Published: June 2023
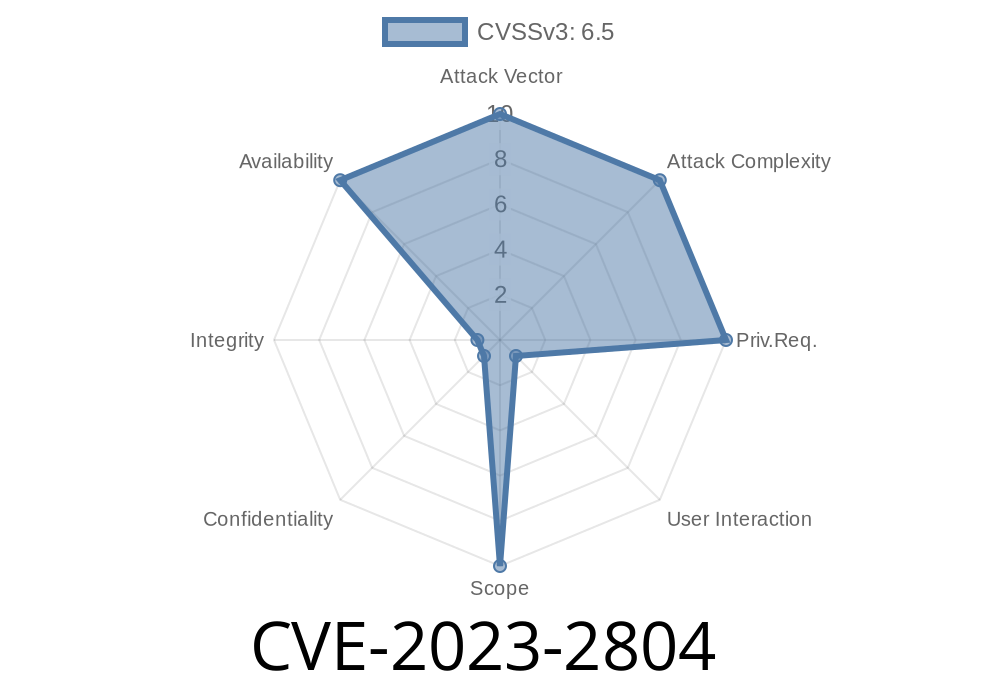
Severity: High
Affected Component: libjpeg-turbo
Vulnerable File: jdmrgext.c
Vulnerable Function: h2v2_merged_upsample_internal()
What is CVE-2023-2804?
CVE-2023-2804 is a significant security vulnerability discovered in the popular image processing library libjpeg-turbo. This vulnerability focuses on a heap-based buffer overflow inside the function h2v2_merged_upsample_internal() located in the jdmrgext.c file. An attacker can exploit this bug to crash an application or potentially execute arbitrary code by supplying a specially-crafted JPEG image.
This issue is exclusive to 12-bit data precision—a rarely used, but supported, mode for high-quality JPEG images. In the vulnerable case, the sample data type's possible values reach outside the valid range, causing unsafe memory writes when processing unexpected JPEG inputs.
Technical Background
libjpeg-turbo is widely used as a fast JPEG image decoding and encoding library. It is built into numerous popular applications and libraries, including image viewers, browsers, and camera software.
JPEG images can use various "precisions" (8, 12, or more bits per sample). Most consumer JPEGs are 8-bit, but the standard also allows 12-bit images (mainly used in scientific and medical imaging).
The h2v2_merged_upsample_internal() function is responsible for "upsampling"—converting lower-resolution chroma data back to full resolution in YCbCr images. This function uses the sample value directly as an array index when 12-bit precision is enabled. An invalid sample can overrun the allocated array, corrupting memory and causing crashes or security risks.
Out-of-range Sample Data:
An attacker crafts a 12-bit lossless JPEG image that contains sample values outside the –4095 range (the valid range for 12-bit JPEG samples).
Processing the Image:
When an application tries to decompress and upsample this image using libjpeg-turbo's merged upsampling, the sample value is used as an index or offset without proper bounds checking.
Buffer Overflow:
Because the value is out-of-range, the program writes or reads data outside the valid heap buffer. This results in a heap overflow, potentially causing a segmentation fault (crash) or enabling more serious exploitation.
Vulnerable Code Snippet
The detailed vulnerable section can be simplified as follows (based on upstream sources and security advisories):
// Simplified version; actual code is in jdmrgext.c
OUTTYPE *outptr = ... ; // Output buffer pointer
for (int i = ; i < width; i++) {
int sample = input_buffer[i];
// Vulnerable: sample can have invalid (>4095) values
outptr[i] = lookup_table[sample]; // Potential out-of-bounds access
}
Key Issue:
sample is assumed to be in a valid range (-4095) but isn't checked in the vulnerable code!
Proof of Concept Exploit
While a working exploit is highly dependent on the application using libjpeg-turbo, here's a general idea of how an attacker can trigger the vulnerability:
Create a 12-bit JPEG image with out-of-range sample data (>4095).
2. Supply this image to a vulnerable program (maybe an image viewer or web server) that uses libjpeg-turbo for decoding, with merged upsampling enabled.
3. Observe a crash (segmentation fault) or, in more advanced scenarios, exploit the overflow for code execution.
Here's how a PoC with djpeg (a common libjpeg-turbo utility) might look
# Generate a malicious 12-bit JPEG with custom software or hex-editing
./djpeg -bitdepth 12 -outfile out.ppm malicious.jpg
# This would cause djpeg to crash when parsing the out-of-range sample.
Wide Reach:
Applies to many open-source programs that rely on libjpeg-turbo (image viewers, web browsers, scientific software).
Who is Affected?
- Developers and maintainers of projects using libjpeg-turbo 3.. and earlier which support 12-bit JPEG images.
Users opening or processing untrusted 12-bit JPEG images with affected software.
Note: 8-bit JPEGs are not affected. Most consumer devices use 8-bit only, but scientific and medical tools could be at risk.
Upgrade libjpeg-turbo:
Fixed in libjpeg-turbo 3..1 and later. Always keep your libraries up to date!
Validate Input Data:
If you are a developer writing code that handles 12-bit JPEGs, always check the range of sample values before processing.
outptr[i] = lookup_table[sample];
<br><br>---<br><br>## References<br><br>- Official Security Advisory and Patch:<br>- CVE-2023-2804 at NIST NVD<br>- libjpeg-turbo Release Notes<br>- Upstream Bug Report & Discussion<br><br>---<br><br>## Summary<br><br><b>CVE-2023-2804 is a heap-based buffer overflow vulnerability</b> in libjpeg-turbo's h2v2_merged_upsample_internal()` when handling 12-bit JPEG images. A carefully-crafted image with out-of-range samples will crash or corrupt the memory of any application that decompresses it using merged upsampling.
If you use libjpeg-turbo in your project, upgrade to the latest version now, especially if you process 12-bit images!
---
*Stay safe, keep your libraries updated, and always validate user input—especially when it comes from images, videos, or other "safe-looking" data.*
Timeline
Published on: 05/25/2023 22:15:00 UTC
Last modified on: 06/06/2023 13:40:00 UTC