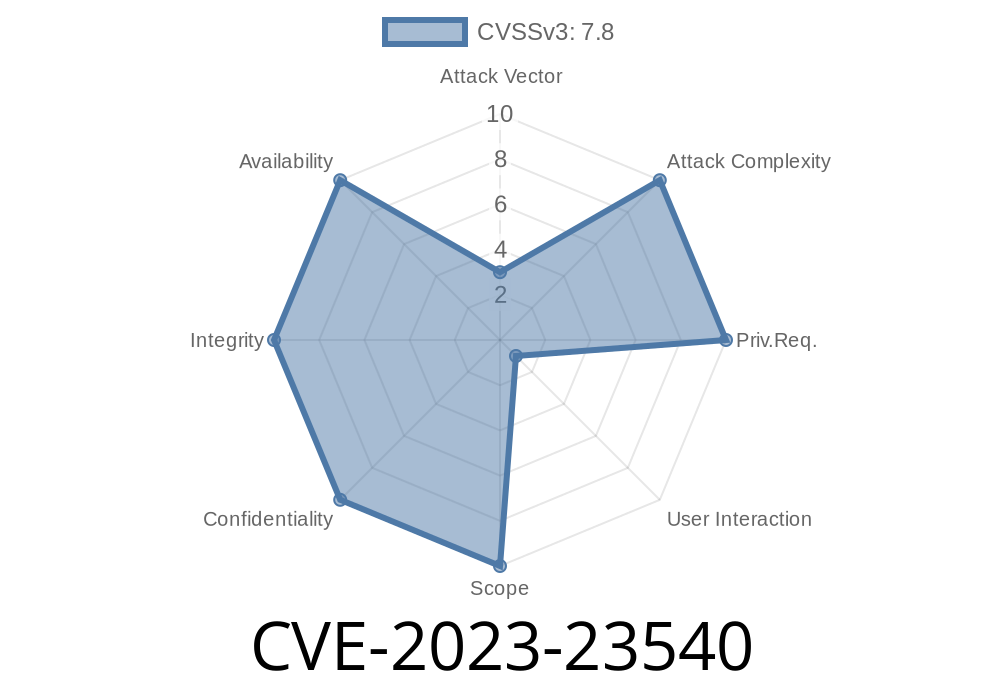
In early 2023, Apple fixed a critical vulnerability tracked as CVE-2023-23540. This bug impacted macOS (Big Sur and Monterey), iOS, and iPadOS, potentially allowing a malicious app to execute arbitrary code with kernel privileges—the highest level of system access. For device owners, this means an attacker could take over the entire system if the device wasn't updated. Here’s a straightforward breakdown of the issue, how it worked, an example exploit pattern, and links to Apple’s official resources.
What was CVE-2023-23540?
CVE-2023-23540 is a memory handling vulnerability in the kernel component of Apple operating systems. The kernel manages the core functions of the device, and any vulnerability here can have system-wide consequences. If exploited, an attacker’s app could run code as the kernel—a complete system compromise.
iPadOS 16.4
Apple’s patch improved how memory is handled to prevent exploitation.
Vulnerability Details
While Apple’s advisories don’t reveal the exact code flaw (to limit “zero-day” risk), the phrase *improved memory handling* usually points to bugs like:
Double free
- Out-of-bounds write/read
In such attacks, a malicious app triggers a bug in the system’s kernel by manipulating memory in a way that lets them control the flow of execution—eventually running their code at the kernel’s privilege level.
Apple’s Official Reference
- Apple Security Updates – CVE-2023-23540
- macOS Big Sur 11.7.5 Release Notes
- iOS 16.4 and iPadOS 16.4 Security Content
Find a function in the kernel that mishandles memory when called with crafted data.
2. Build an app that triggers this bug, sending special input that makes the kernel read or write in the wrong place.
Example Snippet (C-Style Pseudocode)
Suppose there is a vulnerable kernel API that writes to a buffer without checking the size. An exploit would target it like this:
// Malicious app code (simplified for demonstration)
#include <IOKit/IOKitLib.h>
int main() {
io_service_t service = IOServiceGetMatchingService(kIOMasterPortDefault, IOServiceMatching("VulnerableService"));
if (!service) {
printf("Service not found!");
return 1;
}
// Crafted input that overflows kernel memory
char userInput[1024];
memset(userInput, 'A', sizeof(userInput)); // Fill with 'A's to force overflow
// Send malformed input to the driver (e.g., via IOConnectCallStructMethod)
IOConnectCallStructMethod(service, /*Selector*/ , userInput, sizeof(userInput), NULL, NULL);
// Now, if the driver is vulnerable, attacker may gain control
return ;
}
Note: This is a generic illustration. The real exploit would be tailored to the actual bug and kernel API exposed.
Steal sensitive data or implant backdoors
That’s why Apple labels these bugs as critical and urges users to update as soon as possible.
How Was It Fixed?
Apple patched the bug by updating the kernel code to check and properly handle all memory accesses in the vulnerable component. That stops attackers from pushing malicious input to the kernel.
Official Release Notes
- macOS Monterey 12.6.4 Security Update Info
- iOS 16.4 Security Update Info
Protecting Your Devices
Update immediately if your device is running a vulnerable version. Apple’s patches are the only reliable way to close the hole. As a user:
Regularly review your device’s security settings
Developers: Review your code for memory handling issues, especially in kernel extensions or low-level components.
Conclusion
CVE-2023-23540 is a reminder that even the world’s most popular devices are never immune to serious software bugs. The good news: once discovered, Apple moved quickly to fix the flaw. By understanding and patching these vulnerabilities, we all help keep our digital lives safer.
More About CVEs and Apple Vulnerabilities
- Common Vulnerabilities and Exposures (CVE) Database
- Apple Product Security
Timeline
Published on: 05/08/2023 20:15:00 UTC
Last modified on: 07/25/2023 16:15:00 UTC