Published: June 2024
Adobe Acrobat Reader, the world's most popular PDF viewer, has been found vulnerable again. This time, a Use After Free bug, tracked as CVE-2023-26418, allows a remote attacker to execute arbitrary code just by tricking users into opening a booby-trapped PDF file. In this post, we’ll dig deep into this high-risk vulnerability, walk you through possible exploitation, and help you understand the risks with simple explanations.
What Is CVE-2023-26418?
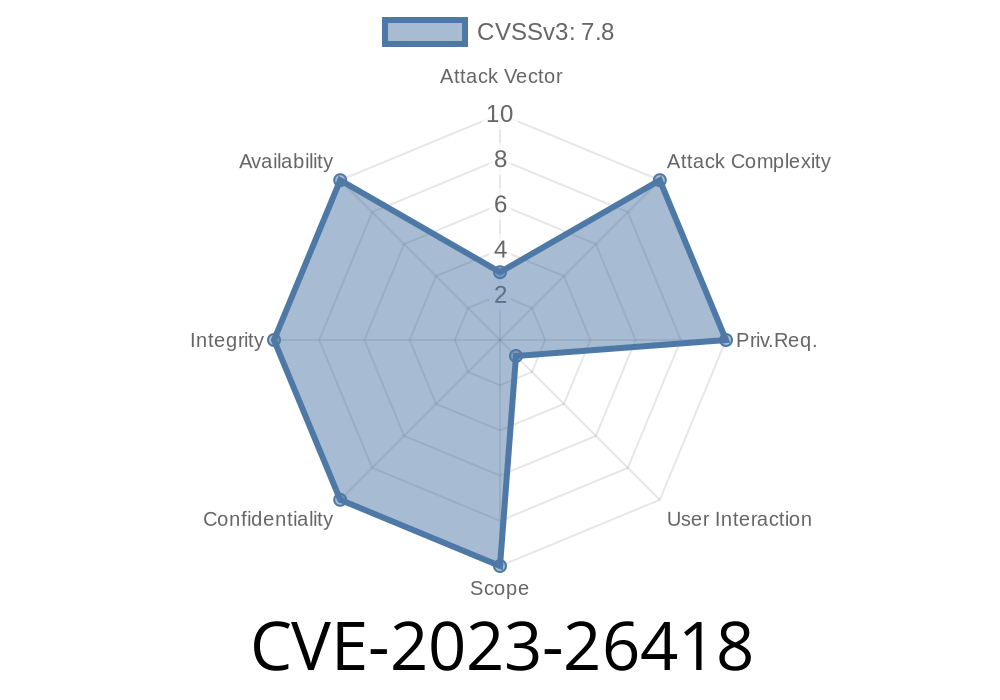
CVE-2023-26418 is a critical security flaw in Adobe Acrobat Reader, affecting versions 23.001.20093 and earlier and 20.005.30441 and earlier. This bug exists due to Use After Free (UAF) memory mismanagement, a common type of vulnerability that occurs when a program continues to use a chunk of memory after it has been freed.
Full remote code execution (RCE) in the current user’s context
User interaction is required: The user must open a specially crafted (malicious) PDF file for the exploit to work.
How Does Use After Free Work?
Let's quickly break down what Use After Free means. Imagine you have a book checked out from a library. You finish reading it and return it (free it). But for some reason, you keep referencing your old notes from that book (use it). If someone else checks out the same book and scribbles dangerous information in it, your notes now could mislead you or cause danger.
In software, memory works the same way. Once a program "returns" memory but continues to use it, a hacker can sneak in, mess with it, and gain control over the software.
The Core of the Vulnerability
The bug happens when handling certain objects or actions inside the PDF file. Attackers can carefully craft a PDF that, when opened, causes Acrobat Reader to free up (delete) an object while it’s still being used. Then, by manipulating memory, they can overwrite that space with their own malicious code. If Adobe Reader executes this code, the attacker gets control over your system.
Step 1: Crafting a Malicious PDF
A hacker creates a PDF file that includes embedded JavaScript. This JavaScript manipulates specific features in PDF, such as annotation APIs or form actions, to trigger the vulnerability.
Here’s an overly simplified snippet showing how malicious JavaScript inside a PDF might look
// Snippet found in some exploit samples
this.getAnnots({nPage: }).forEach(function (annot) {
// Detach annotation
this.removeAnnot(annot);
// Use annotation again (after removal)
annot.setProps({color: ["RGB", 1, , ]}); // Use After Free!
});
This code removes an annotation from the page (freeing it), but then immediately tries to use it again (setProps). Under the hood, this confuses Reader’s memory management and, in the vulnerable versions, can allow arbitrary code execution if memory is prepared just right!
Step 2: Smuggling Payload
The crafted PDF will carry additional code (payload), such as shellcode, that could run commands, steal data, or install ransomware. The attacker uses Heap Spraying techniques (filling memory with jump instructions or payloads) to ensure their code sits at the right spot when the Use After Free condition occurs.
Step 3: User Opens the File
The victim double-clicks the PDF. Acrobat Reader loads it, runs the malicious script, and triggers the bug. If successful, the malware code now runs with the same privileges as the user.
Impact: System takeover, data theft, further malware installation.
Note: There is no public report of exploits in wild as of June 2024, but similar vulnerabilities are popular entry points for phishing attacks.
Adobe released a fixed version in March 2023. Get the latest Reader version here:
References
- Adobe Security Bulletin APSB23-19
- National Vulnerability Database (NVD) entry for CVE-2023-26418
- MITRE CVE page
Conclusion
CVE-2023-26418 is a classic, yet highly dangerous vulnerability in trusted software millions rely on. It shows how a simple PDF file, with embedded scripts, can be used as a weapon. Always keep your software up to date and be cautious with file attachments.
Stay safe. Patch early, patch often. And don’t trust files from strangers!
Timeline
Published on: 04/12/2023 21:15:00 UTC
Last modified on: 04/21/2023 01:34:00 UTC