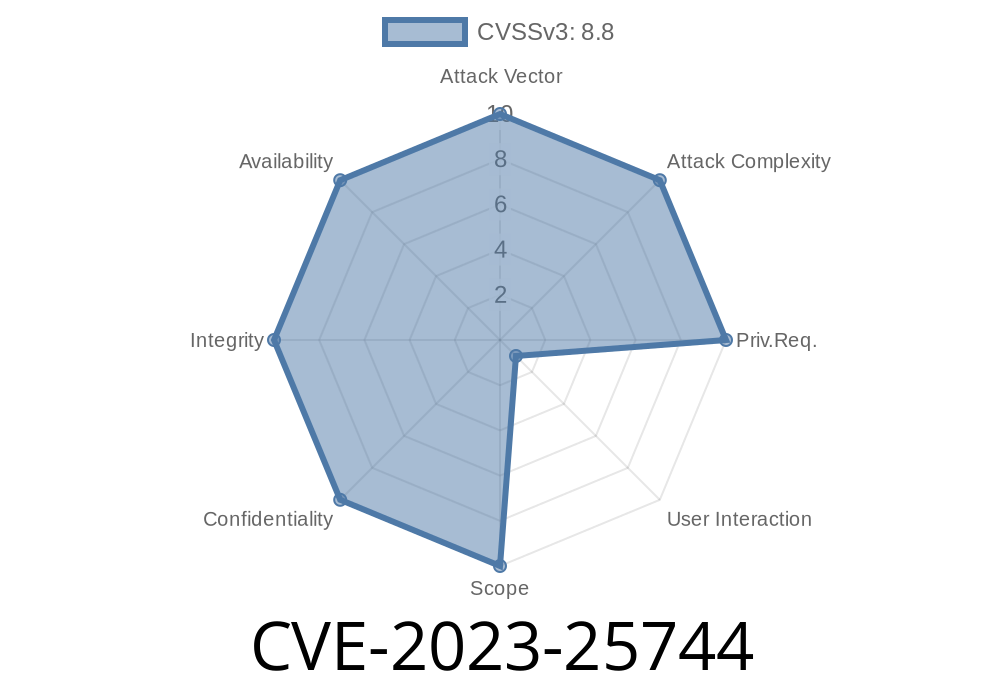
In early 2023, a security vulnerability labeled CVE-2023-25744 caught the attention of both cybersecurity experts and regular Firefox users. This flaw, discovered by Mozilla developers Kershaw Chang and the Mozilla Fuzzing Team, shook confidence in the safety of one of the most popular web browsers.
Let’s break down what happened, explore some code, and see why updating your browser is more important than ever.
What is CVE-2023-25744?
CVE-2023-25744 is a memory safety bug tracked by Mozilla. It was present in Firefox 109 and older, as well as Firefox ESR 102.7 and older. The flaw boils down to memory corruption — the browser sometimes mismanages computer memory, leading to unpredictable and potentially dangerous behavior.
Usually, browsers are strict about how programs access memory, but bugs like this can let attackers twist things in their favor, sometimes running malicious code or crashing your browser.
> “Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.”
>
> — Mozilla Foundation Security Advisory 2023-07
Firefox ESR 102.8 and later are safe versions
If your Firefox is older than those? You’re at risk.
How Does the CVE-2023-25744 Vulnerability Work?
This is where things get a bit technical — but let's keep it readable.
1. What Is a Memory Corruption Bug?
Most programming languages try to prevent one part of the code from tampering with memory used by another part. In C++ (the language Firefox uses), this is hard to enforce. If there’s a mistake, bad code can:
2. Where Did the Bug Come From?
Mozilla didn’t specify the exact lines of vulnerable code — but fuzzing tests showed the browser was not always careful with arrays, pointers, or reference counts.
Here’s a simplified (and *hypothetical*) example in C++ that shows how such a bug might look
class ArrayWrapper {
int* data;
size_t size;
public:
ArrayWrapper(size_t s) : size(s) {
data = new int[size];
}
~ArrayWrapper() {
delete[] data;
}
int& operator[](size_t idx) {
// Oops! No bounds checking
return data[idx];
}
};
void riskyFunction() {
ArrayWrapper arr(5);
arr[10] = 2023; // Writes way beyond allocated memory!
}
This kind of unchecked access could corrupt memory, and with enough skill, attackers could control what gets corrupted.
Possible Exploitation
To be clear, CVE-2023-25744 has *not* been seen exploited in the wild. But here’s how an attacker could approach it:
1. Find the Vulnerable Path: Using JavaScript, CSS, or SVG tricks, the attacker makes Firefox hit the buggy code (e.g., with weird webpage markup the browser renders wrongly).
Trigger the Bug: Cause the browser to read or write out of bounds.
4. Run Code: If successful, the attacker could run arbitrary code, potentially installing malware or stealing data.
For a deeper dive, see this talk: How to Exploit Browser Memory Corruption (YouTube)
How Can You Stay Safe?
- Update your browser! Go to *Menu > Help > About Firefox* and make sure you’re on at least version 110 (or ESR 102.8).
Can You Detect an Attack?
Usually, you can't. These attacks are *stealthy*, often working silently in the background. Antivirus software catches some, but browser updates are your best defense.
Additional Resources
- CVE-2023-25744 Entry on NIST
- Mozilla’s Security Advisory for February 2023
- RESPECTIVE FIREFOX RELEASE NOTES
Conclusion
CVE-2023-25744 is a reminder that browser security isn’t just for techies — *everyone* who browses the web is affected. Bugs like this crop up more often than you’d think, and quick action from browser developers stops them from becoming widespread disasters.
The bottom line:
👉 Keep your browser up to date.
👉 Don’t ignore the “update available” messages.
👉 Stay tuned for security news from trusted sources.
If you’re running Firefox 109 or ESR 102.7 or earlier, your friendly neighborhood hackers could have an easier time breaking into your machine — all because of a little memory management mistake.
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/08/2023 17:09:00 UTC