVE-2023-23455.*
Timeline
Published on: 01/12/2023 07:15:00 UTC
Last modified on: 03/03/2023 01:15:00 UTC