When managing critical business data, the last thing you want is a vulnerability that can make your entire database system stop working. Unfortunately, that’s exactly what happened for users of IBM Db2 versions 10.5, 11.1, and 11.5—also including some installations of Db2 Connect Server. Let’s break down CVE-2023-30443, a denial of service (DoS) bug, and learn what it means, how it can be triggered, and what you should do about it.
What is CVE-2023-30443?
CVE-2023-30443 was made public by IBM in May 2023. It’s a security vulnerability that allows an authenticated attacker to crash the database by sending a *specially crafted query*. When exploited, this vulnerability causes the affected Db2 database system to terminate abnormally (that’s how a DoS attack works).
Includes Db2 Connect Server
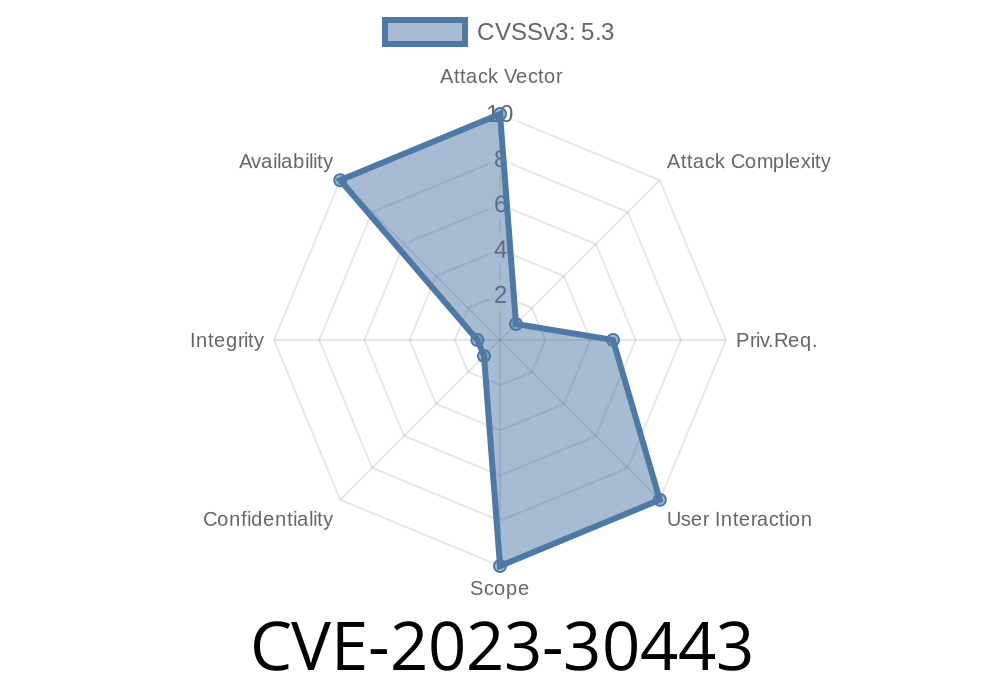
CVSS 3.x Score: 5.9 (Medium)
Attack Vector: Local (the attacker must have credentials)
Why is This Serious?
DoS attacks are a big deal for production systems. While CVE-2023-30443 does not let the attacker steal or modify data, it *does* allow them to stop database operations—potentially bringing down applications or websites relying on Db2.
How Does the Attack Work?
According to IBM’s advisory, the flaw exists in the way Db2 processes certain SQL statements. If a user submits a “specially crafted query,” the database instance can crash, leading to a loss of availability.
While IBM hasn’t published a full proof-of-concept, security researchers often analyze public bug reports and patch notes to identify likely attack vectors. For this case, the key points are:
Elevated privileges not required: Just a regular database user can trigger the bug.
- “Crafted query”: This often means using some character, syntax, or construct the parser or optimizer can't handle correctly.
Example Code Snippet
Below is a simplified (illustrative) version of how a malformed query might look in environments with similar parser bugs. (This is a *conceptual example*—actual attack queries would depend on the exact flaw.)
-- DO NOT RUN ON PRODUCTION SYSTEMS!
-- Sample malformed SQL that could hypothetically exploit the bug
SELECT my_udf(column1), /* UDF: User-Defined Function */
(SELECT COUNT(*) FROM non_existent_table)
FROM huge_table
WHERE (column2 = (SELECT MAX(column2) FROM another_table))
UNION ALL
SELECT REPEAT('A', 100000), (SELECT 1/ FROM sysibm.sysdummy1)
FROM sysibm.sysdummy1;
Generate large strings.
In similar cases, combining edge-case operations like this can sometimes hit a parser bug, cause stack overflows, or trigger fatal engine errors.
## Exploit Details / Steps to Reproduce
Here's a *theoretical* outline of possible attack steps, based on IBM’s description and known database DoS exploitation patterns:
Result: Denial of Service
The database instance crashes or becomes unresponsive, potentially requiring admin intervention to restart.
*Note: Actual exploit queries are not publicly released by IBM for security reasons.*
Mitigation
IBM has released fixes for this vulnerability. You should apply the latest fix packs available for your Db2 version. Patch details and downloads are available here:
- IBM Security Bulletin for CVE-2023-30443
- Db2 Fix Packs & Updates
References
- IBM Security Bulletin: Vulnerability in IBM Db2 (CVE-2023-30443)
- NIST CVE Record for CVE-2023-30443
- Db2 Product Download and Fix Central
Conclusion
CVE-2023-30443 is a classic example of why database software must be kept up-to-date. Even if you think only "hackers" can hurt your data, bugs like these prove all it takes to bring things down is a *quirky* query from a regular user. Patch your Db2 and review your internal account permissions. If you want your database (and applications) to keep running smoothly, don’t let bugs like this sneak up on you.
*Stay secure, stay patched, and monitor your logs!*
Want a deeper dive into the technical analysis once more post-publication info is available? Leave a comment or email us at [your contact info]!
Timeline
Published on: 12/19/2024 01:04:07 UTC