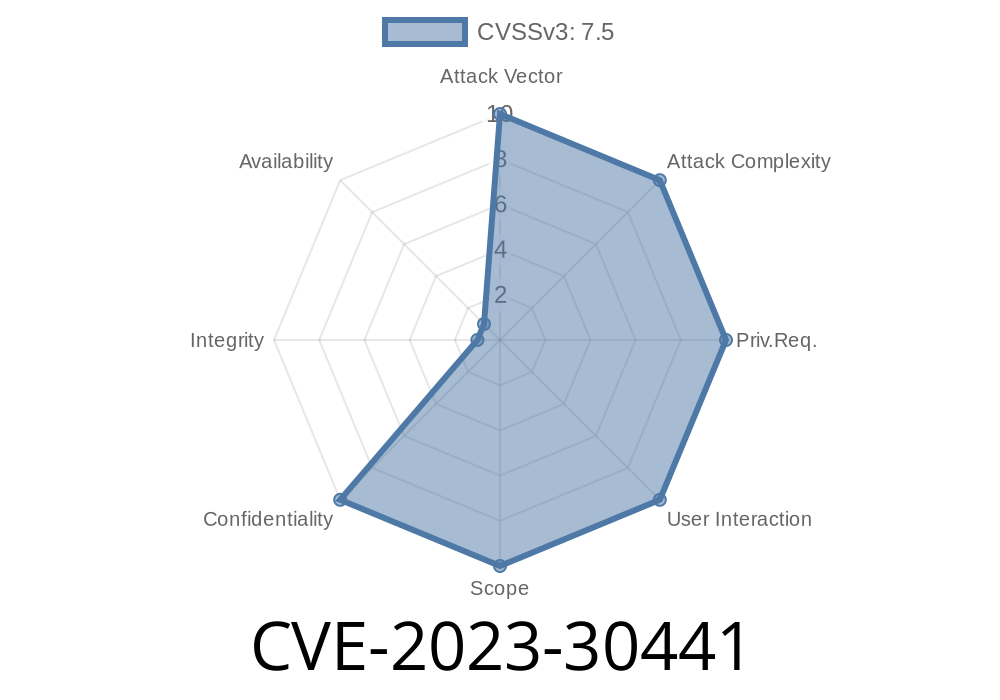
IBM Runtime Environment, Java Technology Edition (IBM JRE) is deeply embedded in many business and enterprise systems. If you’re running it, especially the IBMJCEPlus or JSSE security components from versions 8..7. to 8..7.11, you need to know about CVE-2023-30441 — a vulnerability that could leak sensitive information under certain conditions.
Let’s break down what this flaw is, how it works, and what you should do if you’re affected.
What is CVE-2023-30441?
CVE-2023-30441 is a vulnerability ID assigned to a flaw in the IBM Java runtime (JRE). Specifically, it impacts:
Versions 8..7. through 8..7.11
The issue occurs when a specific configuration, combined with certain internal mistakes in cryptographic processing, leaks information that should remain secret. In cyber-speak, this is an “information disclosure” flaw.
IBM’s Security Advisory:
https://www.ibm.com/support/pages/node/6918138
NVD Record:
https://nvd.nist.gov/vuln/detail/CVE-2023-30441
IBM X-Force Exchange:
https://exchange.xforce.ibmcloud.com/vulnerabilities/253188
What Actually Leaks?
While the official details are a bit limited (to protect companies during patch rollout), the gist is:
- If a developer uses insecure default or custom configuration for certain cryptographic or TLS operations,
And the application is running with a vulnerable IBMJCEPlus or JSSE,
- An attacker could extract internal cryptographic data (example: process memory, encryption keys, or other secrets) by sending specially crafted requests or observing traffic.
It does not mean your data is directly stolen over the network. It’s more subtle. This weakness may help an attacker escalate attacks, decrypt private communications, or impersonate services.
Here’s a simplified scenario to demonstrate how an attacker might take advantage of this flaw
import javax.net.ssl.*;
import java.io.*;
import java.net.*;
public class WeakTLS {
public static void main(String[] args) throws Exception {
SSLContext ctx = SSLContext.getInstance("TLS");
// Insecure: using default config, vulnerable logic below
ctx.init(null, null, null);
SSLSocketFactory factory = ctx.getSocketFactory();
try (SSLSocket socket = (SSLSocket) factory.createSocket("localhost", 443)) {
socket.startHandshake();
// Data exchanged over this socket might leak internal secrets under CVE-2023-30441 circumstances
BufferedWriter out = new BufferedWriter(new OutputStreamWriter(socket.getOutputStream()));
out.write("HELLO SERVER\n");
out.flush();
}
}
}
If you’re using a vulnerable IBMJCEPlus or JSSE, and the system is misconfigured, this kind of handshake (even if you think it’s secure) could allow a crafty threat actor to extract encryption keys or sensitive info, especially if they can interact repeatedly with your service.
CVE-2023-30441 isn’t a bug that “just shows up.” The combination includes
- Running IBM Java 8..7. – 8..7.11 (specifically those with IBMJCEPlus and/or JSSE)
- Weak or default cryptographic settings — not using strong ciphers, or failing to set up custom TrustManagers/KeyManagers
Possible memory management flaws or error-handling bugs in these IBM modules
These conditions together create a risk of information exposure.
How To Protect Yourself
Upgrade:
IBM recommends upgrading to the latest version
- IBM Java Technology Edition release download page
Avoid trusting all certificates (don’t use permissive TrustManagers).
- Regularly rotate keys and review all SSL/TLS and crypto code.
More Technical Details & References
- IBM Support Advisory for CVE-2023-30441
- National Vulnerability Database Entry
- IBM X-Force Exchange
- JSSE Reference Guide
Final Thoughts
CVE-2023-30441 is a classic example that security isn’t just about keeping up-to-date, but also about setting things up right. Even strong systems like IBM Java can be undermined by flaws at the intersection of code and configuration.
If you’re running IBM JRE 8..7. to 8..7.11, patch now and review your settings!
Have you found other weird Java bugs? Want to share how you patched this? Let me know in the comments!
Timeline
Published on: 04/29/2023 15:15:00 UTC
Last modified on: 05/09/2023 02:31:00 UTC