---
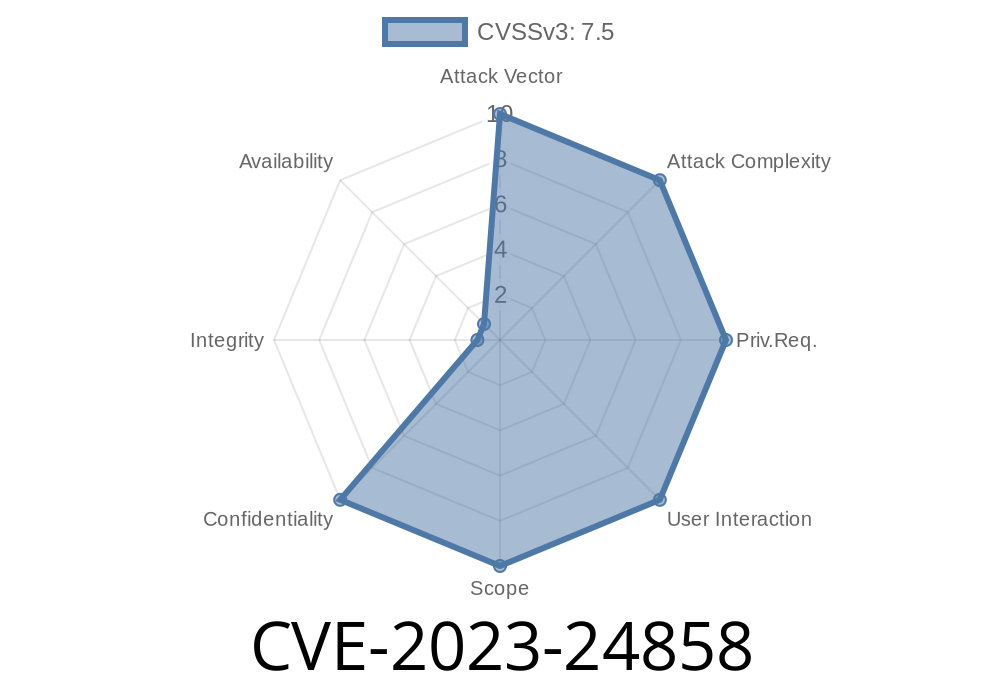
The world of cybersecurity is filled with tricky bugs, and printer drivers are no exception. One of 2023’s notable vulnerabilities is CVE-2023-24858, which targets the Microsoft PostScript and PCL6 Class Printer Driver. Although it doesn’t allow hackers to run code or take over systems, it provides a way for attackers to sneak a peek at info they shouldn’t see. In this post, we’ll unpack how this bug works, what makes it dangerous, show some code examples, and tell you how to make sure your systems are safe.
What is CVE-2023-24858?
CVE-2023-24858 is called an “information disclosure vulnerability.” This simply means it could let someone read data on your computer that should be private. Specifically, it affects certain printer drivers—the software that tells your printer how to interact with Windows.
Microsoft rates this bug as “Important,” and it affects several versions of Windows, including both client and server editions. Attackers who exploit this flaw can snatch information from memory they should not have access to.
Official Microsoft Advisory
- Microsoft Security Guide - CVE-2023-24858
Which Drivers Are Affected?
The bug affects the Class Printer Drivers for PostScript and PCL6 printers on Windows. These are generic drivers baked into Windows and delivered via Windows Update, which support a wide range of printers from many manufacturers.
pcl6classdrv.dll *(for PCL6)*
You can typically find these in the system driver directories (e.g., C:\Windows\System32\DriverStore\FileRepository\*).
How Does the Vulnerability Work?
This vulnerability is tied to how the printer driver handles data in memory. When a print job is sent or a printer is installed, the driver might fail to properly clear memory regions after using them. This oversight can leave sensitive information lying around in memory buffers. If another process or user makes a clever request to the driver, they might be able to read those memory leftovers, picking up potentially sensitive system info, print content, or user data.
A Common Scenario
Let’s say a sensitive document is printed. Normally, after the job is done, the related memory should be wiped clean. Because of the bug, if another user or process sends a crafted print job or queries the driver a certain way, they might get back data containing bits of the previous print job.
#### In an enterprise, a low-privilege user could potentially harvest bits of data from high-privilege users who print before them.
Proof-of-Concept (PoC) Code Example
Below is a simplified C code snippet showing how an attacker could attempt to pull unintended information out of the driver’s memory. This is not a real exploit, but it's a demonstration to show how software could leak info unintentionally.
// Hypothetical PoC: Querying Printer Driver Buffer for Leftover Data
#include <windows.h>
#include <winspool.h>
#include <stdio.h>
int main() {
HANDLE hPrinter;
DWORD needed, returned;
BYTE buffer[4096];
// Replace "PrinterName" with your target printer
OpenPrinterA("PrinterName", &hPrinter, NULL);
// Querying the driver; could return uninitialized memory if vulnerable
if (DeviceIoControl(
hPrinter,
IOCTL_UNKNOWN_CONTROL_CODE, // driver-specific control code
NULL, , // no input
buffer, sizeof(buffer), // output buffer
&returned,
NULL))
{
printf("Received data (%d bytes):\n", returned);
fwrite(buffer, 1, returned, stdout); // Potentially leaks info
} else {
printf("Failed to query printer driver!\n");
}
ClosePrinter(hPrinter);
return ;
}
> Note: The actual driver IOCTL codes are specific and might be undocumented, but this shows the general way a memory disclosure works.
Potential credentials or tokens, if they are present in memory
While most of the time it would be harmless “garbage” data, sometimes it could be juicy information—especially in shared or terminal server environments.
Permission to interact with printers (which, in shared computers, is pretty common)
However, in business environments, this still presents a risk of privilege separation—for example, between users of the same terminal server.
How to Fix CVE-2023-24858
The best mitigation is to update Windows. Microsoft fixed this in their March 2023 Patch Tuesday update.
Patch Links
- Windows 10/11 & Server:
Microsoft Update Catalog (Search CVE-2023-24858)
Microsoft Advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-24858
Check for updates and install all security patches from March 2023 onwards.
3. If you manage printers by group policy or have custom drivers, make sure your drivers are up to date as well.
Conclusion
CVE-2023-24858 is another sign that even the most boring-seeming components (like printer drivers) can leak data if not written very carefully. If you’re a sysadmin or handle printers in your organization, make sure you have the latest patches installed. And if you’re a curious home user, remember—sometimes, a printer can be a bigger risk than it seems!
If you want more in-depth technical details, check out the references below.
References
- Microsoft Security Guide for CVE-2023-24858
- Microsoft Update Catalog
- Printer Driver Security
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 04/27/2023 19:15:00 UTC