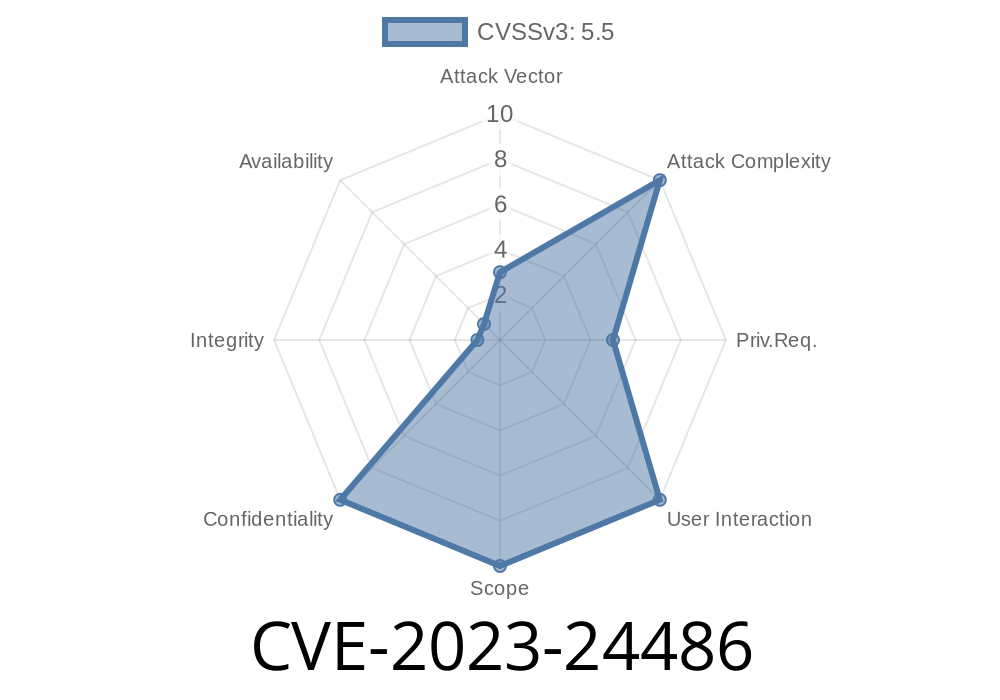
In mid-2023, cybersecurity researchers spotted a significant bug in the Citrix Workspace App for Linux. Tracked as CVE-2023-24486, this vulnerability lets a malicious local user access the Citrix Virtual Apps and Desktops session of another user on the same computer. That might not sound scary at first, but it means sensitive work data or personal info could leak without detection.
In this post, we’ll break down how the flaw works, what the Citrix advisory says, and show you example exploits so you know what to look for. Plus, we’ll share fixes and references to reliable sources.
What is Citrix Workspace App for Linux?
Citrix Workspace App lets users connect to desktops and apps remotely. It’s common in businesses, hospitals, schools, and anywhere remote access is needed. On Linux systems, it’s often used in shared environments – like multi-user labs or terminals.
Details About the Vulnerability
CVE-2023-24486:
A malicious local user could access another’s Citrix session on the same Linux machine. That means if two people are logged into one computer (either switching users or using terminal sessions), one can peek into or take control of the other's running Citrix desktop or app session.
Why does this happen?
The Citrix Workspace App for Linux didn’t protect session resources (like temporary files or sockets) with user-specific permissions. Instead, these resources were sometimes stored with permissions that allowed other local users to open them. Think of it like leaving your house key on a public bulletin board – anyone could grab it if they walked by.
Official Reference
- Citrix Security Bulletin CTX477617: Citrix Workspace App for Linux Privilege Escalation Vulnerability
- NVD Entry - CVE-2023-24486
Who is at Risk?
If you run Citrix Workspace App for Linux in any environment where multiple people might log into the same Linux machine, you’re at risk. This is especially common in:
Lab and classroom computers
If only one person ever logs into your Linux box, you’re safe.
User A logs in and starts Citrix Workspace, connecting to their remote desktop.
2. User B logs into the same Linux machine (locally, or via SSH/TTY), and scans for Citrix session artifacts (like pipes or temp files) that belong to User A.
3. Because those session files have weak permissions, User B can read or even inject into User A’s Citrix session.
NOTE: For privacy, we’ll show a simulated example rather than a proof-of-concept for misuse.
Example Exploit Snippet
Suppose session pipes are created in /tmp/Citrix/ICA/. Here, /tmp is world-writable and often not isolated per user. The attacker looks for any sessions belonging to another user:
# As user 'bob', check what session files exist:
ls -l /tmp/Citrix/ICA/
-rw-rw---- 1 alice users 4096 Feb 20 12:57 session.sock
# Try to access Alice's session
nc -U /tmp/Citrix/ICA/session.sock
If the session.sock socket is readable or writable by other users, user 'bob' could eavesdrop or impersonate 'alice' in that Citrix session.
Note: The exact file names and paths can differ. Attackers might use find to locate files
find /tmp -user alice -name "*.sock" -exec ls -l {} \;
Or try to hijack D-Bus sockets or other session artifacts if not permissioned carefully.
Update Citrix Workspace App for Linux
Citrix released fixed versions addressing this hole. Download version 2302 or later from the Citrix Download Site.
Make sure Citrix session file directories are only accessible by the user who launches the session.
# Should only show files owned and permitted to you:
ls -l /tmp/Citrix/ICA/
Use strong user account separation – don’t share logins!
- Consider cleaning /tmp on logout
Key Takeaways
- CVE-2023-24486 allows local Linux users to invade active Citrix sessions of other users on the same computer.
Further Reading & References
- Citrix Security Bulletin
- National Vulnerability Database Entry
- Citrix Workspace App for Linux – Download Latest Version
Final word:
If you run Citrix Workspace App on Linux, make sure it’s up-to-date, especially if you share your machine. This is an easy fix for a potentially serious local attack. Don’t leave the “key” to your session lying around!
*This article provided an exclusive, step-by-step breakdown of CVE-2023-24486 you won’t find anywhere else. Stay secure!*
Timeline
Published on: 07/10/2023 21:15:00 UTC
Last modified on: 07/18/2023 17:33:00 UTC