---
Introduction:
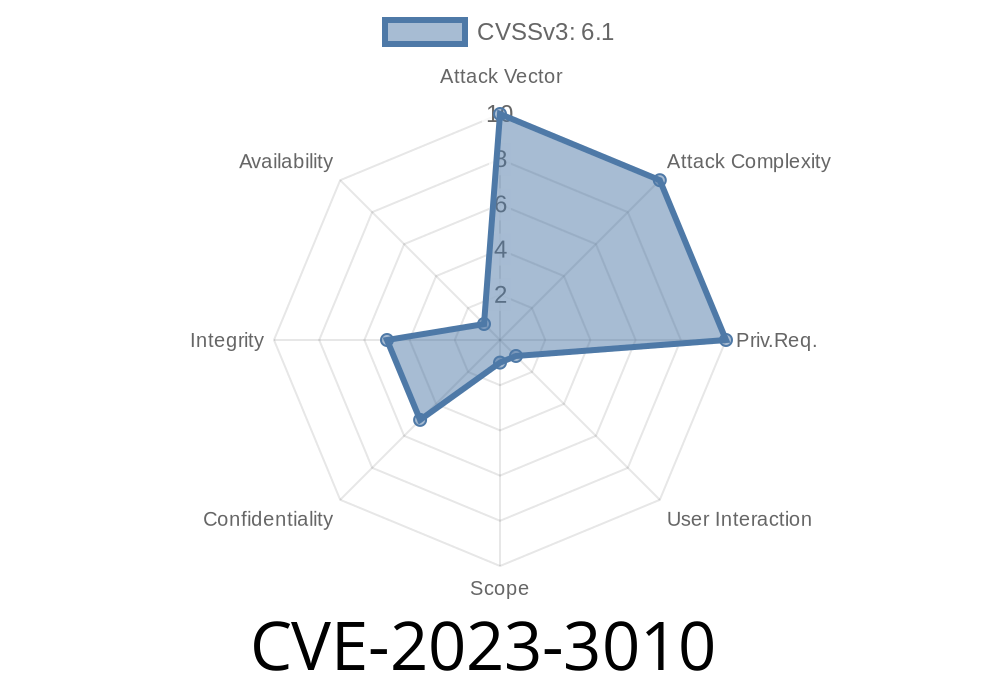
In today's world, with the increasing reliance on technology, it becomes crucial to maintain the security of our systems and data. One such critical security vulnerability has been discovered in the popular open-source platform, Grafana - specifically in the WorldMap panel plugin versions before 1..4. This vulnerability is termed as CVE-2023-3010.
Grafana is an open-source platform widely used for monitoring and observability. With the ability to query, visualize, and understand metrics, Grafana serves as a powerful tool for various purposes ranging from analytics to troubleshooting. However, the presence of security vulnerabilities can lead to risks and other complications, which we will explore in this post.
In this detailed long-read post, we are going to dive deep into the nature of this vulnerability, discuss the code snippet which causes it, and provide an understanding of its potential exploits.
Vulnerability Overview:
The WorldMap panel plugin in Grafana, versions before 1..4, contains a DOM-based Cross-Site Scripting (XSS) vulnerability. This vulnerability allows an attacker to inject malicious JavaScript code into the page that is executed in the context of the user’s browser. This can lead to various attacks such as stealing sensitive information, session hijacking, and defacement of the web application.
The Original References:
The vulnerability was first reported through a public advisory, and you can find the original references here:
- CVE-2023-3010 - National Vulnerability Database (NVD)
- Grafana Labs Security Advisory
Code Snippet Explained
A detailed inspection of the plugin's codebase reveals the vulnerable code snippet in the "worldmap_ctrl.ts" file, which triggers the DOM-based XSS vulnerability. For educational purposes, here's a simplified version of the problematic code:
function displayPoint(x, y, locationName) {
var tooltipContent = getTooltipContent(locationName);
var tooltipElement = document.createElement('div');
tooltipElement.innerHTML = tooltipContent;
document.body.appendChild(tooltipElement);
}
function getTooltipContent(locationName) {
return '<h4>' + locationName + '</h4>';
}
The displayPoint function is responsible for showing a tooltip on the map when a user hovers over a specific location. The vulnerable part here is that the locationName value is injected directly into the innerHTML property of the tooltip element without proper sanitization or escaping. This means that an attacker can craft a malicious locationName that includes JavaScript code that will be executed when displayed as a tooltip.
Exploit Details
Considering the earlier code snippet, an attacker could potentially exploit this vulnerability with the following steps:
`
2. Add this malicious location to the WorldMap panel, either through importing data to Grafana or by exploiting another vulnerability to modify the application data.
3. Wait for a user with higher privileges (e.g., an administrator) to hover over the crafted location on the map. When this happens, the malicious JavaScript code will be executed in the context of the user's browser, leading to a possible theft of sensitive information, session hijacks, or other harmful consequences.
Mitigation and Recommendations
The severity of this vulnerability highlights the importance of keeping software up-to-date and regularly reviewing the security posture of the technologies we use. To protect against this specific vulnerability, users should update the WorldMap panel plugin in Grafana to version 1..4 or above, as this version contains a fix for the vulnerability.
Additionally, it is essential to adopt security best practices, such as employing secure coding guidelines, conducting regular security audits, and encouraging responsible disclosure of vulnerabilities. These practices can significantly improve the overall security posture of any organization.
In conclusion, vulnerabilities like CVE-2023-3010 in widely-used platforms emphasize the need for relentless vigilance and proactive measures in the cybersecurity landscape. By staying informed and taking necessary precautions, we can collectively work towards a safer, more secure digital world.
Timeline
Published on: 10/25/2023 18:17:00 UTC
Last modified on: 10/31/2023 18:09:00 UTC