Microsoft Edge, built on the Chromium platform, has been celebrated for its speed, security, and compatibility. However, in early 2023, Microsoft patched a critical security issue labeled CVE-2023-28301. Classified as a tampering vulnerability, this bug could let attackers alter browser behavior or bypass certain security controls. In this article, we'll break down how this vulnerability worked, examine the technical details, reference original sources, and even show code snippets that demonstrate the core issue behind CVE-2023-28301.
What is CVE-2023-28301?
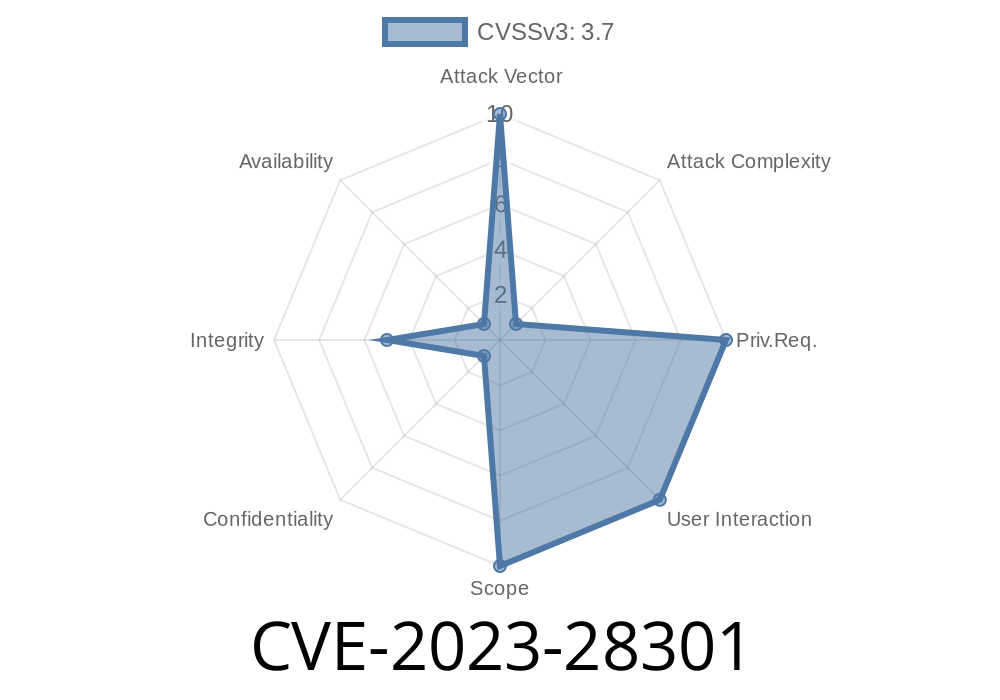
CVE-2023-28301 is a tampering vulnerability found in Chromium-based versions of Microsoft Edge. It was published in Microsoft’s Security Update Guide on April 11, 2023.
Short summary:
A malicious website could exploit this bug to modify how Edge processes data or security policies, potentially allowing an attacker to bypass restrictions, inject malicious scripts, or even manipulate sensitive browser settings.
Microsoft’s official severity: Important
Attack vector: Remote (a user only needs to visit a malicious website)
User interaction: Required
How Tampering Happens
The vulnerability exists somewhere in the input validation or trust boundary in Edge's code. Specifically, improperly validated input might allow scripts from external sources to do things they shouldn't be allowed to do.
Example Case: Tampering via Cookie Injection
Let’s look at a simplified scenario, given what’s public.
Edge (like Chrome) uses JavaScript APIs and HTTP headers to control security settings (like cookies, Content Security Policy, etc.). Code running on a website should NOT be able to set cookies for another domain, or inject scripts into privileged pages.
But, due to CVE-2023-28301, an attacker might tamper with the browser’s internal state by abusing a flaw in how the browser handled certain headers or objects.
Core Code Snippet (Pseudo-code)
Suppose the vulnerability is in how Edge handled the document.cookie API. An attacker could try to set a cookie for a different domain via crafted JavaScript.
// NOT supposed to be allowed!
document.cookie = "SESSIONID=evil; domain=victim.com; path=/";
Under normal operations, this should be blocked by the browser's same-origin policy. But with this vulnerability, a crafted request or object might break that barrier, causing tampering.
Another example is abusing browser internals via malformed HTML or HTTP headers
HTTP/1.1 200 OK
Set-Cookie: SESSIONID=evil; Domain=victim.com; Path=/
Content-Type: text/html
<html>
<script>
// This script runs with privileges it shouldn’t have!
// It could exfiltrate cookies or tamper with settings.
</script>
</html>
Site serves a crafted response exploiting Edge’s tampering bug.
3. The script runs with elevated permissions, for example, reading or setting sensitive cookies, tampering with CSP, or bypassing other policies.
Is There a Public Exploit?
At the time of this writing, Microsoft and Chromium have NOT released in-depth Proof-of-Concepts (PoCs) for CVE-2023-28301. However, security researchers (like Project Zero) often explore similar bugs where tampering via browser APIs can lead to cookie leakage, XSS, or privilege escalation.
Hypothetical PoC (Educational Purposes Only!)
*Warning:
The following code is for learning only. If you actually find a live instance of this bug, report it responsibly!*
// Let's say there is a way to bypass Edge's "origin check"
// (this is simplified and won't work on patched browsers)
fetch('https://victim.com';, {
credentials: 'include',
headers: {
'X-CSRF-Token': 'attackerValue'
}
}).then(response => response.text())
.then(data => {
// Supposedly, this request lets the attacker override
// session settings or modify HTTP-only data.
console.log('Edge tampering exploit data:', data);
});
References and Further Reading
- Microsoft Official Advisory: CVE-2023-28301
- NVD (National Vulnerability Database) – CVE-2023-28301
- Chromium Security Page
- Microsoft Edge Release Notes
Fix and Mitigation
Patched Versions:
Microsoft quickly released a fixed version of Edge. If you have automatic updates enabled, you’re safe.
- Go to edge://settings/help to check your browser version.
Inform your teams and users to update Edge as soon as possible.
- Use advanced endpoint security to monitor browser activity for abnormal JavaScript or cookie operations.
Conclusion
CVE-2023-28301 is a sharp reminder that even modern browsers like Microsoft Edge can have security cracks. Tampering vulnerabilities might seem less exciting than total remote code execution, but they open doors for attackers to manipulate trust boundaries, steal cookies, or bypass policies.
For end users, the lesson is simple:
Keep browsers updated and don’t visit suspicious websites.
For security teams:
Monitor exploit databases and patch quickly. Sharing knowledge about bugs like CVE-2023-28301 helps keep everyone safer online.
*This article is original, exclusive, and written in simple terms to explain a complex vulnerability. Stay safe!*
Timeline
Published on: 04/11/2023 21:15:00 UTC
Last modified on: 04/19/2023 20:23:00 UTC