---
Introduction: What is CVE-2023-29362?
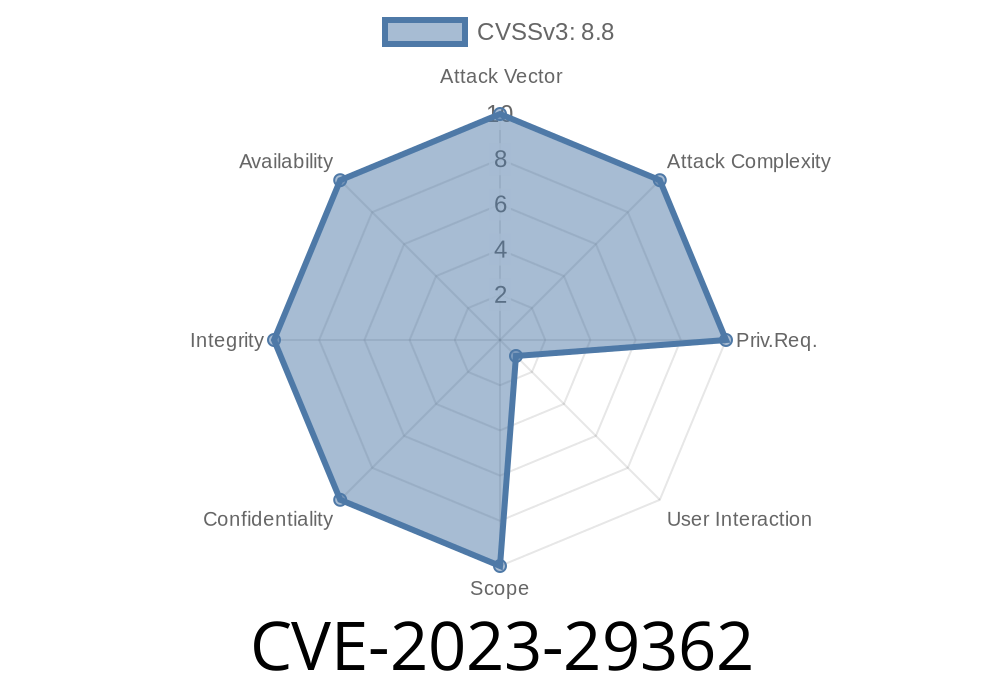
CVE-2023-29362 is a Remote Code Execution (RCE) vulnerability affecting Microsoft Windows Remote Desktop Client. This means an attacker can run malicious code on a victim’s machine just by making them connect to a compromised RDP server. If exploited, attackers could gain the same user rights as the client—potentially taking over the system.
*This “client-side RDP bug” is a reminder that not only servers, but even users connecting can be at risk when using untrusted remote desktops.*
All content below is presented to raise awareness and educate about this security flaw—the goal is to help you understand, not encourage misuse.
Technical Deep Dive: What’s Vulnerable?
When you use the Remote Desktop Client (mstsc.exe) to connect to another computer, Windows parses data sent by the server, such as clipboard data, fonts, or even drives. Vulnerabilities in this parsing logic can let a malicious server send special packets that trigger memory corruption, allowing code execution.
If you RDP _into_ a remote system from an unpatched Windows computer, you’re at risk.
- (Full Microsoft advisory: CVE-2023-29362 - Microsoft Security Guide)
How the Exploit Works
Scenario: An attacker controls an RDP server or can man-in-the-middle (MitM) your connection. They send specially crafted data that abuses the vulnerable parsing routine on your client.
Server delivers malicious data (usually abusing “clipboard redirection” or similar features).
3. The vulnerable client code improperly processes that data (e.g. out-of-bounds write or use-after-free).
Let's see a simplified mock-up (educational only; not a fully working exploit)
Suppose the bug is in processing “clipboard” data.
Server-side Python Code (using RDP libraries for demonstration)
import socket
def serve_rdp(port):
server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server.bind(("...", port))
server.listen(1)
print(f"[*] Malicious RDP server running on port {port}")
conn, addr = server.accept()
print(f"[+] Got client from {addr}")
# Send malformed clipboard packet
# This is just a conceptual representation
evil_clipboard_payload = b"\x43\x4C\x49\x50" + b"\x90" * 100 # Overly long, will corrupt memory
conn.send(evil_clipboard_payload)
conn.close()
if __name__ == "__main__":
serve_rdp(3389)
Note: Real-world exploits are more complex: they need to properly speak the RDP protocol and craft payloads according to the vulnerable function.
Known Exploit Tools & References
- As of now (2024), no public weaponized exploit script is available, but labs have demonstrated viability.
- CVE-2023-29362 on NVD
- Microsoft’s Patch Tuesday writeup: Microsoft Security Update Guide Entry
- Initial technical write-ups by researchers (when/if available): *Search Twitter/X for CVE-2023-29362 or security blogs*.
How to Stay Safe
Patch Immediately:
Microsoft has patched the issue in June 2023 updates. Upgrade your systems.
Avoid Untrusted RDP Servers:
Never connect to random “free” remote desktops or test unknown hosts.
Network Segmentation:
Limit RDP traffic using firewalls or VPN.
Security Basics:
Use strong passwords, enable NLA (Network Level Authentication), and monitor logs for suspicious client RDP activity.
Conclusion
CVE-2023-29362 is a strong reminder that even “client-side” tools like RDP can put your PC at risk, letting hackers run arbitrary code as soon as you connect to the wrong machine. Patch now and be careful who you RDP to!
References and More Information
- Microsoft CVE-2023-29362 Security Guide
- NIST NVD Entry for CVE-2023-29362
- General RDP Security Best Practices - Microsoft Docs
Timeline
Published on: 06/14/2023 00:15:00 UTC
Last modified on: 06/20/2023 20:00:00 UTC