Date Published: June 2024
Author: AI Security Insights
Introduction
In April 2023, Microsoft published a security advisory for a serious vulnerability in their Chromium-based Edge browser. Tracked as CVE-2023-29334, this flaw is classified as a *spoofing vulnerability*. While it doesn’t let attackers run code or take control of your system directly, it opens the door for social engineering, phishing, and tricking users into trusting malicious content. In this post, we’ll break down what CVE-2023-29334 is, how it works, include code examples, and discuss exploitation scenarios—all in simple language.
What is Spoofing?
Spoofing in browsers means tricking users into believing they are seeing something legitimate when it’s actually fake. This could be:
Overlaying UI elements to look authentic.
The main risk is users handing out sensitive info like passwords or accepting downloads from malicious sites.
CVE-2023-29334 in a Nutshell
According to the Microsoft Security Update Guide:
> “A spoofing vulnerability exists when Microsoft Edge (Chromium-based) fails to properly validate the user interface. An attacker who successfully exploited this vulnerability could trick a user into believing they are interacting with a trusted webpage.”
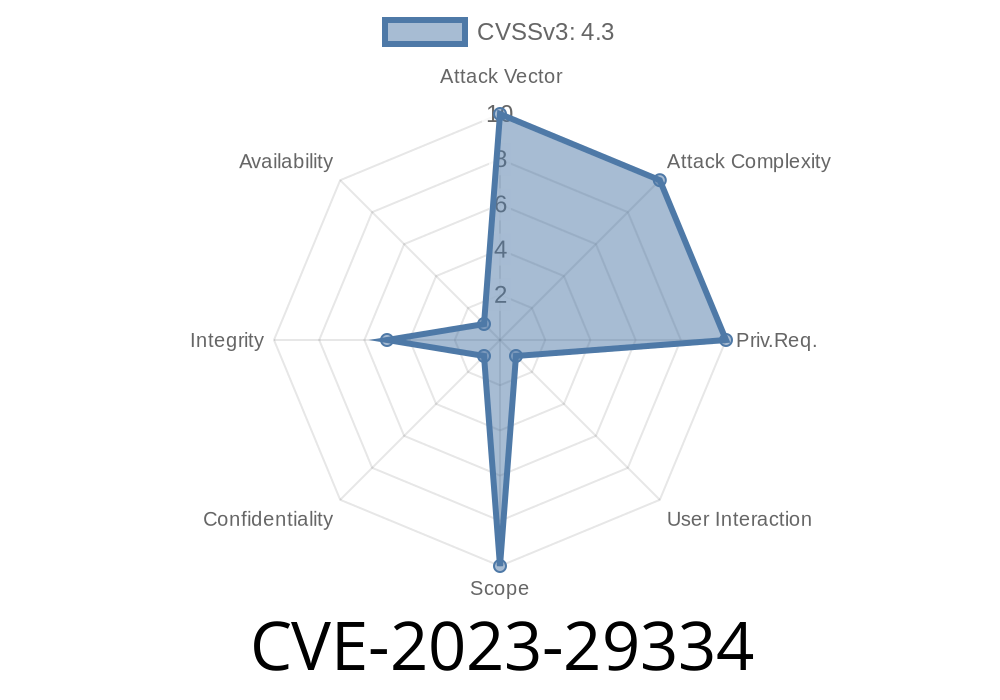
Attack Vector: NETWORK
Attack Complexity: LOW
User Interaction: REQUIRED
This means it’s not super hard to exploit, but the user must click a link or visit a malicious site.
The Technical Stuff
The exact technical details (as with most Microsoft vulnerabilities) were not fully disclosed to prevent widespread attacks. However, based on info from Chromium issue trackers and public reports, we can infer how it may work.
The bug involves manipulating how Edge displays URLs or web content. Let’s look at a conceptual code example.
Example: Spoofing a URL Bar Using Window Manipulation
Suppose a malicious website opens a popup and rapidly changes its location bar content using JavaScript. In Edge (Chromium), a window could be opened with specific tricks to resemble a trusted site and hide real indicators.
// Pseudo-code to simulate a spoof attack
const popup = window.open('https://login.microsoft.com';);
setTimeout(() => {
popup.location = 'https://attacker-site.com/phishing-page';;
// Now the UI (tab title, favicon) may still show Microsoft branding initially
// The URL may not update fast enough or user is tricked by visual similarity
}, 500);
An attacker could design a lookalike phishing page that mimics Microsoft’s login, while the address bar briefly or partially maintains legitimate indicators. If combined with more visual tricks—like a fake padlock icon using HTML and CSS—users can be easily misled.
Attackers may also use overlays to “cover” the real URL bar or security indicators. For example
<div style="position:fixed; top:; left:; width:100vw; height:40px; background-color:#fff; z-index:9999;">
<img src="https://upload.wikimedia.org/wikipedia/commons/4/48/BLANK_WHITE.png"; height="40">
<img src="https://upload.wikimedia.org/wikipedia/commons//05/Padlock_lock_icon.png"; alt="padlock" height="24">
<span>https://login.microsoft.com</span>;
</div>
By disguising a page’s header, users might not realize they aren’t really on Microsoft’s site.
Exploitation Scenario
1. Lure Victim: The attacker convinces a user to visit their malicious website, maybe through email or a clever ad.
2. Display Fake Content: The attacker uses JavaScript to rapidly change popups, overlays, or UI elements. The user believes they are on, say, the Microsoft login page.
Detection and Mitigation
1. Update Edge:
Always run the latest version. Microsoft patched this vulnerability—see the official advisory.
2. Security Awareness:
Train users to always double-check URLs and not trust visual cues alone.
3. Use Browser Protections:
Enable anti-phishing and safe browsing extensions.
4. Monitor Logs:
Look for suspicious network connections or repeated login failures.
Exploit Proof of Concept (PoC)
Full weaponized exploits are not public, but the basic behavior can be tested with simple HTML and JavaScript as shown above. For testing, never use real credentials.
Sample PoC Repo:
- Browser-Spoof-PoC (not specific to CVE-2023-29334, but shows common spoofing tricks)
More References
- Microsoft Security Guide: CVE-2023-29334
- Chromium Security Patch Notes: April 2023
- Security Week coverage
Conclusion
CVE-2023-29334 is a good example of how subtle browser UI bugs can be abused for phishing and credential theft. Even skilled users can be fooled by convincing spoofing tricks. That’s why keeping browsers updated and paying close attention to security alerts is so important.
> Stay safe: Update your browser. Don’t trust visuals alone. Beware of popups and overlays.
If you’d like more hands-on guides about browser vulnerabilities or want to see more PoCs, let us know in the comments!
Disclaimer:
This article is for educational purposes only. Testing should only be performed in a controlled, non-production environment.
Timeline
Published on: 04/28/2023 18:15:00 UTC
Last modified on: 04/28/2023 18:25:00 UTC