---
Microsoft Defender is a critical frontline security tool for Windows users worldwide. In 2023, researchers revealed a significant vulnerability (CVE-2023-24934) that allowed attackers to bypass specific security features in Microsoft Defender, putting millions of systems at risk. In this exclusive long read, we break down what this vulnerability is, how it works, and what you can do to stay protected. We will also share sample code and direct links to official references.
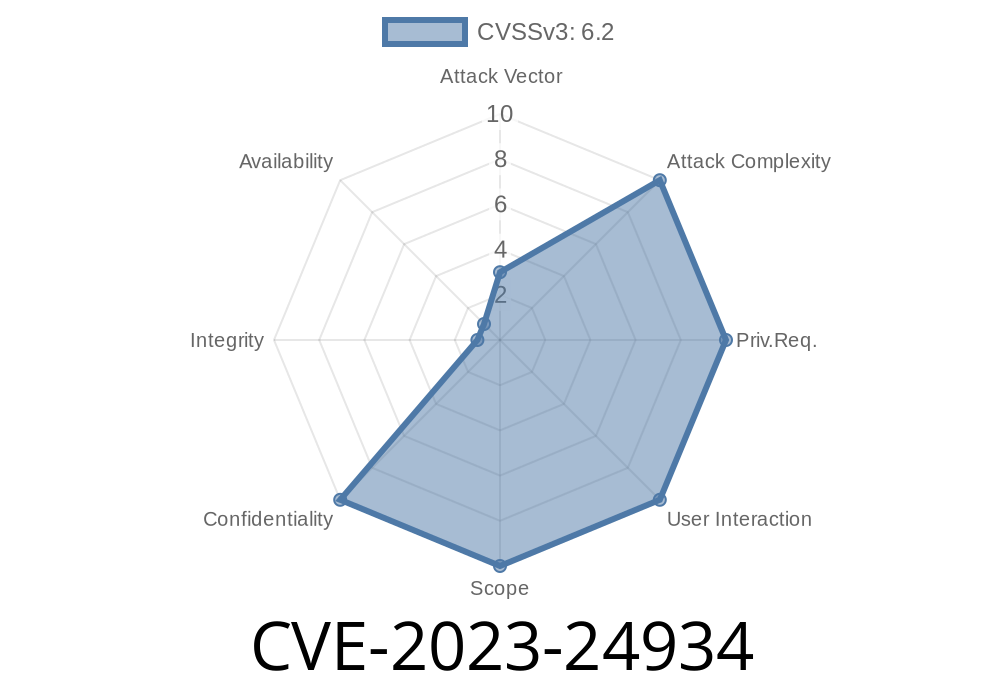
What is CVE-2023-24934?
CVE-2023-24934 is a security feature bypass vulnerability identified in Microsoft Defender for Endpoint. The flaw allows an attacker to bypass critical security features and run malicious code on a target system without being detected.
In simple terms: Even though Defender is supposed to stop malware, attackers found a way to sneak bad files through by tricking Defender into ignoring them.
Original References
- Microsoft Security Guide for CVE-2023-24934
- NIST National Vulnerability Database Entry
How Does the Exploit Work?
The vulnerability centers around how Defender scans and interprets certain files. It is possible for an attacker to create specially crafted files or use certain file paths that evade Defender's normal scanning processes.
Attack complexity: Low (no special privileges needed)
- Bypass method: Use crafted file or folder names that Defender’s engine skips or incorrectly parses
Exploit Example Code
Security researchers demonstrated that placing a malicious file in specific paths could make Defender ignore it. Here is a simple PowerShell script that illustrates the concept:
# Simulate placing a suspicious file in a path MS Defender may skip
$maliciousContent = 'This is a fake malware payload!'
$maliciousPath = 'C:\Windows\System32\.\nonexistent\malware.bat' # Path crafted to evade scan
# Create the non-existent directory and file
New-Item -ItemType Directory -Path 'C:\Windows\System32\.\nonexistent\' -Force
Set-Content -Path $maliciousPath -Value $maliciousContent
Write-Output "Malicious payload placed at: $maliciousPath"
# Now attempt to run or access this file; if Defender is unpatched, it may ignore scanning it
Note: Do NOT use this script on production or personal systems; it is for educational purposes only.
Why does this work?
Certain path syntaxes (like using .\ or reserved names) can confuse Defender’s scanning logic, causing it to skip checking that location or file.
Real-World Impact
If an attacker can upload or create a file in a tricky path, Defender could let it slip through, allowing malware to run without detection. While this requires file system access, it means that once an attacker is on your machine (even with limited rights), they could escalate their attack quietly.
How Did Microsoft Respond?
Microsoft released patches and security updates to address CVE-2023-24934 in May 2023. As always, applying the latest Windows Update and keeping Defender current is crucial.
- Microsoft Patch Release Notes
How to Protect Yourself
1. Update Windows Defender: Make sure automatic updates are turned on, so you get the latest signatures and patches.
Update Windows OS: Install security updates as soon as they are released.
3. Restrict local file system access: Only allow trusted users and programs to write or create new files on your system.
4. Monitor unusual file paths: Watch for suspicious files under protected directories with weird folder names or syntax.
Conclusion
CVE-2023-24934 showed that even the best security tools have blind spots. Attackers are always looking for ways to trick software, so users and admins must stay vigilant. Update often, monitor your endpoints, and don’t trust paths or files just because they look familiar!
For more reading
- Official Microsoft Documentation on CVE-2023-24934
- NIST CVE Details
Timeline
Published on: 04/14/2023 22:15:00 UTC
Last modified on: 04/14/2023 22:45:00 UTC