In April 2023, Microsoft released a patch for a critical vulnerability tracked as CVE-2023-28275. This security flaw affects the WDAC OLE DB provider for SQL Server (also known as MSOLEDBSQL), and can allow attackers to remotely execute code on affected systems. If you use applications or scripts that connect to SQL Server through OLE DB, understanding this vulnerability—and how to mitigate it—is crucial.
What Is CVE-2023-28275?
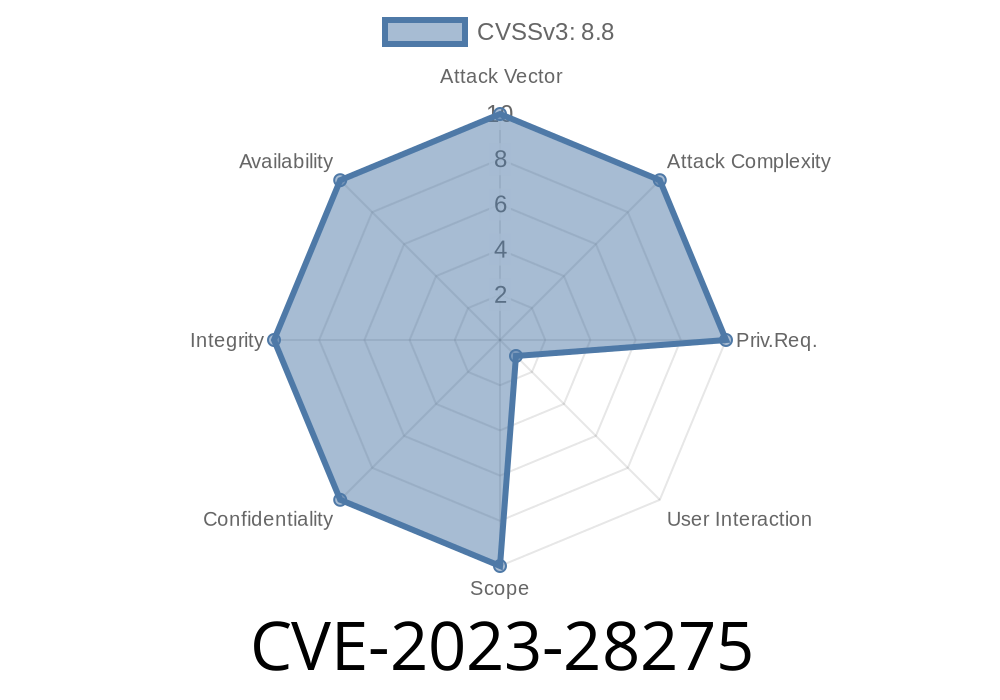
The CVE-2023-28275 vulnerability is classified as a remote code execution (RCE) that impacts the Microsoft OLE DB Provider for SQL Server (WDAC, MSOLEDBSQL). When an application uses the provider to connect to a SQL Server instance, specially crafted input from an attacker could lead to the execution of arbitrary code in the context of the application.
Severity: *Critical (CVSS up to 8.8)*
Affected Component: Microsoft WDAC OLE DB Provider for SQL Server
Attack Vector: Remote, through manipulation of SQL connection strings or data sent to the SQL server
Patched Version: MSOLEDBSQL 19.3. and later
You can read Microsoft’s official advisory here
- Microsoft Security Update Guide: CVE-2023-28275
Understanding the Vulnerable Surface
Most Windows applications (including custom enterprise tools and public frameworks) use OLE DB providers to connect to Microsoft SQL Server. When constructing database connections, users write a *connection string* – a set of parameters that tell the provider which server, database, and credentials to use.
Here’s a classic example in C#
string connString = "Provider=MSOLEDBSQL;Server=tcp:myserver.database.windows.net,1433;Database=mydb;User Id=myuser;Password=mypassword;";
OleDbConnection conn = new OleDbConnection(connString);
conn.Open();
In vulnerable versions, if an attacker controls any part of the connection string (for example, through user input, web parameters, or config files), they could craft malicious parameters that trigger unsafe behavior in the provider and get code execution. This is especially dangerous for web apps or automation scripts running with high privileges.
Proof-of-Concept Exploit
The full, working exploit code is not public, but based on available details, the exploitation follows these steps:
Input Manipulation: The attacker supplies or influences the connection string or SQL queries.
2. Trigger Vulnerability: Malicious parameters are used to exploit flaws in how WDAC OLE DB parses or executes connection initialization.
Example Connection String Exploit
Suppose a vulnerable app passes user-generated values into the connection string without any sanitation:
// Unsafe: Directly using user input
string userInput = Request.QueryString["server"];
string connString = $"Provider=MSOLEDBSQL;Server={userInput};Database=mydb;Trusted_Connection=yes;";
If userInput is set to an exploit payload (exact content would depend on the discovered bug), this could corrupt memory, invoke a DLL, or otherwise trigger RCE.
Sample Python Script to Test OLE DB Provider
You can use pyodbc (which uses OLE DB or ODBC under the hood) to simulate connection attempts and test for a vulnerable version:
import pyodbc
conn_str = (
"Driver={ODBC Driver 17 for SQL Server};"
"Server=tcp:attackerinput;Database=mydb;"
"UID=myuser;PWD=mypassword;"
)
try:
conn = pyodbc.connect(conn_str)
except Exception as ex:
print("Error:", ex)
Again, the real exploit would depend on the inner parsing logic in MSOLEDBSQL, which is best left to closed security research—not for public re-creation.
How to Fix CVE-2023-28275
The fix is simple:
Update the MSOLEDBSQL provider to version 19.3. or later
- Direct download for Microsoft OLE DB Driver for SQL Server
You can check your installed version like this (in PowerShell)
Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\MSOLEDBSQL" | Select-Object Version
References and Further Reading
- Microsoft Security Update - CVE-2023-28275
- Microsoft OLE DB Driver for SQL Server Download
- What is OLE DB? (Microsoft Docs)
Conclusion
CVE-2023-28275 reminds us that even deeply embedded components like OLE DB providers can harbor dangerous vulnerabilities. If you operate or develop apps connecting to SQL Server—especially on Windows—patch now and review all parts of your stack for unsafe input handling.
Timeline
Published on: 04/11/2023 21:15:00 UTC
Last modified on: 04/13/2023 01:09:00 UTC