---
*Published June 2024 · Exclusive Long Read · Written in Simple English*
On April 11, 2023, Microsoft disclosed a serious vulnerability impacting SharePoint Server, a platform used by thousands of organizations worldwide for collaboration and file sharing. This bug, assigned CVE-2023-28288, is a spoofing vulnerability. Attackers can abuse it to fool users and make malicious actions appear trustworthy. In this deep dive, we’ll break down what the vulnerability is, see how exploit works, and discuss easy ways you can stay safe.
What Is CVE-2023-28288?
This vulnerability lies in the way SharePoint Server processes HTTP requests. If an attacker crafts a specially designed URL and tricks a user into clicking it, they can spoof—basically fake—the identity or context of the request. This can lead to things like phishing attacks, session theft, or making malicious content appear legitimate.
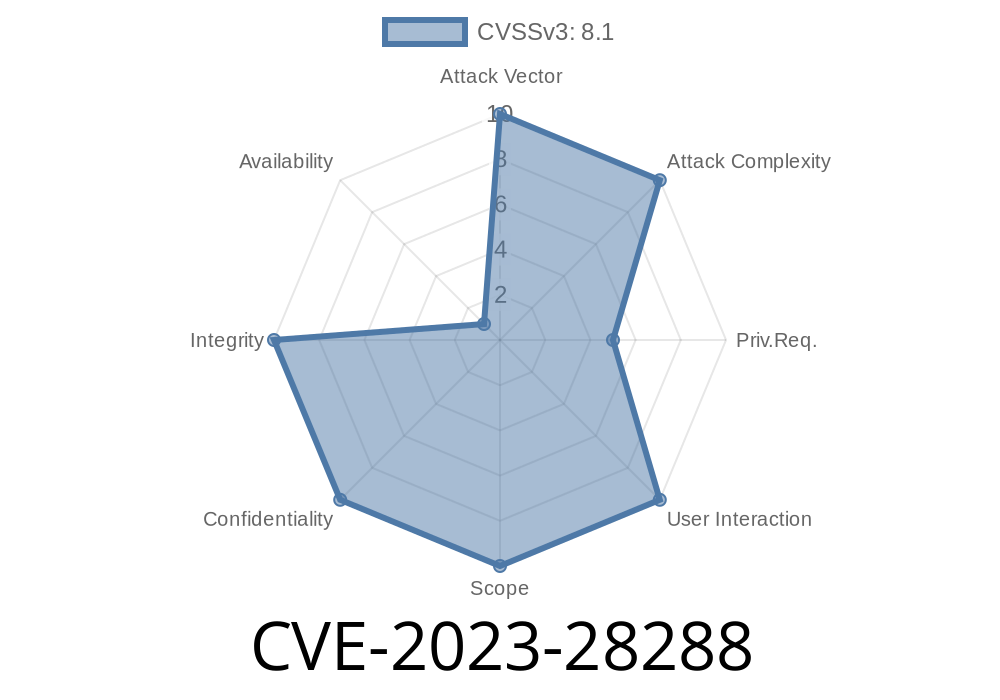
> Vulnerability Type: Spoofing (Impersonation)
>
> Affected Products: Microsoft SharePoint Server Subscription Edition, SharePoint Server 2016, and 2019
>
> Severity: Important
>
> Microsoft Security Advisory
Scenario: How the Attack Works
Let’s imagine an attacker wants to steal credentials or sensitive information from users in a company.
Attacker uploads a malicious file or creates a special link
2. Attacker crafts a spoofed URL pointing to a legitimate SharePoint resource, but with hidden intentions
Victim receives this link via email, SMS, Teams, or another messaging platform
4. Victim clicks the link and is redirected to attacker-controlled content that looks like part of their company’s SharePoint
If the attacker sets their trap right, even savvy users might be fooled because everything looks and feels “official.”
Simple Exploit Example
Here’s a proof-of-concept (PoC) showing how the attack might play out in real life.
Step 1: Prepare a Web Server
Let’s say the attacker controls evil.com. They set up a phishing page that looks like the real SharePoint login.
Step 2: Craft the Exploit Link
Suppose the vulnerable SharePoint site is at https://sharepoint.company.com. The attacker discovers that certain SharePoint endpoints reflect (repeat back) URLs without properly validating them. With a parameter like ReturnUrl, attackers can inject their fakery.
Example malicious URL
https://sharepoint.company.com/_layouts/15/Authenticate.aspx?ReturnUrl=https://evil.com/fake-login
When the victim clicks, SharePoint processes the ReturnUrl parameter, and will redirect the user to a page chosen by the attacker.
The attacker might email a message
> *"Hi, you need to update your HR documents. Please login here: Click here"*
Victim trusts the company domain—but actually gets diverted to evil.com/fake-login, a fake SharePoint login screen, where credentials and tokens can be harvested.
Code Snippet: Detecting and Preventing the Exploit
System admins can check server logs for suspicious redirect patterns. Here’s a simple Python script that scans your SharePoint logs for “outbound” redirects:
import re
with open('SharePointLogs.txt') as logfile:
for line in logfile:
match = re.search(r'ReturnUrl=(https?://[^\s]+)', line)
if match:
url = match.group(1)
if not url.startswith("https://sharepoint.company.com";):
print(f"Suspicious redirect found: {url}")
*This script looks for URLs in your logs where the ReturnUrl doesn’t match your real domain.*
Protection and Patch Advice
Microsoft has released a fix—apply it now!
Download and install the patches provided in their security update guide.
> Mitigation Steps
> - Never disable security validation checks on your SharePoint server
> - Warn staff to never input credentials into “unusual” pages, even if the link looks official
> - Set up outgoing URL filtering/alerts for suspicious redirects
> - Monitor logs for abnormal login or redirect activity
Microsoft Security Update:
Technical Analysis:
Original Patch Details:
Microsoft Patch Tuesday April 2023
Conclusion
CVE-2023-28288 isn’t a headline-grabber like some zero-day exploits, but it’s a classic and dangerous trick—redirecting users to attacker-controlled sites while making everything look official. This attack can lead to business email compromise, credential theft, and further infections. With a simple email and a malicious link, attackers don’t need to do high-tech hacking—just social engineering and stolen branding.
Patch your SharePoint servers now, warn your users, and keep an eye on redirects. Stay safe!
*If you found this useful, share it with your IT team. Knowledge saves networks!*
Timeline
Published on: 04/11/2023 21:15:00 UTC
Last modified on: 06/17/2023 01:15:00 UTC