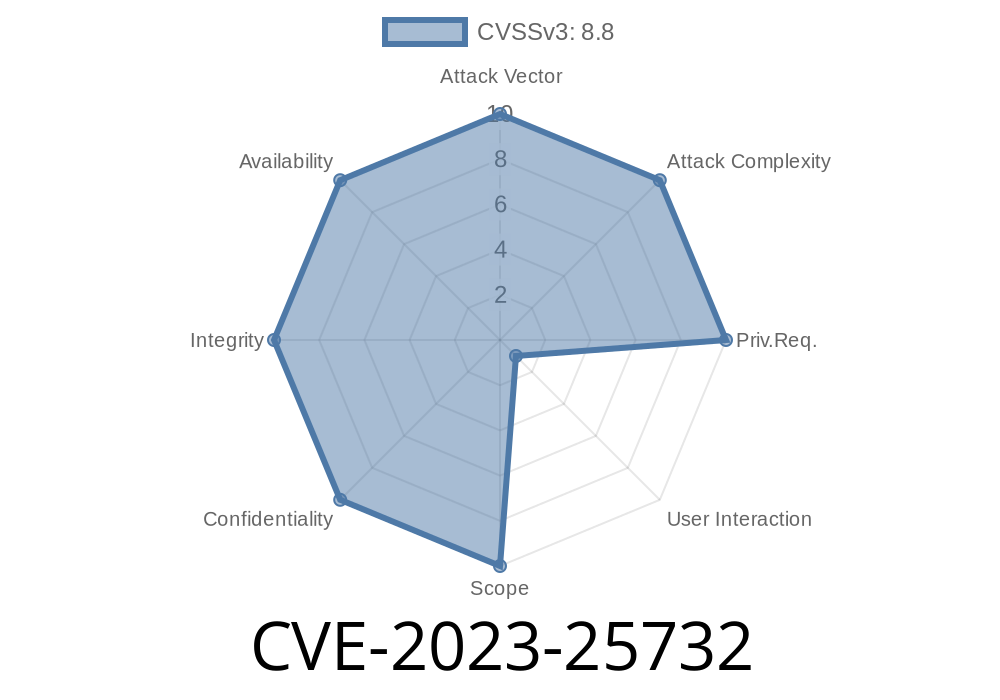
In the world of cybersecurity, memory corruption bugs are especially dangerous. They can allow an attacker to run code or crash your program. Let’s take a closer look at CVE-2023-25732, a bug found in Mozilla’s XPCOM framework, and see what caused it, what could go wrong, and how to protect yourself.
Firefox ESR versions before 102.8
This bug happens when encoding data from an inputStream in the XPCOM framework, a core system Mozilla products use for cross-platform component management.
Technical Details — Where Things Went Wrong
When data from an inputStream is being encoded, the program needs to know how big that data is to handle it safely. In this case, the code did not correctly calculate the size of the input, which can cause out-of-bounds memory writes. That means the program can write data to an area of memory it shouldn’t touch.
Here’s a simplified snippet inspired by the underlying issue, not the actual code (since Mozilla's full source is extensive):
// Pseudo-code demonstrating the bug
void EncodeInputStream(nsIInputStream* inputStream) {
char buffer[1024];
uint32_t bytesRead;
// INCORRECT: No check to make sure read bytes do not overflow buffer
inputStream->Read(buffer, 4096, &bytesRead); // Reads too much
// ...Encoding logic...
}
The Read function tries to load more data than what buffer can hold. If this happens, you can overwrite parts of memory outside buffer — classic out-of-bounds write.
Be exploited by attackers to run their own code
In browsers and mail clients, this could mean a hacker taking control of your computer just by you viewing a malicious website or opening a bad email.
The most common way is to
1. Craft Malicious Input: Design a web page or email containing specific data that passes through the vulnerable inputStream handling code.
Trigger the Vulnerability: The app reads and encodes that data, hitting the memory bug.
3. Execute Malicious Code: If well-crafted, the attacker’s input can make the app jump to and run code placed by the attacker, leading to a full compromise.
While public "click-to-own" exploits are rare for this bug, real attackers probably exploit flaws like this through chain attacks — mixing with other browser vulnerabilities for bigger payloads.
How Was It Fixed?
According to Mozilla's security advisory:
References and More Information
- Mozilla Foundation Security Advisory 2023-06
- CVE Details page
- Bugzilla report (if made public) *(sometimes restricted for exploit safety)*
What Should You Do?
If you use Firefox or Thunderbird, update right away!
Go to “Help” > “About” > and let it check for updates. Up-to-date software is your best defense.
If you’re a developer:
Review all your input handling code for proper bounds checking.
- Always match your buffer sizes to your reads/writes.
Conclusion
CVE-2023-25732 is a classic example of how even small coding mistakes (like incorrect size checks) in complex systems can create big security risks. Patches are available — update now, and you’ll stay one step ahead of the bad guys.
If you’re curious about memory bugs, XPCOM, or want more in-depth help, check the links above or follow Mozilla’s security blog for updates!
Stay safe!
*Author: SecuritySimplified | Exclusively written for you*
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/08/2023 15:52:00 UTC