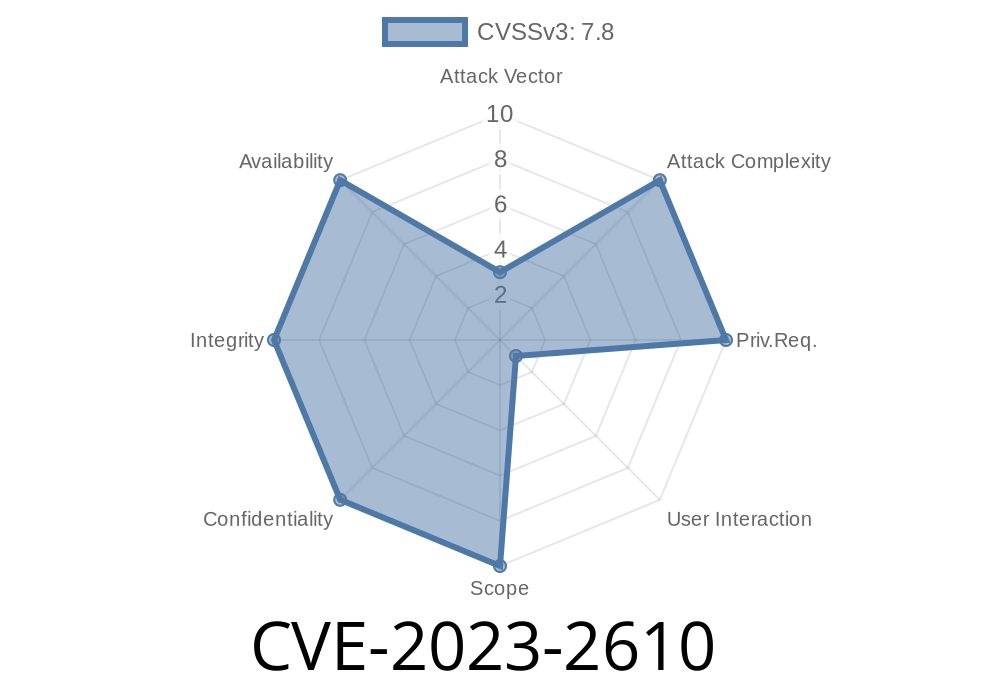
As a developer or system administrator, it's important to be aware of critical vulnerabilities that have the potential to compromise the security of your system. One such vulnerability, identified as CVE-2023-2610, was recently discovered in the popular text editor Vim, which is maintained on the GitHub repository vim/vim. In this post, we will dive deep into the details of this vulnerability, discuss its implications, and provide essential information about the exploit.
CVE-2023-2610 is an integer overflow or wraparound vulnerability that affects Vim versions prior to 9..1532. Before we dive into the specifics, let's quickly review what an integer overflow or wraparound is, for those who may not be familiar with the concept. In simple terms, an integer overflow is a type of arithmetic operation that results in a value outside the range of representable values for a given data type. This can lead to unexpected behaviors and, in certain cases, security vulnerabilities.
Now, let's take a look at the code snippet where the vulnerability exists in the Vim source code
// Located in src/memline.c, function ml_upd_block()
...
if (buf->b_ml.ml_locked_low !=
&& buf->b_ml.ml_locked_high !=
&& off < buf->b_ml.ml_locked_high
- && off + size >= buf->b_ml.ml_locked_low)
+ && (off + size >= buf->b_ml.ml_locked_low
+ || off + size < off))
In the original code, the conditional statement does not properly handle the case where the addition of off and size results in an integer wraparound. This oversight can lead to potentially dangerous memory corruptions when processing certain malformed input files.
To fix this vulnerability, the developers added an additional check to ensure that the result of the addition is greater than off. This can be seen in the modified code snippet shown above, where the original single-line condition has been replaced with a multi-line condition, which checks for both regular overflow as well as integer wraparound.
For a complete understanding of the issue and its fix, you can refer to the original commit on the Vim GitHub repository here: https://github.com/vim/vim/commit/3c4688f5d7c9a4cd319573c39cf362a66847cda
Exploit Details
While no known exploit is currently available, a talented attacker could craft a malicious input file that triggers this vulnerability and subsequently execute arbitrary code or compromise the affected system. As a result, it is crucial that users and system administrators update their Vim installations to version 9..1532 or later, to ensure their systems remain protected against this threat.
Moreover, developers integrating or using the Vim source code in their projects should also update their codebases to include the fix. It is essential to act quickly to prevent any potential exploit from affecting critical systems and causing significant harm.
In conclusion, CVE-2023-2610 represents a severe integer overflow or wraparound vulnerability in the Vim text editor, which can lead to dangerous consequences if left unpatched. By understanding the issue and ensuring your Vim installations and codebases are up-to-date, you can effectively safeguard your systems against this vulnerability.
Timeline
Published on: 05/09/2023 22:15:00 UTC
Last modified on: 06/12/2023 20:15:00 UTC