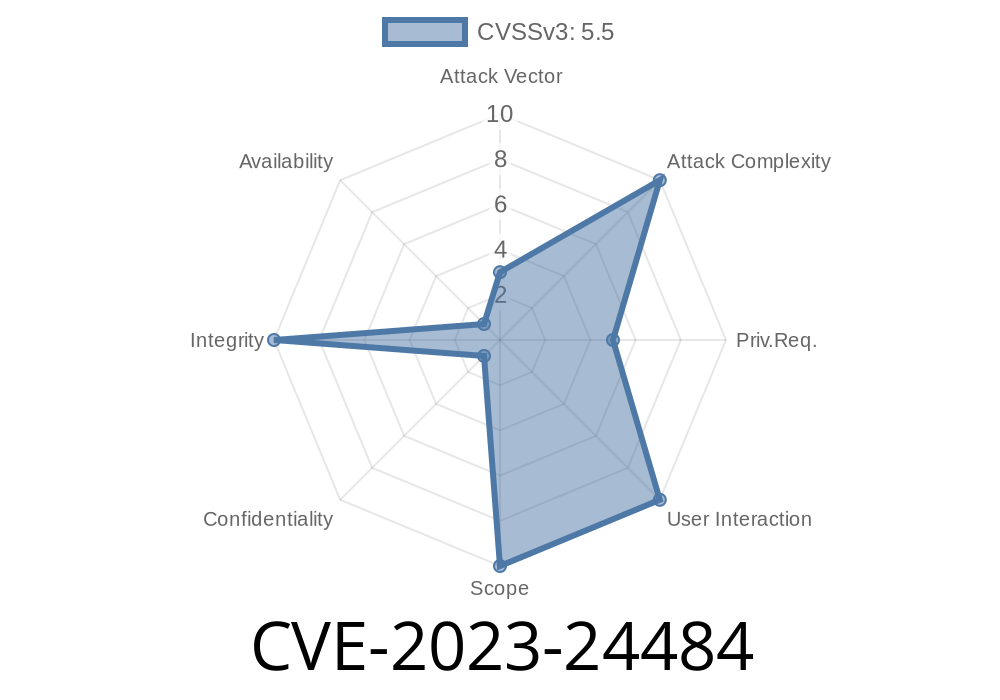
CVE-2023-24484 is a significant bug that impacts certain logging systems within software applications, enabling attackers to plant log files into directories they shouldn’t be able to touch. Simple in concept, but potentially big in impact, this vulnerability shows the importance of proper file and directory management, especially when logs are concerned.
This long-read post explains what this CVE is all about, breaks down why it matters with easy-to-understand code, provides real-world attack scenarios, and directs you to the best references for further study.
What is CVE-2023-24484?
CVE-2023-24484 describes a flaw where a malicious user can manipulate logging mechanisms so that log files are written to directories where the user should NOT have write permissions. This can open the door to security breaches, such as:
Planting files where only trusted processes should write
Affected Software: Some logging libraries and applications, including (but possibly not limited to) certain versions of Citrix Workspace, have been reported as vulnerable.
How Does the Exploit Work?
The core of the problem is improper validation (or sanitization) of directory paths when writing log files. If the software takes user-supplied data to form a filepath (directly or indirectly), attackers could trick it into redirecting log writes.
Example Scenario
Let’s say an application logs user actions to a file, and the *username* is used to build the logfile name.
Vulnerable Node.js Logging Example
const fs = require('fs');
const path = require('path');
function logUserAction(username, action) {
// Danger: username unsanitized!
const logfile = path.join('/var/log/app', ${username}.log);
fs.appendFileSync(logfile, ${action}\n);
}
// Malicious input:
logUserAction('../../etc/cron.d/pwned', 'Attacker was here!');
What’s happening?
- If the application runs as a privileged user, the attacker-controlled *username* (e.g., ../../etc/cron.d/pwned) can cause a log file to be created in /etc/cron.d, a directory where normal users have no write permissions.
- The attacker just bypassed directory restrictions by smuggling filesystem navigation (../) through user input—a classic path traversal!
Placing unauthorized files (which may be executed, e.g., as cron jobs)
- Tainting logs with fake/hidden entries
- Deleting/overwriting sensitive files (if logs are rotated)
Let’s walk through a hypothetical attack
1. Attacker supplies username as ../../var/www/html/shell.php
The innocent-looking log entry is written as
/var/log/app/../../var/www/html/shell.php
3. On Unix systems, this path resolves to /var/www/html/shell.php
4. The attacker crafts the “log entry” to contain PHP code (if the web server executes PHP from that directory):
<?php system($_GET['cmd']); ?>
5. Result: The attacker can now run commands on your server by hitting http://yourserver/shell.php?cmd=ls
Not science fiction! In the wild, similar attacks have been seen with log poisoning and log injection.
Real-World References
- Citrix Security Bulletin on CVE-2023-24484
- NVD CVE-2023-24484 Details
- OWASP Path Traversal Cheat Sheet
Always validate and sanitize everything that becomes part of a path
function safeLogUserAction(username, action) {
// Only allow alphanumeric usernames, no slashes/periods
if (!/^[a-zA-Z-9_-]+$/.test(username)) {
throw Error('Invalid username!');
}
const logfile = path.join('/var/log/app', ${username}.log);
fs.appendFileSync(logfile, ${action}\n);
}
2. Use Least Privilege
Run your applications with the lowest permissions needed. Don’t let web apps run as root or with access to sensitive directories.
3. Set Proper File and Directory Permissions
Ensure only the app/service itself can write to its log directories.
4. Log to a Centralized Secure System
Whenever possible, send logs off the server entirely (e.g., to syslog, ELK, or a cloud logging service).
Conclusion
CVE-2023-24484 is a reminder that even something as boring as log files can be the launchpad for a nasty attack. If your app lets attackers write files where they shouldn't, you're leaving the front door wide open.
Check your code now—make sure you never directly use user input in file paths, and your logs are as secure as your secrets.
Quick References
- Citrix CVE-2023-24484 Advisory
- NVD CVE-2023-24484
- OWASP Path Traversal Defense Guide
Timeline
Published on: 02/16/2023 18:15:00 UTC
Last modified on: 02/24/2023 19:28:00 UTC