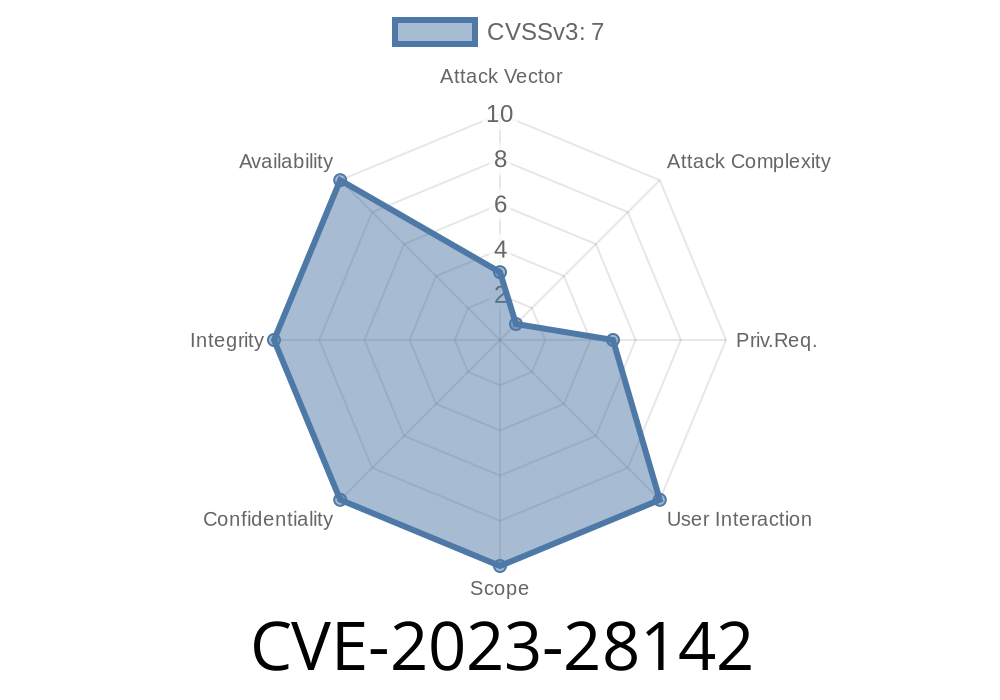
On March 22, 2023, Qualys published a critical advisory detailing a privilege escalation vulnerability—CVE-2023-28142—affecting their popular Cloud Agent for Windows. This bug—a race condition present in versions from 3.1.3.34 and before 4.5.3.1—allows attackers with limited access to gain SYSTEM privileges during agent uninstallation. This long-read post breaks it down in simple language: what it is, how it can be exploited, and what you should do.
What Is Qualys Cloud Agent?
In case you aren’t familiar, Qualys Cloud Agent is security software installed on company computers to help automate vulnerability management and compliance. Running as a SYSTEM service, it has deep access—so any bugs like this are serious.
CVE-2023-28142: The Basics
Vulnerability Type:
Local Privilege Escalation (LPE) via Race Condition during Agent Uninstall
Affected Versions:
Versions older than 4. are End of Life and not supported
Impact:
How Does the Attack Work?
This is a race condition attack, which means two or more processes are running at the same time and a security check can be bypassed if you time things right.
During the uninstall process, the agent performs actions as SYSTEM, including deleting files and registry entries. But, there's a gap where those files/paths can be swapped out (“race”) before deletion, letting someone place their own malicious code that will then run as SYSTEM.
Typical Exploitation Steps
1. Low-privileged attacker gains local access (for example, as a regular user or malware running on a user account).
Initiate agent uninstall
- Often, users can run uninstalls if the agent wasn’t tightly locked down, or the attacker can socially engineer/request it.
3. Monitor deletion actions: Watch for the uninstall process targeting specific files or directories (e.g., logs, temp files).
4. Replace file or path with a malicious executable in the brief window before deletion (using tools like fsutil, PowerShell Move-Item, or just manual timing).
5. Agent attempts to delete (or, as sometimes happens with poorly designed uninstallers, “process” the new file as SYSTEM).
Proof-of-Concept (PoC) Code Snippet
Below is a simple example simulating one method where an attacker could quickly swap a file during windows uninstallation.
# PowerShell PoC simulating a timing attack during uninstallation
$targetPath = "C:\ProgramData\Qualys\agent.log"
$evilExe = "C:\Users\User\evil.exe"
# Start watching for the file deletion
while (Test-Path $targetPath) {
Start-Sleep -Milliseconds 50
}
# When log is deleted, immediately write evil.exe in its place
Copy-Item $evilExe $targetPath
Write-Output "Evil binary placed at: $targetPath"
The attacker might use additional scripting or tools to watch for file operations more precisely (with Procmon, for example), but this idea shows how trivial such an attack can be if the timing is right.
Once their evil.exe is present, some poor uninstall script could launch or load that file as SYSTEM.
Severity and Real-World Impact
- Attacker Role: Needs local access (not remote); best for insider threats or post-compromise malware.
- Result: SYSTEM rights = total control over machine, ability to hide malware, tamper with logs, or pivot in the network.
- Affected Organizations: *Anyone using Qualys Cloud Agent on Windows with vulnerable versions (see above).* Especially dangerous in multi-user, server, or VDI environments.
Responsible Disclosure and Official Sources
Qualys Security Advisory:
https://www.qualys.com/alert/qualys-cloud-agent-windows-privilege-escalation/
CVE Details:
https://nvd.nist.gov/vuln/detail/CVE-2023-28142
Security Research (Third Party):
- Qualys End-of-Life Agent advisory
- Mitre CVE record
Monitor for suspicious uninstall activity: Use EDR or endpoint audit logs.
- Scan for CVE-2023-28142: Use security scanners or Qualys own detection tools.
Conclusion
CVE-2023-28142 is a textbook example of why uninstallers and update routines must be protected just as carefully as active security tools. Race conditions are tricky and can slip through QA—here it lets regular users grab the keys to the kingdom.
Don’t ignore this if you use or manage Qualys Windows agents!
Patch, audit, and restrict permissions now.
Stay safe—and always test updates before rolling them out everywhere!
References:
- Qualys Security Advisory
- NVD CVE-2023-28142
- Qualys Cloud Agent for Windows Release Notes
Timeline
Published on: 04/18/2023 16:15:00 UTC
Last modified on: 04/28/2023 13:18:00 UTC