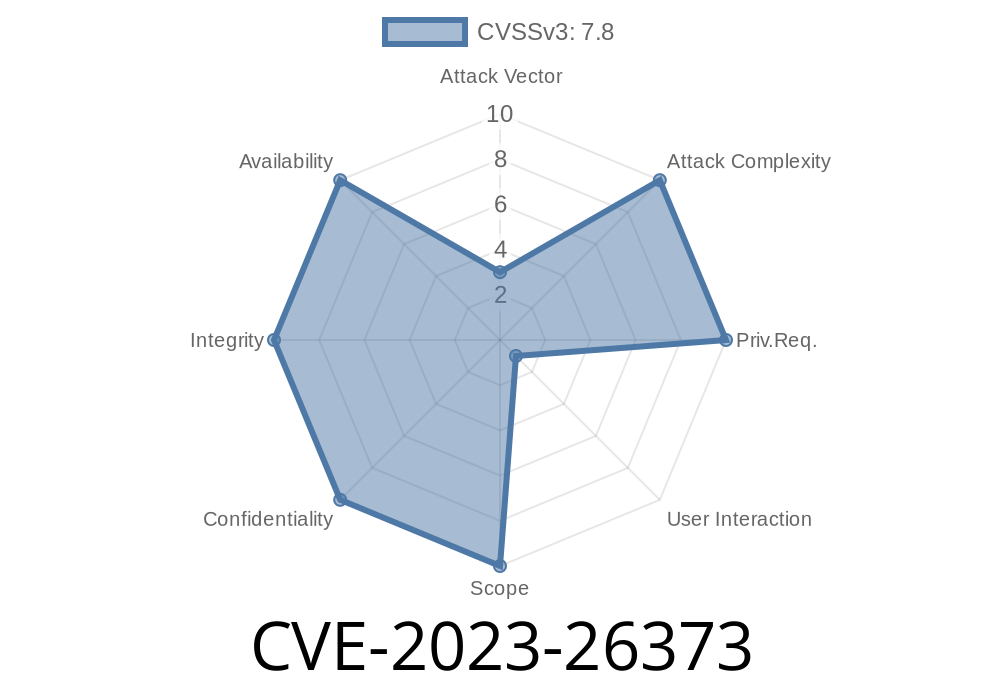
In March 2023, Adobe published a security update addressing a serious vulnerability—CVE-2023-26373—in Adobe Dimension, a popular 3D design software. This vulnerability affects version 3.4.8 and all prior versions, and could allow attackers to execute arbitrary code on a victim’s machine. Here, we’ll break down what this means, how the exploit works, show a simplified code snippet, and provide direct links to official sources. This article is crafted in simple language so anyone interested in security can follow.
What is CVE-2023-26373?
CVE-2023-26373 is an out-of-bounds write vulnerability. This means that malicious input can cause Adobe Dimension to write data outside the intended memory region, potentially overwriting critical program data or functions with attacker-controlled information.
Risk:
If an attacker convinces a victim to open a purposefully-crafted Dimension file (like .dn or imported asset), the attacker can hijack the program’s execution and run malicious code as the user.
Craft a Malicious File:
The attacker creates a specially tailored 3D model or project file which exploits the flaw in the way Dimension handles memory.
Send to Victim:
The victim is tricked (via phishing, social engineering, or fake download links) into opening the malicious file in Adobe Dimension.
Trigger the Bug:
When Dimension attempts to load the file, its code mishandles a buffer, leading to an out-of-bounds write. This can overwrite memory pointers or function addresses.
Execute Malicious Code:
The attacker’s code executes on the system with the same permissions as the user running Adobe Dimension.
> Note: Exploitation requires user interaction—the bug won’t trigger just by receiving the file, only by opening it with the vulnerable program.
Code Snippet: Simulating an Out-of-Bounds Write
Here’s a simplified example in C++ (for illustration only!) of the kind of programming error that could cause this issue:
#include <iostream>
#include <cstring>
void vulnerable_function(char *input) {
char buffer[100];
// Incorrectly trusting input length: dangerous!
strcpy(buffer, input); // No bounds checking!
std::cout << "Loaded: " << buffer << std::endl;
}
int main(int argc, char *argv[]) {
if (argc != 2) {
std::cerr << "Usage: prog <input>" << std::endl;
return 1;
}
vulnerable_function(argv[1]);
return ;
}
If the user provides a string longer than 100 characters, buffer will be overrun, leading to an out-of-bounds write—exactly the type of vulnerability found in CVE-2023-26373, though the real Dimension code is far more complex.
Possible Exploit Scenario
Imagine a malicious .dn project or model file with oversized or corrupted data fields. When opened, Adobe Dimension’s faulty code could process this file and accidentally copy too much information into a fixed-size buffer. Clever attackers position their “overflow” data so that it replaces critical instructions in memory, furthering control over the application.
In-the-wild Example
- Attacker crafts a .dn file with a payload hidden in a resource chunk (like a texture or mesh data array).
Victim opens the file; Adobe Dimension processes the chunk, triggering the overflow.
- Overwritten memory includes a function pointer or saved return address, which the attacker uses to redirect execution to their code (for example, opening a remote shell or running ransomware).
Adobe Security Bulletin:
APSB23-18 for Adobe Dimension (March 2023)
NVD Entry:
MITRE CVE Record:
CVE-2023-26373 at cve.mitre.org
Patch Download:
Conclusion
CVE-2023-26373 represents a classic but severe memory safety bug in a high-profile creative tool. While not an “automatic” attack, it only takes one bad file and one click to be compromised. Stay updated, stay cautious, and always verify the source of project files.
If you want to understand more or need help with secure workflows for creative teams, don’t hesitate to reach out to your security specialists.
Timeline
Published on: 04/12/2023 20:15:00 UTC